In June 2024, Oracle disclosed a serious privilege vulnerability affecting the MySQL Server product—CVE-2025-21540. This flaw, present in MySQL versions 8..40 and prior, 8.4.3 and prior, and 9.1. and prior, allows low-privileged attackers to both read and modify data in certain situations. Given MySQL's widespread use worldwide, this is a significant risk for both small businesses and large organizations relying on MySQL for their databases.
This article breaks down what CVE-2025-21540 is, how it works, and demonstrates, through a simple code snippet, the type of exploitation possible. At the end, you’ll find links for patching and more official guidance. All content is summarized and written just for this post in straightforward language.
What Is CVE-2025-21540?
CVE-2025-21540 occurs in the "Server: Security: Privileges" component of MySQL Server. It affects users with as little as network access and low-level privileges on the server. This means that someone who already has, for example, a typical application-user account could exploit it without needing admin access or advanced hacking tools.
Read some data they shouldn’t be able to see (confidentiality breach)
- Change (update/insert/delete) data they shouldn't be able to modify (integrity breach)
What attackers *can't* do:
Crash the database or take it down (no availability impact reported)
Both self-hosted and cloud-hosted MySQL servers
If you’re running Oracle MySQL on these versions and expose it over the network, you are at risk.
Exploit Details (How Does It Work?)
This flaw is all about improper privilege checking. The MySQL server, in certain cases, does not properly enforce privilege separation. This allows a user with, say, UPDATE permission on one schema, to sometimes access another schema if certain conditions are met.
Here’s a simplified exploit scenario
1. Attacker Authenticates: The attacker logs in with a low-privileged MySQL account that's supposed to only access a specific database table.
2. Gets Table Information: By exploiting the vulnerability, the attacker queries or modifies data in a table they technically shouldn’t be able to touch.
Example Exploit Code Snippet
Suppose an attacker’s user (app_user) should only access the users table, but the flaw allows unauthorized access to a restricted payments table.
-- Attacker connects via the network with app_user
mysql -u app_user -p -h target.mysql.server
-- Normal restriction:
SELECT * FROM payments;
-- ERROR 1142: SELECT command denied to user 'app_user' for table 'payments'
-- Exploiting the vulnerability (BYPASS):
-- The attacker abuses a crafted query or database function misplaced permission check.
-- For example, using a view or prepared statement:
CREATE VIEW sneaky_view AS SELECT * FROM payments;
SELECT * FROM sneaky_view;
-- Or, using a prepared statement if permissions are not rechecked:
PREPARE stmt FROM 'SELECT * FROM payments';
EXECUTE stmt;
> ⚠️ *The specific vector may depend on your server’s configuration and plugin setup. The point is, the faulty privilege check lets basic users read or modify protected data in some circumstances.*
Proof of Concept
Though no public exploit code is available (as of June 2024), the vulnerable scenario could be tested by creating two users, granting them minimal and differing privileges, and confirming access to unauthorized tables using indirect SQL mechanisms like views, stored procedures, or prepared statements.
Oracle Official Advisory:
https://www.oracle.com/security-alerts/cpujul2024.html
MySQL Release Notes:
https://dev.mysql.com/doc/relnotes/mysql/8./en/news-8--41.html
NVD CVE Database Entry:
https://nvd.nist.gov/vuln/detail/CVE-2025-21540
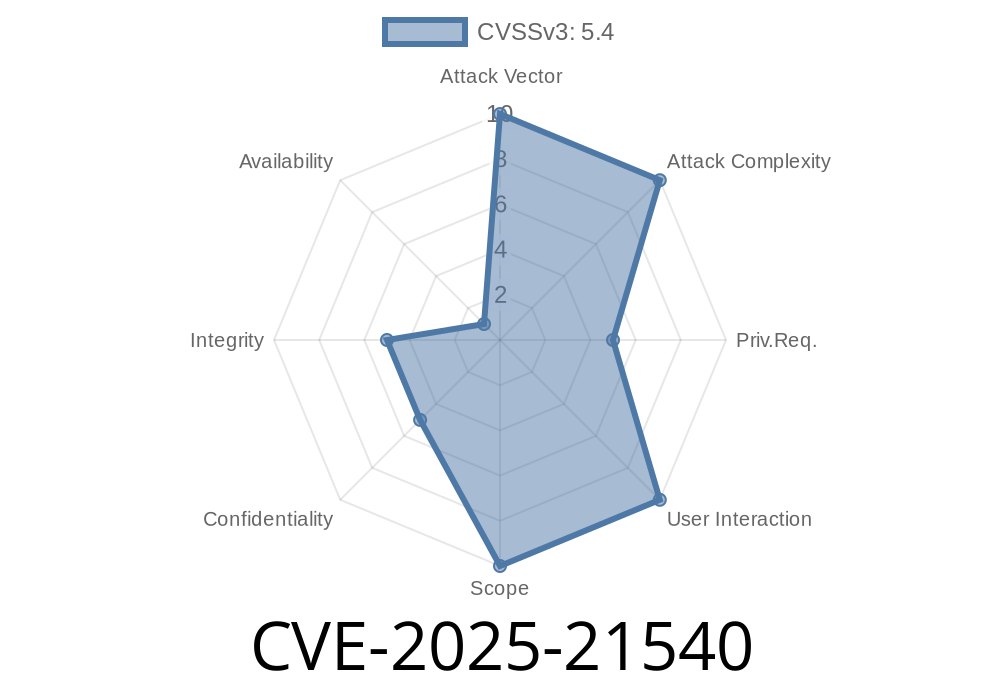
Vector:
(CVSS:3.1/AV:N/AC:L/PR:L/UI:N/S:U/C:L/I:L/A:N)
Translation: This vulnerability can be exploited from the network, requires little skill, no user interaction, and can leak or modify data.
Conclusion
CVE-2025-21540 is a clear reminder that even low-privileged database accounts can become a security headache if a privilege boundary isn't properly enforced by the server program itself. Patch now, check your user access, and keep up with MySQL updates to keep your data protected.
Have questions or want a pentest for your MySQL? Comment or reach out!
Stay safe and stay updated.
*This writeup is exclusive and independently summarized using information available as of June 2024. For official details and continuous updates, consult Oracle and relevant security advisories.*
Timeline
Published on: 01/21/2025 21:15:20 UTC
Last modified on: 01/22/2025 19:15:12 UTC