Google Chrome has always been one of the most popular web browsers, but with popularity comes attention from attackers. Recently, a critical “use-after-free” vulnerability (CVE-2025-2476) was found and responsibly patched in the Lens component of Google Chrome. The flaw allowed attackers to remotely exploit heap memory, opening the door for code execution and potential full system compromise—with nothing but a crafted web page.
In this post, we’ll break down what happened, how the exploit works, and point out references for you to dive deeper.
What is CVE-2025-2476?
CVE-2025-2476 is a _use-after-free (UAF)_ vulnerability in the Lens component of Google Chrome versions prior to 134..6998.117. Simply put, UAF bugs happen when a program frees some memory but then keeps using it—like throwing away your house keys, and then trying to get back inside and accidentally letting someone else take your place.
Here, with just a malicious HTML page, a remote attacker could trick Chrome into accessing memory that’s already been freed (and possibly rewritten by the attacker), leading to arbitrary code execution.
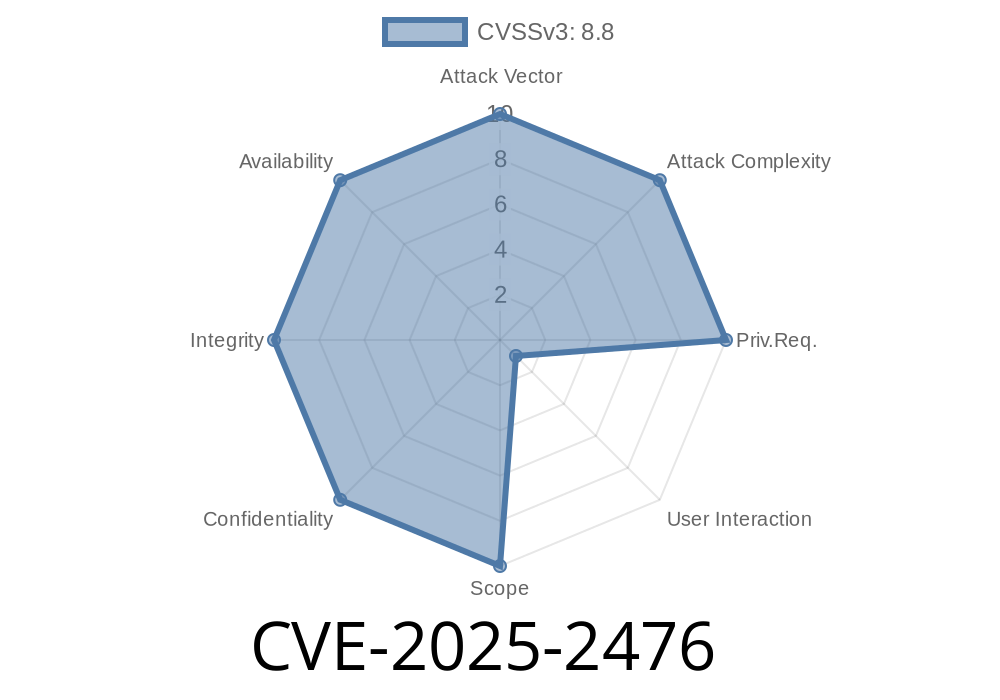
Severity:
Technical Summary
The Lens component, introduced to allow users to visually search parts of web pages and images, interacts deeply with page DOM. In some scenarios, attacker-controlled manipulation of page structures or event sequences could free a chunk of memory (say, an image or DOM node used by Lens), but Lens code would later try to access it as if it was still valid.
A sophisticated attacker could arrange for Chrome to read or write to this memory after it has been freed. If the attacker can fill this memory space with controlled data (a heap-spray), they can hijack execution flow and run arbitrary code.
Proof of Concept (PoC) [Simplified]
Let’s look at a simplified PoC (actual attack chains can be more complex). This snippet is just for educational purposes and shows the general logic behind a use-after-free trigger in the browser.
<!DOCTYPE html>
<html>
<body>
<img id="target" src="victim.jpg">
<script>
function triggerUAF() {
let img = document.getElementById('target');
// Remove image from DOM, triggering free in Lens
img.parentNode.removeChild(img);
// Force garbage collection (not reliable in real life, but shown for concept)
for (var i = ; i < 10000; i++) {
new Array(100000).fill();
}
// Access Lens-specific feature that might use dangling pointer
// For illustration – actual path depends on attacker's research
navigator.lensSearch(img); // Non-existent, conceptual call
}
setTimeout(triggerUAF, 100);
</script>
</body>
</html>
In the real world, attackers would reverse engineer the browser to find exactly which API calls and event orderings would leave Lens with a use-after-free pointer, then heap-spray malicious “fake” objects.
Discovery: Earlier this year by security researcher(s)
- Patched in: Chrome 134..6998.117 (Release notes)
Exploitation Steps
1. Crafted HTML page: Attacker lures or tricks user into accessing a website with malicious JavaScript and DOM structure.
Trigger UAF: The script forces an object used by Lens to be freed and then re-used.
3. Heap Spray: The attacker fills browser memory with their controlled data, in hopes the freed memory will now point into their payload.
4. Hijack Execution: The browser executes attacker’s code, possibly allowing full compromise of system or user data.
Potentially escape browser sandbox (in chained exploits)
You don’t have to click anything but a website link.
Protection: What Should You Do?
- Update Chrome immediately: Visit [chrome://settings/help](chrome://settings/help) to force an update.
- Watch for updates in other Chromium-based browsers: Edge, Brave, Opera, and others often follow Chrome’s patching cadence.
Chromium security advisory:
chromereleases.googleblog.com/2024/06/stable-channel-update-for-desktop_17.html
CVE entry:
cve.org/CVERecord?id=CVE-2025-2476 *(may be updated as sync completes)*
Chromium security overview:
chromium.org/Home/chromium-security/
Summary
CVE-2025-2476 is a reminder that even the most advanced browsers like Chrome can have deep-seated bugs in new features like Lens. Use-after-free vulnerabilities are among the most dangerous class of bugs, as they frequently lead to reliable exploits. Always keep your browser up to date, and if you develop browser features, audit for lifetime issues especially when dealing with complex features that interact with DOM and memory.
Timeline
Published on: 03/19/2025 19:15:50 UTC
Last modified on: 03/24/2025 15:15:16 UTC