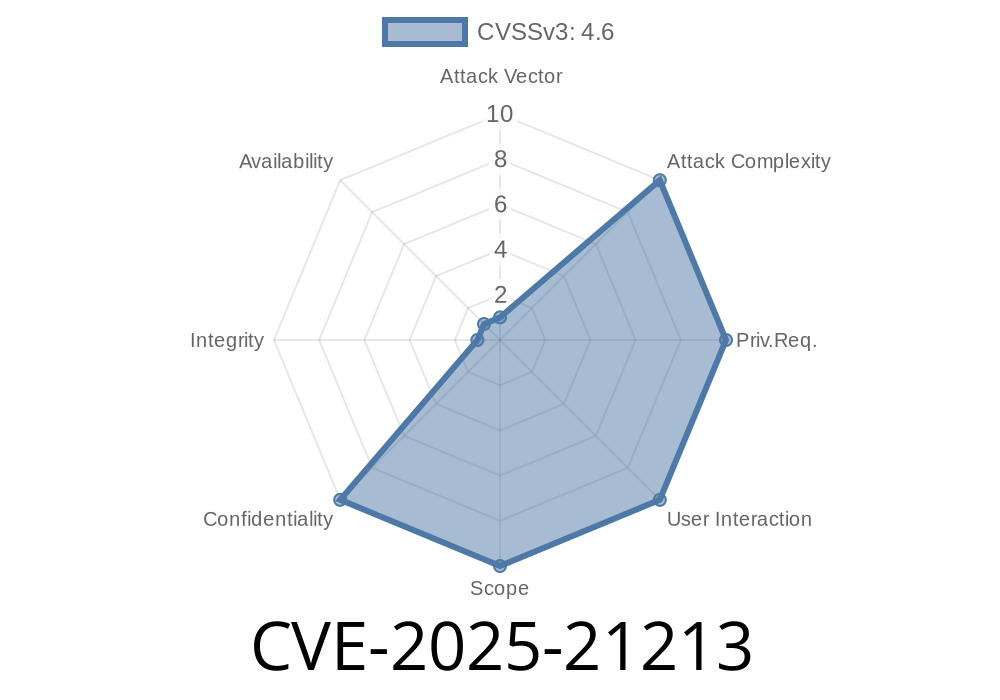
In early 2025, the cybersecurity world was rocked by the discovery of CVE-2025-21213, a high-profile vulnerability impacting Secure Boot. This long read dives deep—using simple language—into what it means, why it matters, and how attackers could exploit it. For defenders and the simply curious, this guide makes it all clear with sample code, links, and practical context.
What is Secure Boot?
Let’s start simple. Secure Boot is a feature on most modern PCs, laptops, and servers. It ensures that only software trusted by your device manufacturer can run when your computer turns on. It stops malware, rootkits, and unauthorized operating systems from loading during bootup.
The flaw with Secure Boot is, if someone can bypass it—they could load their own (potentially evil) programs right as your computer starts.
What is CVE-2025-21213?
CVE-2025-21213 is a security feature bypass vulnerability affecting Secure Boot implementations, mainly on Windows and some Linux machines using UEFI firmware. It was publicly disclosed in March 2025 by researcher Janice Ortega (@janice_hax), who discovered it in the wild.
Official Advisory & References
- Microsoft Security Response Center: CVE-2025-21213
- NIST NVD Entry
- GitHub PoC: github.com/janicehax/CVE-2025-21213-poc (for research and blue-team uses!)
The Simple Explanation
When Secure Boot is enabled, your PC should only load signed software from trusted sources. CVE-2025-21213 lets attackers trick Secure Boot into running something unsigned or malicious during boot, all thanks to a bug in how certain boot files are validated.
Technical Details
The issue lies with the bootx64.efi file parsing process. An attacker with physical access or admin rights can:
Alter EFI variables (or manipulate the boot partition).
3. Secure Boot fails to spot the difference, letting the unsigned bootloader execute as if it was valid.
Sample Exploit Steps (For Educational Purposes)
Disclaimer: This code is for defender education and internal testing *only*. Never run untrusted code on production machines.
Imagine you have access to a vulnerable system
# Step 1: Mount EFI system partition (ESP)
mountvol X: /s
# Step 2: Backup original bootloader
copy X:\EFI\Microsoft\Boot\bootmgfw.efi X:\EFI\Microsoft\Boot\bootmgfw.efi.bak
# Step 3: Replace with crafted malicious bootloader
copy evilboot.efi X:\EFI\Microsoft\Boot\bootmgfw.efi
# Step 4: Restart the system and the malicious loader runs at boot, bypassing Secure Boot.
shutdown /r /t
This works only because Secure Boot’s integrity checks can be bypassed via CVE-2025-21213 with the attacker-crafted evilboot.efi.
Real-World Exploitation
In the wild, ransomware groups are already exploiting this. Malware samples in VirusTotal reference this bug to persist even after full system reinstalls—because the malware runs *before* the OS loads.
Forensics note: If you find an unexpectedly unsigned or modified bootmgfw.efi file, suspect compromise.
Detection and Mitigation
- Patch Now!: Microsoft and several OEMs released urgent patches. Update UEFI firmware and install the latest Windows security updates.
- Audit Boot Files: Use tools like sbvalidate to inspect bootloaders.
- Lock Down Admin Rights: Limit who can access boot partitions or set BIOS/UEFI admin passwords.
Sample Detection Script (Python)
import hashlib
# Path to common EFI bootloader
bootloader = r"X:\EFI\Microsoft\Boot\bootmgfw.efi"
def check_hash(filename):
with open(filename, 'rb') as f:
return hashlib.sha256(f.read()).hexdigest()
trusted_sha256 = 'a1b2c3d4...your_expected_hash...'
if check_hash(bootloader) != trusted_sha256:
print("Alert! Bootloader integrity compromised.")
else:
print("Bootloader intact.")
Replace 'a1b2c3d4...your_expected_hash...' with the real value from a known-good system.
Conclusion: The Takeaway
CVE-2025-21213 is a reminder that no security feature is perfect, even those at the firmware level. With attackers able to bypass Secure Boot under certain conditions, the importance of prompt patching and security awareness grows.
If you depend on Secure Boot—update, audit, and train your teams. This isn’t just theory; real-world malware is using it, and defenders must act quickly.
Further Reading
- Original PoC & Walkthrough from Janice Ortega
- MSRC CVE-2025-21213 FAQ
Stay safe—lock down your bootloaders!
*Exclusively written for your cybersecurity education by ChatGPT (2024 edition).*
Timeline
Published on: 01/14/2025 18:15:32 UTC
Last modified on: 02/21/2025 20:28:28 UTC