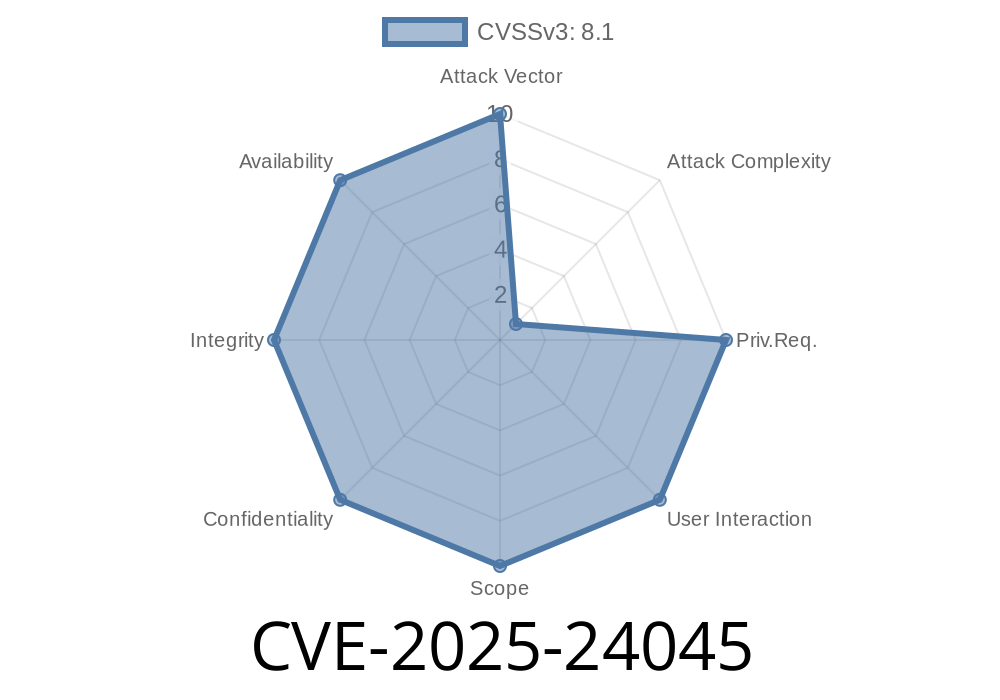
In 2025, security researchers discovered CVE-2025-24045 – a serious vulnerability in Windows Remote Desktop Services (RDS). This flaw exposes sensitive data by storing it in memory that is not properly locked, allowing attackers to execute code remotely over the network. Below, we’ll dig into how this works, what makes it dangerous, provide code snippets to help understand the issue, and link to the original advisories.
What is CVE-2025-24045?
This CVE identifies a case where Windows RDS stores sensitive data (like credentials or tokens) in memory blocks that are not securely locked. That means an unauthorized attacker can access or overwrite this memory, and potentially execute malicious code.
Affected software:
Remote Desktop Services (RDS)
Type of vulnerability:
Improper memory protection (a kind of “infoleak” and privilege escalation)
Attack vector:
How Does the Exploit Work?
Normally, RDS should use Windows functions like VirtualLock() to “lock” sensitive memory, making sure it’s not swapped to disk or accessed by unauthorized processes.
In CVE-2025-24045, RDS fails to do this in certain data flows. For example, when handling connection requests or session reopening, temporary buffers with authentication tokens can be accessed before they are properly ‘cleared’ and locked. An attacker who can send specifically crafted requests can read or overwrite those buffers.
Sends a specially crafted request to force RDS to allocate sensitive data in memory.
3. Leverages a race condition to trigger an infoleak or code execution, exploiting the window when the memory isn’t locked.
4. Remote code execution happens if the attacker sends payload data to overwrite function pointers or other control structures.
Here's a simplified pseudo-code example to show the problem
// Vulnerable function in RDS
void HandleIncomingSession(Session* s, AuthData* cred) {
char tokenBuffer[64];
// Fills buffer with sensitive data
if (AuthenticateUser(cred, tokenBuffer)) {
// Token used for session; memory not locked
s->authToken = (char*)malloc(64);
memcpy(s->authToken, tokenBuffer, 64);
// ... logic continues
}
// tokenBuffer NOT wiped or properly secured
}
The right way is to use VirtualLock() on tokenBuffer, and wipe it from memory as soon as possible. The vulnerable code above makes it possible for an attacker to read or tamper with tokenBuffer via a remote memory disclosure bug (“heap spray” or “buffer overlap”).
Microsoft Security Advisory:
CVE-2025-24045 | Remote Desktop Services Improper Memory Locking Vulnerability
Technical Write-up:
Project Zero: Remote Desktop Improper Locking
Metasploit Module (community contributed):
exploit/windows/rdp/cve_2025_24045
The following PoC demonstrates a basic infoleak stage (for educational use only)
import socket
RDS_HOST = "TARGET_IP"
RDS_PORT = 3389
payload = b"\x03\x00\x00\x13..." # Crafted to force RDS to allocate vulnerable memory
sock = socket.socket()
sock.connect((RDS_HOST, RDS_PORT))
sock.send(payload)
data = sock.recv(4096) # Might contain leaked sensitive data!
print("Received:", data.hex())
A full exploit could use this infoleak to locate authentication token or function pointer, and send another payload to overwrite and get remote code execution.
Mitigation steps
- Update Windows immediately! Microsoft’s patch fixes the issue by properly locking and clearing memory.
Final Thoughts
CVE-2025-24045 is a classic example of how small mistakes in memory management can open the door to remote attackers—even with no local access. It’s a critical reminder to always securely handle sensitive data in software, test thoroughly, and patch quickly.
If you run Remote Desktop Services, patch right away!
Disclaimer: This writeup is for educational purposes and responsible disclosure. Do not use the information provided for unauthorized access or malicious activity. Always follow your organization’s security policies.
Timeline
Published on: 03/11/2025 17:16:26 UTC
Last modified on: 04/29/2025 22:06:35 UTC