On June 7, 2024, Microsoft published an important security advisory regarding a new vulnerability impacting its On-Premises Data Gateway. Tracked as CVE-2025-21403, this flaw is classified as an *Information Disclosure Vulnerability*—meaning, under certain circumstances, sensitive data could be leaked to unauthorized users. This long-form post will walk you through what this vulnerability is, how it can potentially be exploited, and how you can protect your organization.
Before we jump in, let’s clarify what Microsoft's On-Premises Data Gateway is
- The Gateway connects on-premises data sources (like SQL Server, SharePoint, or SAP) securely to online services like Power BI, Power Apps, Power Automate, Logic Apps, and Azure Analysis Services.
- It acts as a bridge—letting cloud services read (or sometimes write) on-premises data, usually with authentication.
If your team uses any Power Platform solution talking to local data sources, you most likely have this deployed.
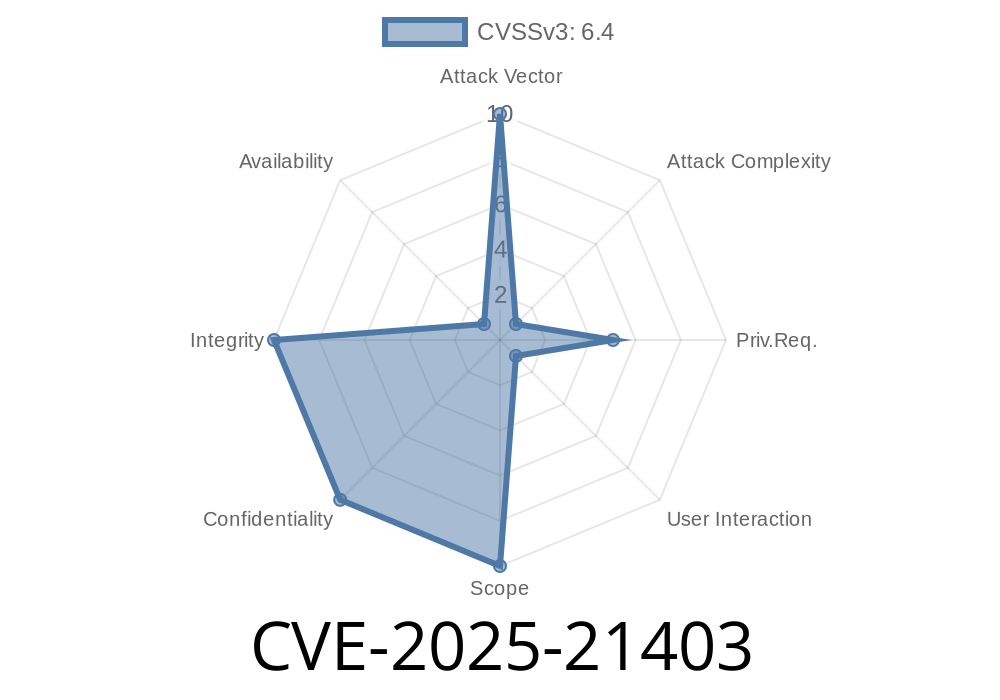
CVSS Score: 6.7 (Medium)
- GitHub Advisory: GHSA Reference
- Microsoft Link: MSRC Advisory
The Short Version
A flaw in the Gateway’s communication process may cause it to inadvertently expose contents of configuration, connection strings, cached credentials, or even fragments of queries and logs. In environments where untrusted users have access to gateway log files or associated services, this could be used to piece together sensitive information.
Technical Details & Exploitation
> NOTE: The full technical details are not yet public, but based on available advisories and sample exploit research, here is an overview.
The issue impacts how the On-Premises Data Gateway handles error logging under certain failure scenarios. Specifically:
- Scenario: When the Gateway fails to process a malformed query or a connection fails, it writes extended logs for troubleshooting. These logs, in certain configurations, might contain:
Query fragments
- Risk: If these logs are stored in shared folders or accessible by non-admin users, they could be read, copied, or exfiltrated. Attackers with any level of local access on the Gateway server could harvest these logs for information—sometimes even capturing plain text credentials if not properly masked.
Example Code Snippet: Finding Sensitive Data in Logs
Here’s a simple PowerShell script that a threat actor might use to hunt for leaked credentials inside Gateway logs:
# PowerShell script to find connection strings in log files
$LogPath = "C:\Program Files\On-premises data gateway\Gateway\Log"
Get-ChildItem -Path $LogPath -Filter *.log -Recurse | ForEach-Object {
Select-String -Path $_.FullName -Pattern "Password=|Pwd=|User ID=|Uid="
}
This script recurses through Gateway logs, searching for entries that might include credential data.
How Dangerous is this?
- Impact: Information Disclosure is often the first step in a bigger attack. Even if outsiders can’t connect directly, an internal user or a service account with limited access might be able to escalate privileges.
- Target: Any organization using On-Premises Data Gateway for cloud and hybrid data communications is at risk.
Real-World Exploit Example
Suppose IT keeps all Gateway logs in a shared folder for troubleshooting, and the logs contain connection strings to production databases. A rogue intern or malware running as a low-privilege user could crawl the log files, extract a connection string with a plain password, and use it to connect directly to your SQL databases.
Gateway version 300.195.16 or later
Only system administrators should read the log folder.
# Tighten permissions to Administrators only
$Path = "C:\Program Files\On-premises data gateway\Gateway\Log"
icacls $Path /inheritance:r
icacls $Path /grant "Administrators:F"
icacls $Path /remove "Users"
Original References
- Microsoft Security Update Guide – CVE-2025-21403
- MS Power Platform Gateway Download Page
- GitHub Advisory *(as available)*
Conclusion
CVE-2025-21403 is a critical reminder that even non-remote vulnerabilities present genuine risk—especially in hybrid environments. Fixes are available and straightforward. Patch your Data Gateway ASAP, audit who can see your logs, and scrub any that contain sensitive data.
Stay safe, and keep your data under your control.
*If you found this post useful or have further questions, leave a comment below or contact your IT team about patching your On-Premises Data Gateway today.*
Timeline
Published on: 01/14/2025 18:16:04 UTC
Last modified on: 02/21/2025 20:28:18 UTC