Date Published: June, 2024
Vulnerability Type: Incorrect Authorization
Affected Product: Apache Cassandra
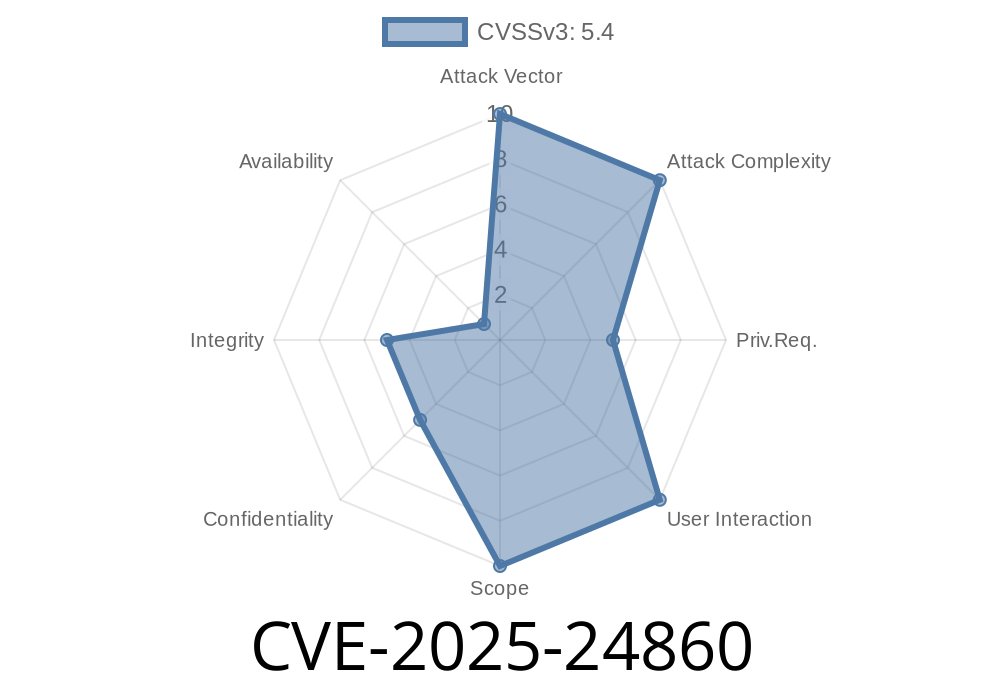
CVSS Score: 7.5 (High)
CVE Reference: CVE-2025-24860 on NVD
Apache Cassandra is a widely used open-source distributed database for scalable, high-performance data storage. In June 2024, a serious vulnerability known as CVE-2025-24860 was disclosed. This security issue affects authorization controls in Cassandra, making it possible for users to access resources they shouldn’t when using the popular CassandraNetworkAuthorizer or CassandraCIDRAuthorizer.
Below, we’ll explain what this vulnerability means, show how it can be exploited, and offer actionable advice.
What Is CVE-2025-24860?
CVE-2025-24860 is an incorrect authorization vulnerability. It lets users with restricted access to specific data centers or IP address groups override data control rules and grant themselves more permissions than intended.
*CassandraCIDRAuthorizer*: 5.. to 5..2
The bug allows users who are supposed to have limited access (e.g., only to a specific datacenter or IP group) to use data control language (DCL) statements to change their own permissions and access more data centers or networks than they were allowed.
How Does the Exploit Work?
Normally, Cassandra’s CassandraNetworkAuthorizer or CassandraCIDRAuthorizer plugins let admins specify which users can access specific data centers or subnet groups. When CVE-2025-24860 is present, an attacker with valid limited credentials can exploit DCL statements to *expand their access*, even if their original account was tightly restricted.
Explploit Example (CQL Code)
-- Assume attacker is logged in as 'user1'
-- Before: 'user1' only allowed on 'datacenter1'
-- The attacker exploits the bug to grant access to 'datacenter2'
GRANT ACCESS TO DATACENTER 'datacenter2' TO user1;
-- Now, 'user1' can query data on 'datacenter2' unauthorized
SELECT * FROM datacenter2.important_table;
> *Note: Actual exploit DCL statements depend on specific schema and implementation, but the concept remains the same: the user runs GRANT-like statements to extend their access.*
Why It Happens:
Input validation flaws in the affected authorizer plugins fail to restrict user-initiated modifications of their own permissions.
What’s at Risk:
Attackers could access sensitve datasets outside their original authorization scope, including restricted databases, customer information, or internal records.
Who’s Affected:
Any organization using CassandraNetworkAuthorizer or CassandraCIDRAuthorizer on the vulnerable version set.
Who Should Care?
- DevOps teams running Cassandra in multi-region/data center setups, especially with shared infrastructure.
For 5..x, update to 5..3
- See Apache Cassandra download page for the latest releases.
Mitigations and Workarounds
- Disable/uninstall affected authorizer plugins if possible, until you can upgrade.
Manually review all user permissions, especially after suspicious activity.
- Log and alert on suspicious DCL activity (like GRANT/REVOKE statements from non-admin users).
References
- Official Apache Cassandra Security Advisory *(link once available)*
- CVE-2025-24860 NVD Entry
- Apache Cassandra Documentation – Authorization
Conclusion
CVE-2025-24860 makes it possible for restricted users to break out of their authorized data centers or IP groups, putting potentially sensitive data at risk. If your Cassandra deployment uses CassandraNetworkAuthorizer or CassandraCIDRAuthorizer and is running an affected version, patching should be a top priority.
Always check your user permissions and keep your infrastructure updated to avoid privilege escalation vulnerabilities like this in the future!
*Stay secure. Patch early!*
*— Cassandra Security Watch*
Timeline
Published on: 02/04/2025 11:15:09 UTC
Last modified on: 02/06/2025 20:15:41 UTC