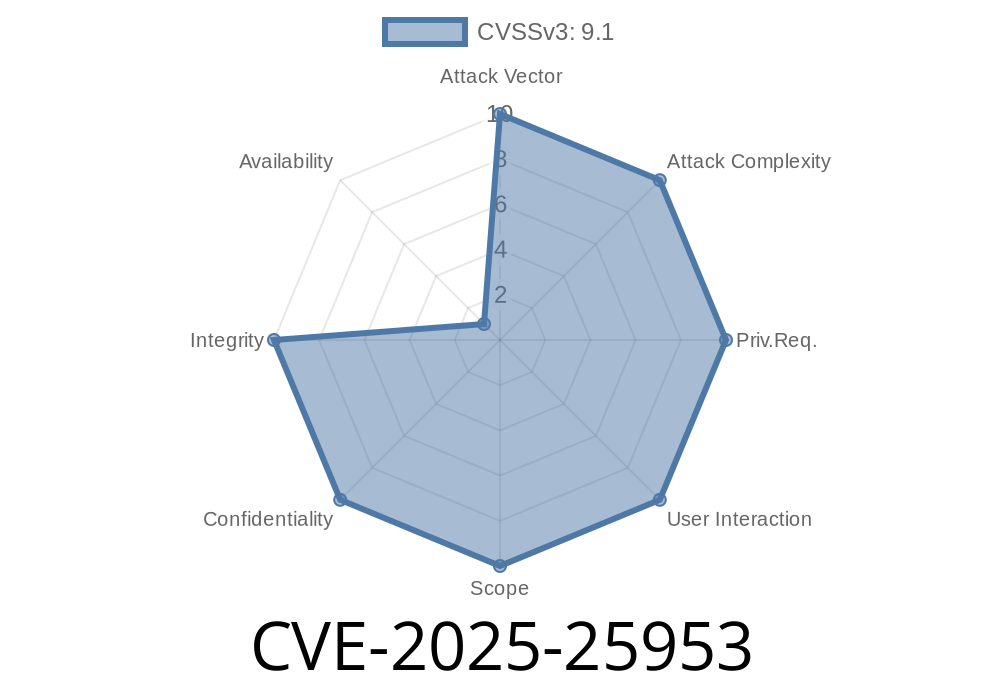
In early 2025, a critical security flaw labeled CVE-2025-25953 was discovered in the Serosoft Solutions Pvt Ltd Academia Student Information System (SIS) EagleR v1..118. This vulnerability exposes Azure JWT access tokens, potentially allowing attackers to escalate their privileges and gain access to sensitive student and administrative data.
In this long read, we'll discuss what this vulnerability is, how it was discovered, provide a simplified code snippet to illustrate the problem, detail its exploit, and offer remediation steps. For context and technical reference, links to official sources are provided.
What Is CVE-2025-25953?
An Azure JWT access token gives applications permission to access Microsoft services (like Office 365, Azure resources, etc.) on behalf of a user. If such tokens are accidentally leaked, any attacker possessing one can impersonate that user, bypassing regular login checks.
Researchers found that in version 1..118 of the Academia SIS (EagleR), certain API responses and log files were exposing these highly sensitive Discord tokens. Anyone already logged in (i.e., with basic access) could exploit this exposure to move laterally in the system or escalate their privileges towards admin.
How Was The Vulnerability Discovered?
The issue was initially flagged by a security researcher who noticed tokens appearing in unexpected places during API traffic analysis. By inspecting API calls and response payloads in the browser's developer tools, the researcher observed Azure JWT tokens being returned in plaintext.
The response payload looked something like this (simplified for clarity)
{
"status": "success",
"userRole": "user",
"azureToken": "eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9..."
}
Note: The real tokens are longer; the snippet above is just an example.
Privilege escalation: Attackers can craft requests posing as higher-privileged users.
- Sensitive info access: Student records, grades, personal addresses, and even payroll data may be accessed.
- Persistence & lateral movement: Attackers can leverage the token to create more tokens or gain access to connected services, thanks to Azure SSO (Single Sign-On) integration.
Since the SIS often integrates with broader campus resources, exposure of the JWT could lead to full campus-wide data compromise.
Here's a step-by-step guide to how one might exploit this bug (purely for educational purposes)
1. Authentication as a normal user:
Log in using a valid account (even a student account suffices).
2. Capture API traffic:
Open up your browser network tab or use a proxy tool like Burp Suite or OWASP ZAP.
3. Find the exposed token:
Monitor the API responses, especially those that return user data or session details. Look for properties like azureToken.
4. Extract the JWT:
Copy the value of "azureToken".
5. Decode and Analyze:
Tools such as jwt.io let you decode the token. You will see claims such as role: "admin" or role: "superuser" if the token was issued improperly.
6. Use the Token:
You can now use this token as a bearer token in further HTTP requests, such as
GET /api/admin/students
Authorization: Bearer <leaked JWT token>
If access control isn't enforced correctly, this grants full admin access.
Here's a Python example of using a leaked JWT token to access protected SIS endpoints
import requests
# Replace with the target SIS server and the leaked token
sis_url = 'https://sis.example.com/api/admin/students';
jwt_token = 'eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9...' # Leaked token
headers = {
'Authorization': f'Bearer {jwt_token}'
}
response = requests.get(sis_url, headers=headers)
print(response.json())
References
- NVD Entry for CVE-2025-25953 (may update soon)
- Serosoft Academia SIS Official Site
- JWT Best Security Practices
- Azure Token Security
Conclusion
CVE-2025-25953 underlines the real-world risks of poor token management in education technology. Institutions running unpatched Serosoft Academia EagleR v1..118 are *critically exposed* until a fix is applied. Immediate upgrade and audit are essential to avoid sensitive student data ending up in the wrong hands.
Stay vigilant and always keep your systems up to date!
*This post was written exclusively for educational purposes. Do not use this information to attack or compromise any systems without permission. Always disclose vulnerabilities responsibly to affected vendors.*
Timeline
Published on: 03/03/2025 01:15:11 UTC
Last modified on: 03/05/2025 17:15:15 UTC