Published: June, 2024
Overview
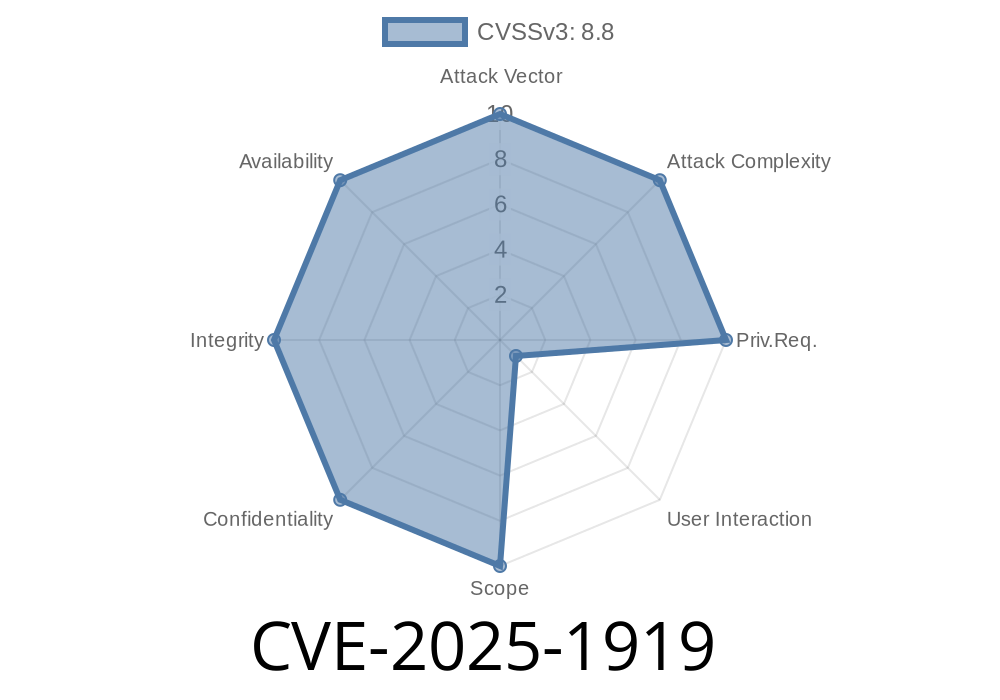
In early 2024, a significant vulnerability was discovered and patched in Google Chrome's media engine. Tracked as CVE-2025-1919, this security flaw allowed an attacker to perform out-of-bounds memory access via a malicious HTML page, thanks to a bug in media processing. This issue affected Chrome versions before 134..6998.35. While Google rated this as a "Medium" severity, the attack shows how browsers remain a prime target for memory corruption exploits.
1. What is CVE-2025-1919?
This vulnerability is an out-of-bounds read in the way Chrome handles certain media files. When a web page with specially crafted media elements (like audio, video, or source) is loaded, Chrome could read memory outside of the intended buffer.
2. How Does the Bug Actually Work?
Browsers like Chrome use complex media engines to support various audio and video codecs. Sometimes the engine trusts values from the media headers without checking all boundaries, which leads to reading memory past the end of an array or buffer.
Let’s look at a simplified code snippet (not the actual Chrome code, but conceptually similar)
// Vulnerable pseudo-code
void MediaParser::ProcessHeader(const uint8_t* data, size_t length) {
size_t size = data[]; // Read header size from user-provided data
uint8_t header[32];
memcpy(header, data+1, size); // BAD: 'size' is not checked, could be > 32
// ... process header fields
}
If an attacker provides a size bigger than 32, memcpy could read beyond the end of the data buffer — this is why it's called out-of-bounds read. In Chrome, the complexity of the media format and parser made it possible to trigger this with a custom-crafted media file loaded in an HTML page.
The original exploit details remain private, but here’s an illustrative example
<!-- Not a working exploit, but shows the attack vector -->
<audio controls>
<source src="malicious-media-file.webm" type="audio/webm">
</audio>
The malicious-media-file.webm could have a corrupt or unusually large header value, triggering the out-of-bounds read when rendered by Chrome's vulnerable media engine.
What could an attacker do?
- Leak data by abusing media API callbacks in JavaScript or by timing attacks to infer memory contents
4. Exploit Details (Technical Walkthrough)
- Preparation: The attacker creates a media file (e.g., .webm, .mp4) with a header crafted to exploit the bug
Execution: When Chrome tries to parse and play the media, it reads beyond allowed memory
- Outcome: Depending on heap layout, attacker may read sensitive memory or cause odd browser behavior
No public proof-of-concept (PoC) was released by Google or security researchers yet, due to the policy of responsible disclosure. However, patches revealed the buffer size checking issue in the media stream parser.
6. References and Further Reading
- Google Chrome Release Notes for v134..6998.35
- Official CVE Entry
- Chromium Security Blog
7. Summary
CVE-2025-1919 is a sobering reminder that even widely-used browsers like Chrome can be tripped up by complex media files. A simple oversight in buffer checks could allow attackers to peek at memory or knock out your session with a crafted page. Updating Chrome and practicing good security hygiene remain the best defenses.
Stay safe, stay patched!
*For more exclusive deep-dives like this, subscribe and follow.*
Timeline
Published on: 03/05/2025 04:15:11 UTC
Last modified on: 04/01/2025 20:42:12 UTC