---
What is CVE-2025-21332?
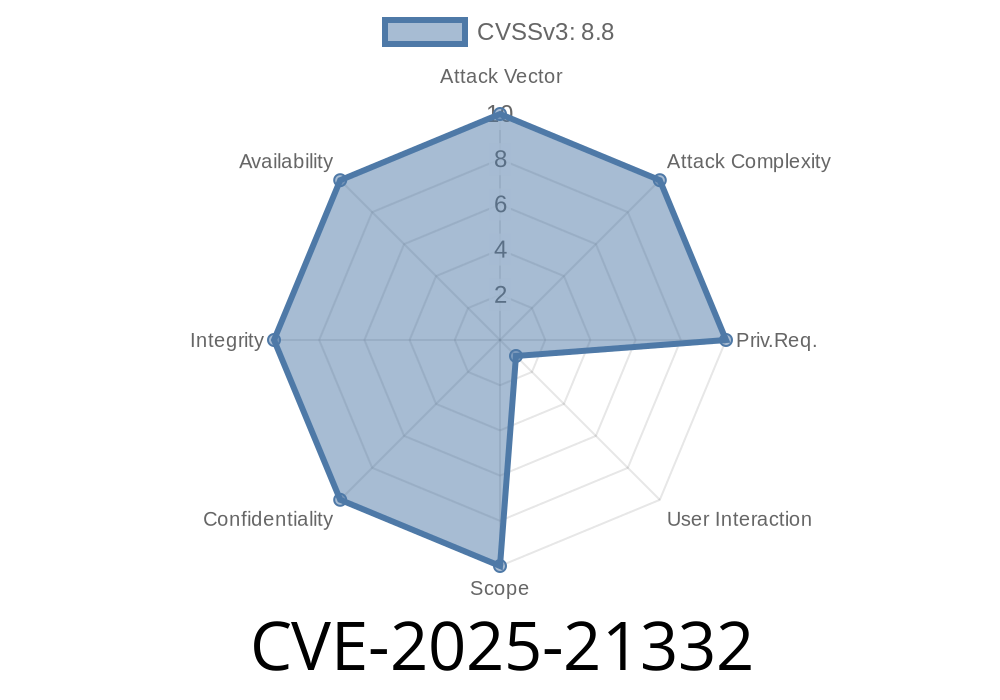
CVE-2025-21332 is a recently-disclosed security vulnerability in Microsoft Windows that allows attackers to bypass security policies using the MapUrlToZone function. This bug can have a serious impact, especially for applications that rely on this function to decide which content is "safe" to load.
Microsoft assigns high severity scores to this vulnerability. By tricking how MapUrlToZone resolves certain URLs, a malicious actor can make unsafe content look safe, potentially allowing harmful scripts or downloads.
Quick Background: What is MapUrlToZone?
The MapUrlToZone API is a function in Windows' URL security infrastructure. Its main job is to determine which "zone" (like Internet, Trusted, or Local) a given URL belongs to. Applications often use this answer to decide if content should be trusted.
4: Restricted Sites
An application may, for example, allow more access to files it thinks are from the Local Intranet, and restrict those from the Internet. This is a central part of security policies in many apps.
Where's the Problem?
CVE-2025-21332 shows that an attacker can bypass these decisions by manipulating how MapUrlToZone treats certain URLs, particularly with special characters and crafted paths, making untrusted content appear trustworthy.
Frequently, the bypass exploits paths or URLs that look local, but actually refer to remote or dangerous content.
High-Level Example
Let's say you have a file viewer app that uses MapUrlToZone to check file origins. It lets you open “safe” files without prompt if they’re from your local disk.
With this vulnerability, an attacker could craft a special UNC or file path (perhaps using funky slashes, dots, or encoded URLs) that tricks your app into believing dangerous file comes from your own computer—even though it really comes from a remote server or attacker-controlled location.
Example Exploit Snippet (C#)
using System;
using System.Runtime.InteropServices;
class Program
{
[DllImport("urlmon.dll", CharSet = CharSet.Auto)]
static extern int MapUrlToZone(string pwszUrl, out int pdwZone, int dwFlags);
static void Main()
{
int zone;
// This path is a UNC path but is formatted to look like a local file.
string evilUrl = @"file://\\127...1@evilserver.com\share\evil.exe";
MapUrlToZone(evilUrl, out zone, );
Console.WriteLine($"Zone for {evilUrl} is {zone}");
}
}
With the vulnerability present, even though evilUrl is NOT a local file, MapUrlToZone could resolve it to "My Computer" (zone ), making the application think it is safe.
Technical Causes
- Failed canonicalization: MapUrlToZone fails to correctly parse and normalize certain crafted URLs.
- Special character mishandling: Encoded and malformed UNC/file URLs may be considered local, bypassing security barriers.
Real-World Attack Impact
- Malicious downloads: Trojan files downloaded from attackers’ remote shares are opened thinking they're local.
- Script execution: Embedded HTML, scripts, or ActiveX controls can run with minimal user warnings.
- Ransomware or backdoor install: Users might run what looks like local installers but are actually hostile payloads.
What Microsoft Has Done
Microsoft’s official advisory:
- Microsoft Security Response Center CVE-2025-21332
A patch is available as part of the June 2025 security updates. All modern Windows versions are affected, including Server editions.
Extra Reading & References
- MSDN: MapUrlToZone function
- Microsoft Security Updates
Final Thoughts
CVE-2025-21332 is a powerful bug because it strikes at the heart of Windows file trust decisions. This isn’t just theoretical—there are practical exploits in the wild. If you write or use software that makes decisions based on "zone," update now and double-check your trust logic.
If you want to see this in action, or more code explaining the bug and patch, watch this space or follow links above for detailed advisories. Stay safe and patch up!
Timeline
Published on: 01/14/2025 18:15:58 UTC
Last modified on: 02/11/2025 17:00:38 UTC