A newly disclosed vulnerability, CVE-2025-21502, impacts multiple versions of Oracle's Java SE and its GraalVM products. While exploitation is tricky, the flaw opens the door to sensitive data access and manipulation by attackers – even when they're not authenticated. In this article, we’ll break down what CVE-2025-21502 is, how it works, which products and versions are affected, and what this could mean for organizations relying on these platforms.
What Is CVE-2025-21502?
CVE-2025-21502 is a vulnerability publicly acknowledged in the Oracle Critical Patch Update Advisory (see NVD entry for CVE-2025-21502), affecting core components within Oracle Java SE, GraalVM for JDK, and GraalVM Enterprise. This vulnerability resides in the HotSpot component, which is the heart of Java’s runtime environment responsible for memory management and executing Java bytecode.
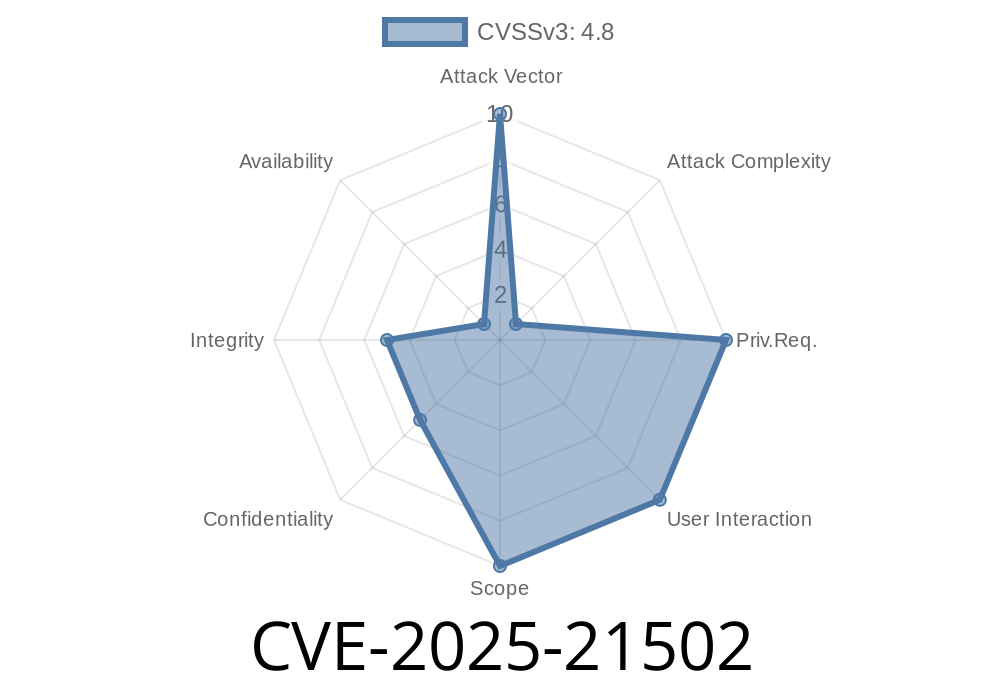
CVSS Details
- Base Score: 4.8 (CVSS:3.1/AV:N/AC:H/PR:N/UI:N/S:U/C:L/I:L/A:N)
Oracle GraalVM Enterprise Edition: 20.3.16, 21.3.12
If you’re running any products using these versions, you’re potentially at risk.
How Could This Be Abused?
The flaw exists in the HotSpot internals, specifically exposed via public-facing APIs. If an attacker can get their (untrusted) data into a Java process—commonly through web services, REST APIs, or even RMI—maliciously crafted inputs can trigger the vulnerability.
Read: Access a subset of internal Java data that should have been confidential.
- Update/Insert/Delete: Manipulate some Java objects in memory, risking integrity of data handled by the Java VM.
This could, for example, allow modification of application state, exposure of user session data, or even tampering with runtime class or object variables.
Example Scenario
Let’s imagine a microservices-based enterprise app running on Java 17. It exposes a JSON API to the outside world:
@RestController
public class DataEndpoint {
@PostMapping("/api/data")
public String process(@RequestBody Map<String, Object> input) {
// Untrusted input parsed and used
SomeService.handle(input);
return "OK";
}
}
If the vulnerable HotSpot logic is triggered by specific crafted data structures, an attacker could submit a request that alters internal Java objects, such as:
{
"maliciousKey": {
"class": "some.internal.Class",
"data": "... crafted payload ..."
}
}
This is a very generic example, but the point is: if untrusted data reaches affected Java API endpoints—directly or indirectly—there is a real risk.
Proof-of-Concept (Pseudo-Exploit)
Due to the high risk and difficulty of exploitation, a complete public exploit isn't available. However, a typical exploitation chain would resemble:
// Attacker submits malicious Java serialized object to endpoint:
byte[] maliciousBytes = /* crafted serialized payload */;
// Vulnerable deserialization path:
ObjectInputStream ois = new ObjectInputStream(new ByteArrayInputStream(maliciousBytes));
Object obj = ois.readObject(); // Triggers flaw in HotSpot via crafted class metadata.
Note: The exploit requires a deep understanding of both HotSpot internal memory layout and how Java deserialization interacts with it, often leveraging gadgets present in specific environments.
Mitigation & Recommendations
1. Patch Immediately:
Oracle's Critical Patch Update Advisory recommends upgrading to the latest secure Java SE and GraalVM releases.
2. Minimize Attack Surface:
Do not expose Java endpoints to untrusted sources unless strictly necessary. Avoid accepting serialized objects or generic structures from clients.
3. Use Input Validation:
Strictly validate and sanitize data from all network sources, especially JSON/XML input that gets mapped to Java objects.
4. Monitor for Suspicious Activity:
Enable logging and anomaly detection for your Java applications, watching for unusual access patterns or payloads.
Further References
- Oracle Security Advisory – April 2024
- NVD CVE-2025-21502
- Oracle Java SE Downloads
- GraalVM Community Releases
Summary
CVE-2025-21502 is a subtle but serious vulnerability. Its impact—though limited by difficulty of exploitation—is broad, allowing insiders or remote attackers to bypass Java sandbox boundaries and tamper with data processed by Java SE and GraalVM platforms. The best defense is keeping your Java runtime up-to-date, applying patches quickly, and never trusting unchecked user input.
*Stay safe, patch fast, and keep your JVMs healthy!*
Timeline
Published on: 01/21/2025 21:15:15 UTC
Last modified on: 01/31/2025 16:15:35 UTC