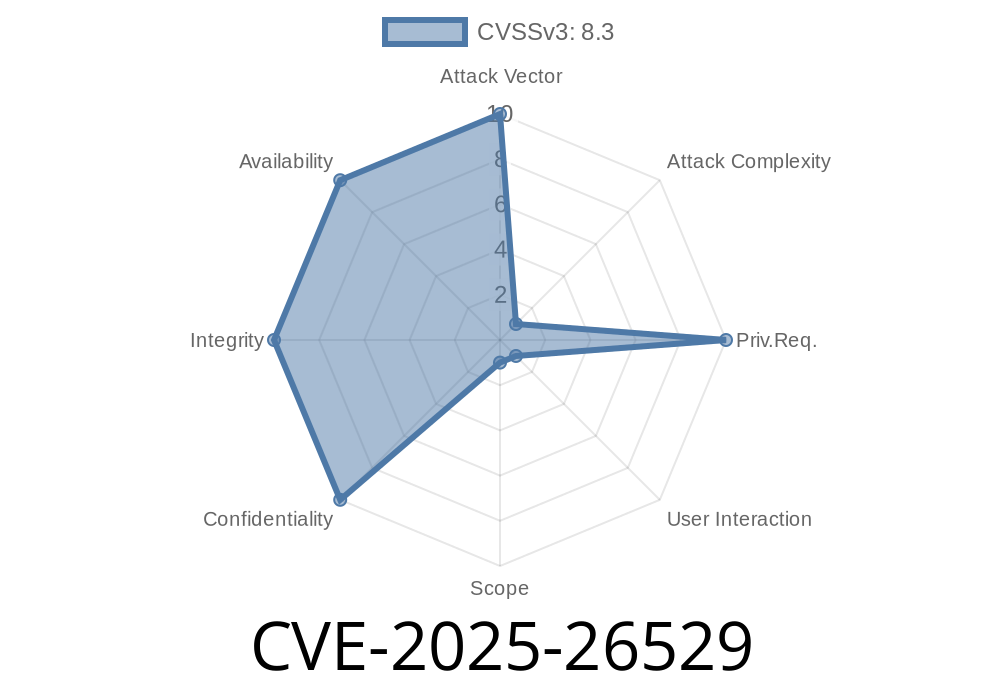
In early 2025, a new vulnerability named CVE-2025-26529 was discovered affecting various web-based applications with site administration panels. This vulnerability revealed that information displayed in the administration live log was not properly sanitized, opening the door for a dangerous type of cyber attack known as Stored Cross-Site Scripting (Stored XSS). In this post, we break down what CVE-2025-26529 is, how it works, why it matters, and how attackers can exploit it with simple examples.
What is Stored XSS?
A Stored XSS vulnerability (also known as persistent XSS) occurs when user input is saved by the server (in a database, log, or message), and then served to future users *without* proper sanitization. If this user input contains malicious scripts, any user viewing the data (say, an admin looking at a live log) could unwittingly run the attacker’s code in their browser.
This is especially dangerous when the targeted user is an administrator—attackers could steal cookies, perform actions on behalf of admins, or compromise the entire platform.
Description
The live log feature in the site administration panel displayed raw information derived from user activities. However, the data displayed—such as usernames, request details, or custom messages—was not sufficiently sanitized. This means that if a malicious user could control any part of the data ending up in the live log, they could inject scripts that would run in the browsers of admins viewing the log.
Example of the Vulnerability
To better understand, let’s say the web app logs unsuccessful login attempts, including the *username* that was attempted.
Code Snippet (Vulnerable)
// Pseudocode for vulnerable log entry
$log_entry = "Failed login attempt by " . $_POST['username'];
file_put_contents('admin_live_log.html', $log_entry, FILE_APPEND);
// Later, the admin panel shows this in HTML:
echo file_get_contents('admin_live_log.html');
Attacker Input
<script>alert('XSS');</script>
If this is submitted as the username, the script tag is stored in the log file. When an admin views the log page, the browser runs the script.
Result: Admin sees a popup (real attacks could do much worse).
1. Identify input fields that appear in logs
Typical fields are usernames, comment boxes, or custom headers.
2. Inject malicious scripts
Supply input like <script>...your code...</script>.
3. Wait for an admin to view the live log
Once stored, any admin that loads the live log page will unknowingly run the attacker’s script.
Safe Coding: How Should It Be Fixed?
Never trust any input before rendering it in HTML, even if it’s *internal* like log files!
Secure Code Example
// Use htmlspecialchars (PHP) or similar in other languages
$log_entry = "Failed login attempt by " . htmlspecialchars($_POST['username'], ENT_QUOTES, 'UTF-8');
file_put_contents('admin_live_log.html', $log_entry, FILE_APPEND);
// Or always escape before output:
echo htmlspecialchars(file_get_contents('admin_live_log.html'));
This change ensures any <, >, ", ', etc. are converted to their safe HTML equivalents, so scripts are shown as plain text rather than executed.
Apply patches: Developers should sanitize all log content before rendering.
- Audit logs: Check live logs for unexpected HTML/script.
References & Further Reading
- Official CVE-2025-26529 Entry (MITRE)
- OWASP XSS Cheat Sheet
- Vulnerability Postmortem Example (Similar Issue)
Conclusion
CVE-2025-26529 is a reminder that security must consider every surface—including “internal” admin tools. One unsanitized log can be all it takes for a devastating attack. Always escape user input, even in places you think are private, and stay up to date with software patches to protect your site.
Timeline
Published on: 02/24/2025 20:15:33 UTC