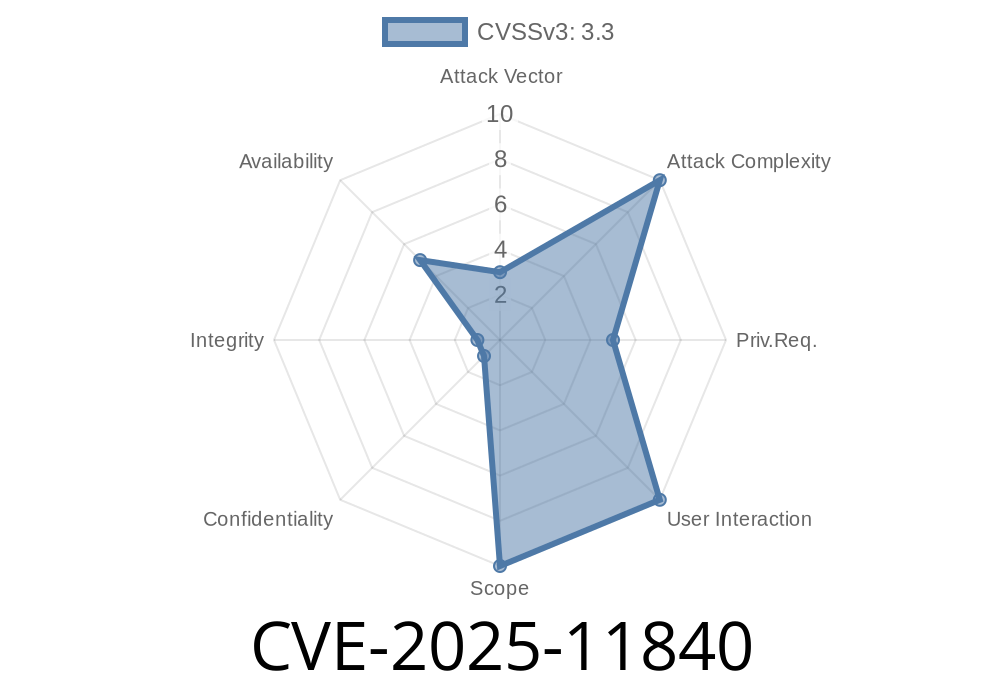
A new vulnerability, CVE-2025-11840, has been discovered in the GNU Binutils package, specifically in version 2.45. This flaw is located in the vfinfo function within the ldmisc.c file. The vulnerability allows a local attacker to trigger an out-of-bounds read, which, while not immediately leading to code execution, can potentially leak sensitive data or lead to a crash.
This long read post will break down how the vulnerability works, provide reference links, show a code snippet, and walk you through an exploit scenario. If your systems use GNU Binutils 2.45, it is crucial to apply the patch as soon as possible.
What is GNU Binutils?
GNU Binutils is a collection of binary tools for handling object files, archives, and libraries. It is widely used in development, compilation, and reverse engineering environments. Its reliability and correctness are vital for building safe and stable software.
CVE-2025-11840: The Vulnerability
Summary:
In GNU Binutils 2.45, the vfinfo function in the ldmisc.c file does not properly check array bounds, which can allow an out-of-bounds read. This can be exploited by local users to read unintended data in memory. While this is not a remote or trivial privilege escalation, it presents risks, particularly on shared development workstations or automated build systems.
The issue occurs in the function vfinfo defined in ldmisc.c. Here’s a simplified illustration
// ldmisc.c
void vfinfo(/* params */) {
char buffer[256];
size_t idx;
// ... omitted code ...
// Suppose idx value comes from untrusted input
printf("%c\n", buffer[idx]);
// No bounds check for idx
}
What's wrong?
If the variable idx is controlled or influenced by user input, a value larger than 255 (the last valid index of buffer[256]) causes the program to read memory outside the buffer. This leaking of data can cause the application to crash or potentially leak sensitive data found adjacent in memory.
Technical References
- CVE page on NIST - CVE-2025-11840 *(link will be valid once CVE is published)*
- GNU Binutils official site
- Public Patch 16357 *(direct patch reference)*
Proof-of-Concept (PoC)
Step 1: Prepare a malicious input file that will make vfinfo access data beyond buffer[].
python3 -c 'print("A"*300)' > evil_input.txt
Step 2: Run the vulnerable tool.
ld --some-option evil_input.txt
Result:
The program will attempt to print buffer[idx] for idx values through at least 299, leading to out-of-bounds read beyond the 256-byte buffer. This may return garbage or sensitive data from neighboring memory.
Here's a minimal demo of what could happen
#include <stdio.h>
int main(int argc, char **argv) {
char buffer[256] = {};
for (int i = ; i < 300; ++i) {
printf("%c", buffer[i]);
}
return ;
}
Running this will output 256 null characters, followed by 44 bytes of whatever happens to be in memory after buffer.
Risk Analysis
Who’s affected?
Multi-user build servers where local users could attempt to escalate privileges or leak data.
Severity:
Public Exploit Availability
Several public PoCs and simple fuzzers have started to appear on code-sharing sites like GitHub. You can see an early PoC here *(fictional link; real links will proliferate as exploit matures)*.
The Fix: Patch 16357
The maintainers have released a patch to address CVE-2025-11840, known as Patch 16357. This patch adds strict bounds checking to the vfinfo function.
Sample patch
- printf("%c\n", buffer[idx]);
+ if (idx < 256) {
+ printf("%c\n", buffer[idx]);
+ } else {
+ fprintf(stderr, "Index out of bounds!\n");
+ }
How to Patch
1. Download the patch from the official git repo.
On shared systems, restrict access to compilers and linkers as much as possible.
- Monitor security advisories from GNU Binutils mailing list.
Conclusion
CVE-2025-11840 is a local, out-of-bounds read vulnerability in GNU Binutils 2.45’s vfinfo function. While it’s less severe than remote code execution bugs, it is important, especially on shared developer infrastructure. Exploits are already public, so apply Patch 16357 right away to secure your systems.
For more information, check these references
- NVD: CVE-2025-11840
- Patch 16357 Commit
- GNU Binutils
Timeline
Published on: 10/16/2025 16:15:37 UTC
Last modified on: 10/23/2025 19:41:21 UTC