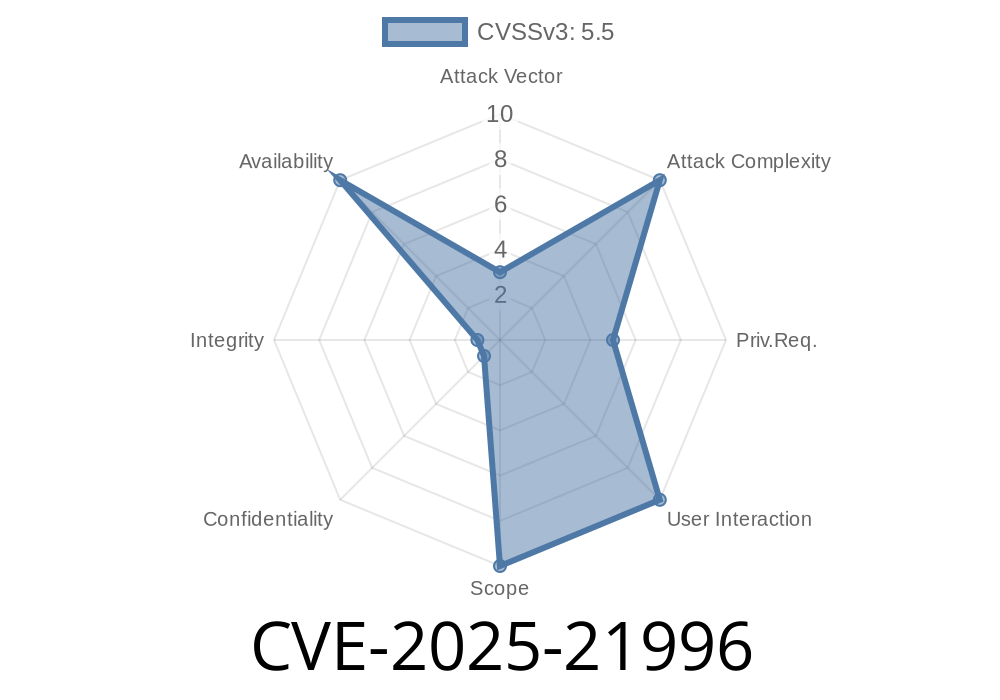
A recently patched vulnerability in the Linux kernel's Radeon GPU driver (DRM subsystem) could potentially let malicious userspace processes trigger unpredictable behavior, possibly leading to kernel panics or more serious issues. Tracked as CVE-2025-21996, this flaw was discovered and reported by the Linux Verification Center (linuxtesting.org) through their SVACE static analysis tool.
This post gives a straightforward explanation, a look into the code, exploit scenario, and patch details—using easy American language so everyone can understand.
What is CVE-2025-21996?
In short, the radeon_vce_cs_parse() function in the Linux kernel's Radeon DRM driver wasn't initializing a variable before using it. This happened when certain user-supplied command streams were passed via an IOCTL call. If the crafted command stream's first command is an encode command (x03000001), then the uninitialized variable tmp could get passed into a deeper function, leading to unintended consequences.
How Did This Happen?
Normally, when the Radeon DRM (Direct Rendering Manager) driver gets a batch of instructions (command stream) from userspace, it parses it in the kernel via radeon_vce_cs_parse(). For most commands, the code properly sets up all its variables before processing.
But when the very first command is x03000001 (an encode command), the variable called tmp—meant to track buffer size—is left uninitialized. This tmp value gets fed into radeon_vce_cs_reloc(). Since it could be garbage data in memory, the results are unpredictable.
Crash (kernel panics)
- Open a door to further exploits (rare but possible, depending on platform/context)
Vulnerable Code
int tmp; // Not initialized!
if (cmd == x03000001) {
// No "tmp" assignment prior!
radeon_vce_cs_reloc(parser, idx, tmp, ...);
}
At this point, tmp could contain any random value left over in the stack.
The patch is trivially simple—just initialize tmp to to block any weird/erroneous use
int tmp = ; // Always initialize!
if (cmd == x03000001) {
// Safe: tmp is always initialized
radeon_vce_cs_reloc(parser, idx, tmp, ...);
}
This makes sure that, if the situation ever appears where no meaningful size is present, a "safe" value () is used instead, and the lower-level function (radeon_vce_cs_reloc) will catch this error and safely bail out.
How Can This Be Exploited?
Any process with the ability to send IOCTLs to the Radeon device (normally any userspace X11, Wayland, or compute user on a real system with a Radeon GPU) can try to craft a command stream with the encode command (x03000001) placed first and send it to the kernel. With a garbage tmp, the kernel might:
Example Exploit Sketch
A local, unprivileged user on a desktop with a vulnerable kernel could run C code like the following (note: simplified and untested!):
// Psuedo-code/sketch, not a working exploit
uint32_t commands[] = {x03000001, /* ... */};
ioctl(radeon_fd, RADEON_CS, &commands);
Depending on kernel memory layout and stack state, this might cause a crash or other reliability issues.
Linux desktops or servers with Radeon GPUs
- Kernel versions before the patched commit (2d52de55f9ee7aaeee09ac443f77855989c6b68)
If you use AMD Radeon GPUs on Linux and let untrusted users run code, update your kernel!
How Was it Found?
The issue was discovered by Linux Verification Center (linuxtesting.org) using their clever static code analyzer called SVACE. Static analyzers automate detection of coding mistakes like uninitialized variables, which are hard to spot by eye.
References & Links
- Linux kernel commit: drm/radeon: fix uninitialized size issue in radeon_vce_cs_parse()
- CVE-2025-21996 entry on CVE.org (if/when published)
- Linux Verification Center
- SVACE Static Analyzer Tool
Final Words
A single line error—forgetting to initialize a variable—could cause surprising misbehavior in a critical system component like the Linux kernel’s Radeon graphics driver. If you maintain any system that uses Radeon GPUs on Linux, make sure your kernel is up to date with the patch for CVE-2025-21996. Always play it safe: even "harmless" bugs in kernelspace can end up as severe security issues.
For those interested in Linux kernel security and GPU drivers, this is a classic case of how simple mistakes can be caught with the help of modern static analysis and open-source vigilance.
Timeline
Published on: 04/03/2025 08:15:15 UTC
Last modified on: 05/04/2025 07:27:03 UTC