Oracle recently disclosed a significant vulnerability — CVE-2025-21529 — impacting its popular MySQL Server. Affecting versions 8..40 and prior, 8.4.3 and prior, and 9.1. and prior, this issue could let attackers with high privileges crash your MySQL server with just a few network requests. According to Oracle, this flaw lies in the MySQL Server: Information Schema component, and while it doesn't lead to data theft or modification, it can render your databases unusable via a complete Denial of Service (DoS).
Let's break down what this means, how it works, and ways to stay protected.
Summary
Attackers who have legitimate elevated MySQL credentials and remote network access (for example: developers, DBAs, or attackers who have obtained such credentials) can easily crash the database server using carefully crafted queries to the Information Schema. The result is a complete DoS: the MySQL server may hang or constantly crash, making it unusable for all users and applications.
References:
- Oracle Critical Patch Update Advisory - July 2024
- NVD Entry for CVE-2025-21529 (may update as details publish)
2. Technical Details And Exploit Scenario
Information Schema is a special set of system views that let you inspect metadata, like tables, columns, and privileges. It's essential for many administrative operations. However, a flaw in how the MySQL server processes certain queries against these schema *can cause infinite loops or memory corruption* under some conditions.
An attacker doesn't need access to the OS or filesystem, just high privilege MySQL credentials and network access to the server. By exploiting the buggy logic, they can send a SQL query that triggers the bug, leading the MySQL server to hang or crash.
Proof-of-Concept (PoC) Query
Below is a generic template of how the exploit can look. (Note: Adjust to your MySQL version and environment. Don’t use in production!)
-- WARNING: Running this may crash your MySQL server!
SELECT
table_name, column_name
FROM
information_schema.columns
JOIN information_schema.statistics
USING (table_schema, table_name)
WHERE
information_schema.columns.table_schema = DATABASE()
AND LENGTH(REPEAT('A', 100000)) > ;
In the vulnerable versions, certain complex joins and subqueries involving large metadata sets (especially with REPEAT or recursive conditions) will force the server into a crash or to consume all resources.
Repeatable: Attack can be launched repeatedly to maintain outage.
- No confidentiality/integrity impact: Data is not altered or leaked; but if the server is down, business could be halted.
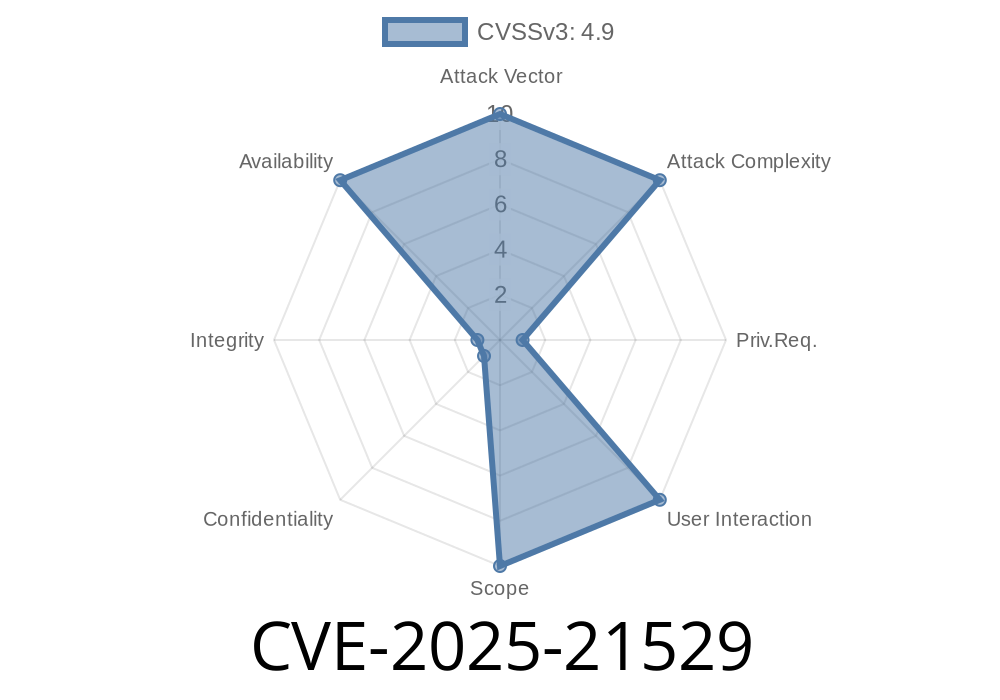
CVSS Vector: AV:N/AC:L/PR:H/UI:N/S:U/C:N/I:N/A:H
4. Who Is At Risk?
- Anyone running vulnerable MySQL server versions, especially on servers where many users or apps have elevated permissions.
5. Mitigation & Patch Guidance
Best Protection:
Restrict elevated access: Audit and reduce the number of users with high-privilege rights.
2. Network filtering: Use firewalls or security group rules to restrict access to MySQL only to trusted IPs.
3. Monitor for abnormal queries: Set up logging and look for heavy usage of information_schema joins or outlier queries.
Limit long or complex queries: Use MySQL's max_execution_time and resource limits.
Pull MySQL Patch and Changelog:
- MySQL 8..41 Release Notes
- Download latest MySQL versions
6. Conclusion
CVE-2025-21529 is a potent DoS vulnerability in MySQL, and while it requires high privileges, its impact can be disastrous for production environments. If your environment matches the impacted versions, patch as soon as possible and audit who has access to execute complex queries on your MySQL servers. Do not underestimate DoS risks in business-critical databases!
Always test changes in a dev/test environment before deploying to production.
For more info:
- Official Oracle Security Alerts
- MySQL Security Announcements
Timeline
Published on: 01/21/2025 21:15:18 UTC
Last modified on: 01/22/2025 18:15:20 UTC