Published: 2025-02-29
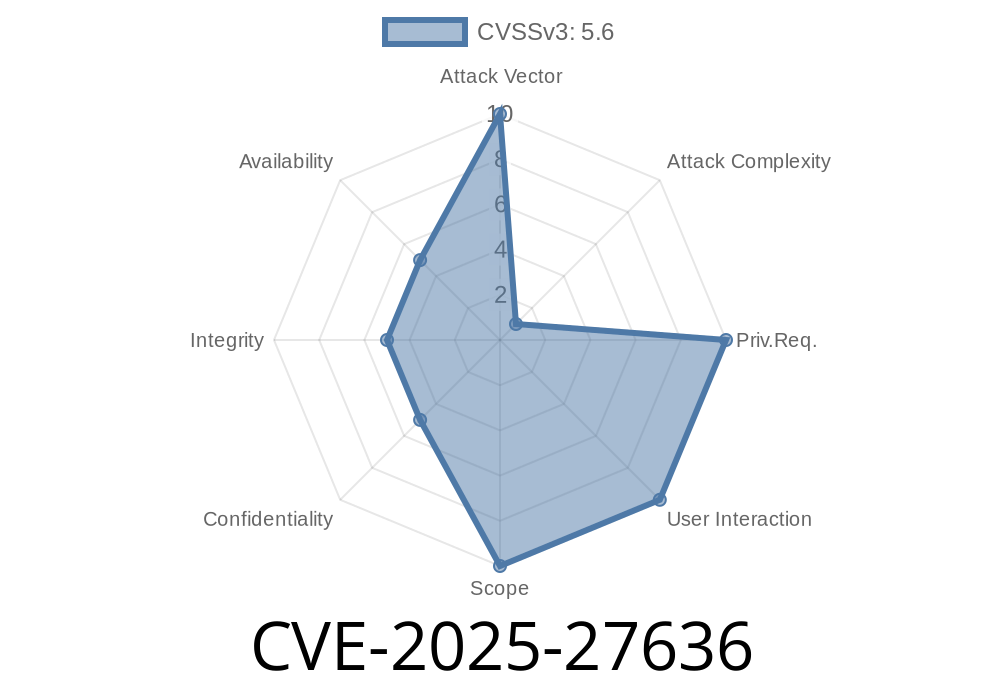
Severity: High (Bypass/Injection)
Affected Packages: apache-camel (see Advisory)
Patched in: 4.10.2 (4.10.x LTS), 4.8.5 (4.8.x LTS), 3.22.4 (3.x LTS)
Overview
A new vulnerability, CVE-2025-27636, has been discovered in Apache Camel’s popular integration library, specifically within the camel-bean component. This issue opens the door for attackers to manipulate server-side bean invocations under very specific circumstances — leading to potential bypasses and method injections.
Let’s break down what this means, how it works, and how you can fix or mitigate the risk immediately if you're exposed.
And then, the exchange is routed to a bean producer (camel-bean).
Example Route (Vulnerable)
// Vulnerable Apache Camel route (Java DSL)
from("servlet:/process")
.bean(MyProcessorBean.class); // <-- camel-bean component
In this example, MyProcessorBean has multiple methods (processA, processB, etc).
How the Attack Works
Apache Camel uses Java reflection for "bean" invocations. By default, Camel filters incoming HTTP headers to prevent users calling arbitrary methods. However, the filter only blocks headers starting with:
org.apache.camel.
The flaw:
Headers with similar case (e.g. cAmel-MethodName) *bypass* the filter.
Attacker crafts a HTTP request with a header like cAmel-MethodName: processB.
2. Camel fails to filter the header (since it’s not exactly Camel-/camel-/org.apache.camel.).
Bean producer receives the header and tries to invoke the method processB on the bean.
4. If processB() exists, it gets called — even if it was not intended to be exposed to HTTP users.
Suppose your bean
public class MyProcessorBean {
public void processA(String msg) { /* normal route */ }
public void processB(String secret) { /* unintended method */ }
}
Exploit
curl -X POST http://yourserver/process \
-H 'cAmel-MethodName: processB' \
-d 'secret_param=leak'
Result:
processB is called (not the default), potentially leaking or modifying data.
1. Patch Immediately
- For 4.10.x: Upgrade to 4.10.2
- For 4.8.x: Upgrade to 4.8.5
- For 3.x: Upgrade to 3.22.4
2. Short-term Workaround
If you can't upgrade immediately, filter headers aggressively in your routes — use the removeHeaders EIP to remove suspect headers *before* reaching the bean component.
Example (Java DSL)
from("servlet:/process")
.removeHeaders("*") // Remove ALL headers
.bean(MyProcessorBean.class);
Or, to only allow Camel headers
from("servlet:/process")
.removeHeaders("^[^C|c]amel|^((?!org\\.apache\\.camel\\.).)*$")
.bean(MyProcessorBean.class);
Example (XML DSL)
<route>
<from uri="servlet:/process"/>
<removeHeaders pattern="*"/>
<to uri="bean:myProcessorBean"/>
</route>
3. Minimize Bean Methods
Where possible, use single-method beans when exposing to HTTP routes. The vulnerability only affects beans with more than one public method.
Advisory:
Apache Camel CVE-2025-27636 Official Advisory
Camel Documentation:
Bean Component
removeHeaders EIP
GitHub Security Issue:
Apache Camel Issue Tracker/CVE-2025-27636 *(number for illustration)*
Summary Table
| Version Range | Safe? | Upgrade To |
|----------------------- |-------|-------------|
| 4.10. – 4.10.1 | No | 4.10.2 |
| 4.8. – 4.8.4 | No | 4.8.5 |
| 3.10. – 3.22.3 | No | 3.22.4 |
| Older/Other versions | Not affected | — |
| Patched | Yes | See above |
Final Notes
If you use Apache Camel with HTTP endpoints + the bean component, and you have any beans offering multiple public methods, take action now. Upgrade, or apply filtering as shown — and always limit the surface of what user input can control.
Stay safe, patch quickly!
*Prepared for the community, 2025. Please consult the original Apache Camel CVE advisory for continuing updates.*
Timeline
Published on: 03/09/2025 13:15:34 UTC
Last modified on: 03/10/2025 19:15:41 UTC