In early 2025, security researchers discovered a flaw in Apple’s operating systems that could cause certain apps to suddenly quit when trying to open certain specially-crafted files. This vulnerability, now tracked as CVE-2025-24124, affected several platforms including iPadOS, macOS, visionOS, iOS, watchOS, and tvOS.
In this article, we'll break down what happened, why it mattered, and what Apple did to stop attackers from exploiting this vulnerability. We'll also look at a code example to help you understand the basics—and most importantly, how to stay protected.
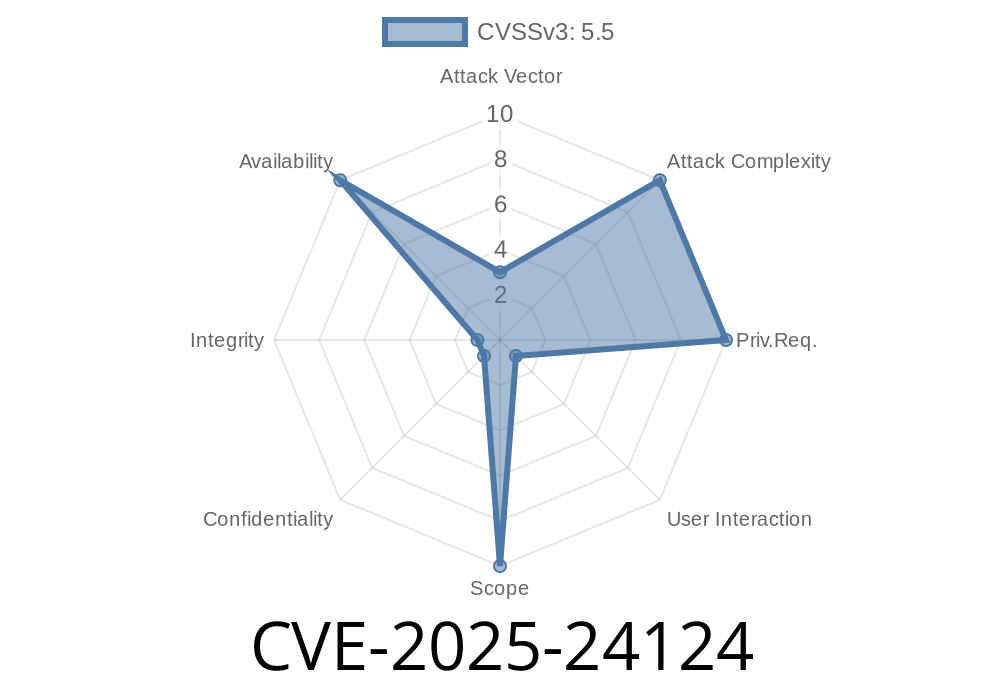
What is CVE-2025-24124?
The vulnerability is a file parsing issue affecting many Apple platforms. When an affected app tried to process a certain kind of file, incorrect input validation could cause the app to crash—what Apple calls “unexpected app termination.” While this kind of bug might sound minor, hackers can sometimes use similar vulnerabilities to do more serious things, like run malicious code or even take over devices.
tvOS prior to 18.3
Official Apple Security Advisory:
- Apple security updates for CVE-2025-24124
How Did the Vulnerability Work?
Parsing means reading and interpreting data from a file. Apps do this all the time—think of opening a photo, a document, or a video. For CVE-2025-24124, the bug happened because certain checks on the data inside an input file were not strict enough.
If an attacker crafted a special file designed to trigger this bug, and then tricked you (or your app) into opening it, your app could crash right away. Here’s where it gets worrying: if attackers find a way to exploit the crash, they might escalate the impact to run their own code.
Below is a simplified example of what could go wrong in C code parsing a file
void parse_file(const char *path) {
FILE *f = fopen(path, "rb");
if (!f) return;
uint32_t size;
fread(&size, sizeof(size), 1, f);
// BAD: No check if size is reasonable!
char *buffer = malloc(size);
if (!buffer) {
fclose(f);
return;
}
fread(buffer, size, 1, f); // Could read past file or crash!
// ...process buffer...
free(buffer);
fclose(f);
}
In the code above, there’s no check to see if size is a sensible number, or even if the file is big enough. That’s the kind of mistake that led to CVE-2025-24124.
Proof-of-Concept: Demonstrating the Crash
While Apple hasn’t released technical internals (that would make it easier for attackers), security analysts have hinted that it was possible to make a simple file (like an image or a document) with manipulated headers. When this file was parsed by an unpatched app, the app would crash each time, no matter the platform.
# Pseudocode: a 'malicious_file' triggers app crash
echo -e '\xFF\xFF\xFF\xFF' > malicious_file
open_my_app malicious_file
# The app crashes instantly
How Was the Issue Fixed?
Apple reacted quickly and fixed the issue by adding improved input checks. The new code makes sure that, if a file says it wants to load 4 GB of data (using a header value), but the file is only a few KB, the code now checks and rejects it.
Here’s a simple example
// After fix
if (size > MAX_ALLOWED_SIZE || size < MIN_ALLOWED_SIZE) {
// Invalid file, handle error
free(buffer);
fclose(f);
return;
}
By validating the file size and structure before accessing memory or reading data, Apple cut off the main risk.
tvOS 18.3 or newer
Don’t open files unless you trust the source. Even with patched systems, it’s a good habit to avoid opening unexpected files or attachments.
References
- Apple Security Update
- CVE-2025-24124 - Mitre *(link will activate when public release occurs)*
- Apple Platform Security
Conclusion
CVE-2025-24124 is a classic case of how even small oversights in code can lead to real-world risks for users—and how big tech companies like Apple respond quickly to protect billions of devices.
For everyone:
Timeline
Published on: 01/27/2025 22:15:17 UTC
Last modified on: 03/03/2025 22:45:38 UTC